消失的芒果——MangoFarmSOL退出骗局始末
事件概览
MangoFarmSOL将自己定位为Solana网络上的质押协议,鼓励用户存入SOL而获得奖励。该项目曾承诺在1月10日进行空投而获得了Solana社区的关注。
然而,1月10日的承诺从未兑现。2024年1月6日,MangoFarmSOL就实施了退出骗局,从项目合约中转移了用户存入的13,512枚SOL(当时约126万美元),又部署恶意前段,误导用户授权“紧急迁移”并在此盗取约6万美元。这是我们在2024年至今发现的最大规模的退出骗局。
随后,MangoFarmSOL关闭了其社交账户和网站。
同之前我们报道的xKingdom事件一样,此次事件再次凸显了DeFi领域固有的退出骗局风险,强调了用户警惕意识与团队KYC的重要性。
骗局时间线
第一步:布下陷阱
① 1月3日,该项目利用社交媒体KOL的推广来提高其可信度并吸引更多用户。
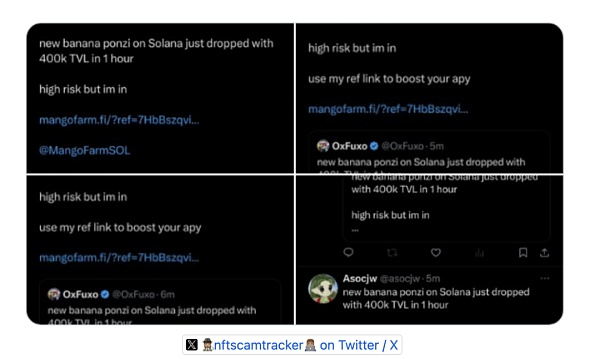
② 1月5日,该团队发表文章,声称将于1月10日空投MANGO代币,质押SOL以及推荐其他用户等行为均可获得更多奖励。
③ 1月3日至1月7日,用户开始将SOL存入MangoFarmSOL的合约中。受到MANGO代币空投承诺的诱惑,以及网络营销的影响,该协议的TVL超过了130万美元。

第二步:实施骗局
① 盗取合约资金:MangoFarmSOL团队发起骗局,将用户存入Mango合约内的13,514 SOL(约126万美元)提取到钱包8ggvi。

?第一笔交易:135枚SOL从Mango合约(Bfg5SM)转移到钱包8ggvi。
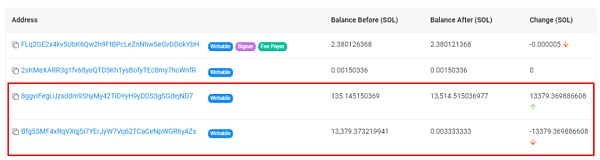
?第二笔交易:13,379枚SOL从Mango合约(Bfg5SM)转账至钱包8ggvi。
② 部署恶意前端再次行骗:随后,团队还借助先前被盗事件,以“紧急迁移”为幌子,部署了含有恶意代码的前端。该项目的官方社交媒体账户也发布了该恶意前端,诱骗用户进行交易,导致了约6万美元的额外资产被盗。
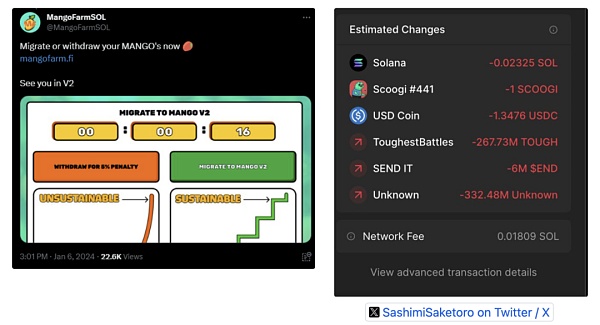
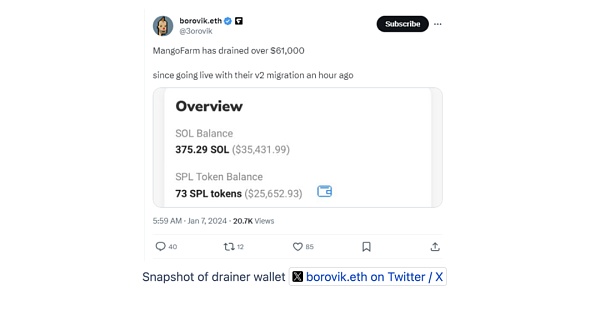
③ 彻底消失:MangoFarmSOL随后停用了其社交媒体账户并关闭了官方网站,并开始转移资金。
第三步:资金转移
Mango合约被盗资金流向
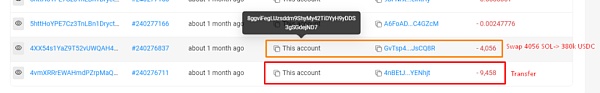
① 初始转移:Mango合约中总共有13.5K枚SOL,价值约126万美元,被盗后被发送到地址8ggvi.....ejND7。
② 混合&转换:接着,9,458枚SOL被发送到4nBETJ以混淆资金链路;8ggvi