同态加密市场格局分析:数字隐私的下一个前沿
太长不看版:
零知识证明 (ZKP) 对于提高 web3 中的可扩展性和隐私性显然很有用,但由于依赖第三方处理未加密数据而受到阻碍。
完全同态加密(FHE)带来了突破,允许同时共享和单独的私有状态,而无需第三方信任要求。
FHE 可以直接对加密数据进行计算,从而支持暗池 AMM 和私人借贷池等应用程序,这些应用程序的全局状态信息永远不会被泄露。
好处包括无需信任的操作和加密数据上无需许可的链上状态转换,挑战集中在计算延迟和完整性方面。
新兴 FHE 加密货币领域的主要参与者专注于开发私有智能合约和用于扩展的专用硬件加速。
未来的 FHE 加密架构包括直接在以太坊上集成 FHE rollups 的潜力。
「以太坊生态系统中剩下的最大挑战之一是隐私(……),使用整套以太坊应用程序涉及将您生活的很大一部分公开,供任何人查看和分析。」—维塔利克
至少在过去的一年里,零知识证明(ZKP)一直是密码学领域的宠儿,但它也有其局限性。它们对于隐私、在不泄露信息的情况下证明信息知识以及可扩展性很有价值,特别是在 zk-rollups 中,但是,它们目前至少面临一些主要限制:
(1) 隐藏信息通常由受信任的第三方在链外存储和计算,限制了其他应用程序需要访问这些链外数据的无需许可的可组合性。这种服务器端证明类似于 web2 云计算之类的系统。
(2) 状态转换必须通过明文完成,这意味着用户必须信任那些拥有未加密数据的第三方证明者。
(3) ZKP 不适合需要了解共享私有状态才能生成有关本地私有状态的证明的应用。
然而,任何多人用例(例如暗池 AMM、私人借贷池)都需要链上共享私有状态,这意味着使用 ZK 需要某种中心化/链下协调器来实现共享私有状态,这使得它很麻烦并引入信任假设。
输入完全同态加密
完全同态加密 (FHE) 是一种加密方案,允许在无需事先解密的情况下对数据执行计算。它允许用户将明文加密为密文并发送给第三方处理它而无需解密。
这是什么意思?端到端加密。FHE 允许共享私有状态。
例如,在 AMM 中,去中心化做市商账户与每笔交易交互,但不属于任何单个用户。当有人将代币 A 交换为代币 B 时,他们必须了解共享做市商账户中两种代币的现有金额,以生成交换详细信息的有效证明。然而,如果全局状态通过 ZKP 方案隐藏,则生成该证明将不再可行。相反,如果全局状态信息可公开访问,则其他用户可以推断有关个人交换的细节。
使用 FHE,理论上可以隐藏共享状态和个人状态,因为可以通过加密数据计算证明。
除了 FHE 之外,实现隐私圣杯的另一个关键技术是多方计算(MPC),它解决了对私有输入进行计算的问题,并且仅公开这些计算的结果,同时保留了输入的机密性。但是,我们将其留待另一次讨论。我们这里的重点是 FHE——它的优点和缺点、当前市场和用例。
值得注意的是,FHE 仍处于开发早期,这不是 FHE 与 ZKP 或 FHE 与 MPC 的部落主义问题,而是与当前可用技术相结合时解锁的附加功能。例如,注重隐私的区块链可以使用 FHE 来启用机密智能合约,使用 MPC 在验证器之间分发解密密钥的分片,并使用 ZKP 来验证 FHE 计算的完整性。
优点和缺点
此时:FHE 的好处包括:
1. 没有第三方信任要求。数据可以在不受信任的环境中保持安全和私密。
2. 通过共享私有状态的可组合性。
3. 数据可用性,同时维护数据隐私。
4. (环)LWE的量子电阻。
5. 能够无需许可地在加密数据之上进行链上状态转换。
6. 不需要像英特尔 SGX这样容易受到旁道攻击的硬件和集中式供应链。
7. 在完全同态 EVM (fhEVM) 的背景下,无需学习执行重复的数学乘法(例如,多标量乘法)或使用不熟悉的 ZK 工具。
其缺点包括:
潜伏。计算密集型意味着大多数方案目前对于计算量大的应用程序在商业上不可行。值得注意的是,鉴于硬件加速正在积极开发中,这是一个短期瓶颈,并且此时 Zama 的 fhEVM 已经可以在每月约 2000 美元的硬件上实现约 2 TPS。
准确性问题。FHE 方案需要噪声管理以防止密文无效或损坏。然而, TFHE更准确,因为它不需要近似(与某些操作的CKKS不同)。
早期的。在 web3 领域推出的可投入生产的 FHE 项目非常少,这意味着需要进行大量的战斗测试。
市场概况
当前的 FHE x 加密货币格局
强调
Zama为加密和非加密用例提供了一系列开源 FHE 工具。其 fhEVM 库支持私有智能合约,保证链上机密性和可组合性。
Fhenix利用 Zama 的 fhEVM 库来实现端到端加密汇总。他们的目标是简化将 FHE 集成到任何 EVM 智能合约中的过程,只需对现有合约进行最少的修改。创始团队由 Secret Network 创始人和英特尔前 FHE bizdev 负责人组成。Fhenix 最近筹集了 700 万美元的种子资金。
Inco Network是一个由 FHE 驱动、兼容 EVM 的 L1,通过集成 Zama 的 fhEVM 加密技术,将加密数据的计算引入到智能合约中。创始人 Remi Gai 是 Parallel Finance 的创始成员之一,并与几位 Cosmos 工程师一起实现了这一愿景。
硬件。一些实体正在构建硬件加速来解决延迟问题。值得注意的是,Intel、Cornami、Fabric、Optaanalysis、KU Leuven、Niobium、Chain Reaction和一些 ZK ASIC/FPGA 团队。大约三年前,DARPA 授予基于 ASIC 的 FHE 加速拨款,推动了这一发展的激增。也就是说,对于某些 GPU 可能达到 20+ TPS 的区块链应用程序来说,这种专门的硬件加速可能不是必需的。FHE ASIC 可以将性能提高到 100+ TPS,同时大幅降低验证器的运营成本。
值得注意的提及。谷歌、英特尔、OpenFHE 都为 FHE 的整体进步做出了重大贡献,只是在加密领域的具体程度不那么具体。
用例
关键优势是实现共享私有状态和个人私有状态。这是什么意思?
私有智能合约:传统的区块链架构将用户数据暴露在 web3 应用程序中。每个用户的资产和交易对其他每个用户都是可见的。这对于信任和可审计性很有用,但也是企业采用的主要障碍。许多企业不愿意或干脆拒绝公开这些信息。FHE 改变了这一点。
除了端到端加密交易之外,FHE 还支持加密内存池、加密区块和机密状态转换。
这解锁了各种新颖的用例:
DeFi:暗池,通过加密内存池、无法追踪的钱包和机密支付(例如链上组织的员工工资)消除恶意 MEV。
游戏:加密状态多人策略游戏,支持各种新的游戏机制,如秘密联盟、资源隐藏、破坏、间谍、虚张声势等。
DAO:私人投票。
DID:在链上加密信用评分和其他标识符。
数据:合规的链上数据管理。
那么 FHE 加密架构的未来会是什么样子呢?
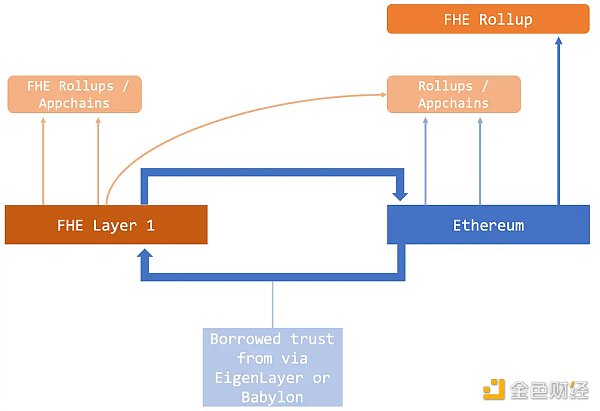
我们应该详细阐述三个核心组件:
第 1 层:该层是开发人员 (a) 在网络上本地启动应用程序或 (b) 与现有以太坊生态系统(输入输出模型)接口的基础,包括以太坊主网及其 L2s/侧链。
L1 的灵活性在这里是关键,因为它迎合了寻求具有 FHE 功能的本机平台的新项目,同时也适应了更愿意保留在当前链上的现有应用程序。
汇总/应用程序链:应用程序可以在这些启用 FHE 的 L1 之上启动自己的汇总或应用程序链。为此,Zama致力于fhEVM L1 的乐观堆栈和 ZK FHE 汇总堆栈,以扩展注重隐私的解决方案。
以太坊上的 FHE Rollup:在以太坊上启动 FHE Rollup 本身可以显着增强以太坊上的本地隐私,但面临一些技术挑战:
数据存储成本:即使明文条目很小,FHE 密文数据也相当大(每个 8 kb 以上)。出于数据可用性(DA)目的在以太坊上存储如此大量的数据在汽油费方面将非常昂贵。
定序器集中化:集中式定序器排序交易并控制全局 FHE 密钥是一个主要的隐私和安全问题,它首先违背了 fhEVM 的目的。虽然 MPC 是分散控制全局 FHE 密钥的潜在解决方案,但维护多方网络来执行计算会增加运营成本并导致潜在的低效率。
生成有效的 ZKP:为 FHE 操作生成 ZKP 是一项仍在开发中的复杂任务。虽然像Sunscreen这样的公司正在取得进展,但这种技术可能还需要几年的时间才能广泛用于商业用途。
EVM 集成: FHE 操作需要作为预编译合并到 EVM 中,因此需要对涉及计算开销和安全问题的多个问题的网络范围升级进行共识投票。
验证器硬件要求:以太坊验证器需要升级硬件才能运行FHE 库,这引发了对中心化和成本的担忧。
我们预计 FHE 最初将在流动性较低的环境和隐私至关重要的特定领域找到自己的定位。最终,随着吞吐量的增加,FHE L1 上可能会出现更深的流动性。从长远来看,一旦上述问题得到解决,我们可能会在以太坊上看到 FHE rollup,它可以更顺畅地利用主网的流动性和用户。现在的挑战在于找到 FHE 的杀手级用例、保持合规性并将可立即投入生产的技术推向市场。
与此同时,任何想要亲自动手或通过赏金狩猎赚钱的开发者都可以尝试Fherma的 FHE 挑战,并获得几项 4 位数的赏金。
致谢:非常感谢 Gurgen Arakelov(Yasha Labs/Fherma 创始人)、Rand Hindi(Zama 创始人)、Remi Gai(Inco Network 创始人)和Hiroki Kotabe(Inception Capital 研究负责人)对此做出的贡献文章。
Original title The original author is too long to read the version. Zero-knowledge proof is obviously useful for improving scalability and privacy, but it is hindered by relying on a third party to process unencrypted data. Full homomorphic encryption has brought a breakthrough, allowing simultaneous sharing and separate private state without third-party trust requirements, and can directly calculate encrypted data to support applications such as dark pools and private lending pools. The benefits of these applications include no need to trust. The challenge of unlicensed state transition on operating and encrypting data focuses on computing delay and integrity. The main participants in the emerging cryptocurrency field focus on developing private smart contracts and specialized hardware for expansion to accelerate the future encryption architecture, including the potential of direct integration on the Ethereum. One of the biggest challenges left in the Ethereum ecosystem is privacy. Using a complete set of Ethereum applications involves exposing a large part of your life to anyone for viewing and analyzing Vitalik. In the past year, zero-knowledge proof has always been the darling of cryptography, but it also has its limitations. They are very valuable for privacy to prove information knowledge and scalability without leaking information, especially in China, but at present they face at least some major limitations. Hidden information is usually stored and calculated by trusted third parties outside the chain, which limits the combination of other applications that need to access these off-chain data without permission. This server-side proof is similar to cloud computing. The system state transformation of classes must be completed in plain text, which means that users must trust those third-party certifiers who have unencrypted data, and it is not suitable for applications that need to know the shared private state to generate certificates about the local private state. However, any multi-user use case, such as the dark pool private lending pool, needs to share the private state on the chain, which means that the use requires some centralized coordinator under the chain to realize the shared private state, which makes it very troublesome and introduces the trust assumption that the input is completely homomorphic and encrypted. Homomorphic encryption is an encryption scheme that allows data to be calculated without prior decryption. It allows users to encrypt plaintext into ciphertext and send it to a third party to process it without decryption. What does this mean? End-to-end encryption allows sharing private state, such as decentralizing a market maker account to interact with each transaction, but it does not belong to any single user. When someone exchanges tokens for tokens, they must know the existing amounts of two kinds of tokens in the shared market maker account to generate exchange details. Effective proof of information, however, if the global state is hidden by the scheme, it will no longer be feasible to generate the proof. On the contrary, if the global state information is publicly accessible, other users can infer the details about personal exchange. In theory, the shared state and personal state can be hidden, because another key technology to realize the holy grail of privacy is multi-party calculation, which solves the problem of calculating private inputs and only discloses the results of these calculations while preserving them. We have left the confidentiality of the input, but we will leave it for another discussion. Our focus here is on its advantages and disadvantages. It is worth noting that the current market and use cases are still in the early stage of development. This is not a tribalism problem of AND or AND, but an additional function that is unlocked when combined with currently available technologies, such as a privacy-sensitive blockchain, which can be used to enable confidential smart contracts. The advantages and disadvantages of this time are verified by distributing pieces of decryption keys among verifiers. Including the fact that there is no third-party trust requirement, the data can remain safe and private in an untrusted environment. By sharing the combinability of private state and maintaining the quantum resistance of data privacy ring, the state transition on the chain can be carried out without permission on encrypted data. There is no need for hardware and centralized supply chain that are vulnerable to bypass attacks like Intel. Under the background of complete homomorphism, there is no need to learn to perform repeated mathematical multiplication such as multi-scalar multiplication or use unfamiliar tools Disadvantages include the intensive latent computation, which means that most schemes are not feasible in business for applications with a large amount of computation at present. It is worth noting that in view of the fact that hardware acceleration is being actively developed, this is a short-term bottleneck, and at this time, the problem of accuracy can be realized on hardware with a monthly cost of about US$. The scheme needs noise management to prevent ciphertext from being invalid or damaged, but it is more accurate because it does not need to be similar to some operations. Early projects that can be put into production in the field are very Less means a lot of battle testing. The current cryptocurrency pattern emphasizes providing a series of open source tools for encrypted and unencrypted use cases. Its library supports private smart contracts to ensure confidentiality and composability in the chain, and the library used to realize end-to-end encryption summary. Their goal is to simplify the process of integrating into any smart contract, and only need to make minimal changes to existing contracts. The founding team is composed of founders and former Intel leaders, and recently raised the seeds of million dollars. The fund is a driver-compatible one that introduces the calculation of encrypted data into the smart contract through integrated encryption technology. The founder is one of the founding members and has realized this vision with several engineers. Some entities are building hardware acceleration to solve the delay problem. It is worth noting that the grant of acceleration funds based on some teams about three years ago has promoted the surge of this development, that is to say, for some possible blockchain applications, this special hardware acceleration can Can it be necessary to improve the performance and greatly reduce the operating cost of the verifier? It is worth noting that Google and Intel have made great contributions to the overall progress, but the specific degree in the field of encryption is not so good. The key advantage of specific use cases is to realize shared private state and personal private state. What does this mean? The traditional blockchain architecture exposes user data in the application, and each user's assets and transactions are visible to every other user. Trust and auditability are very useful, but they are also the main obstacles for enterprises to adopt. Many enterprises are unwilling or simply refuse to disclose this information, which has changed this point. In addition to end-to-end encrypted transactions, they also support encrypted memory pools, encrypted blocks and confidential state transitions, which unlock various novel use cases. Dark pools can't track wallets and confidential payments through encrypted memory pools, such as eliminating malicious games and employees' salaries organized on the chain. Multi-player strategy games support various new game mechanisms, such as secret alliances, hiding resources, destroying spies' bluff, and other private votes. Encrypt credit scores and other identifiers on the chain, 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。

















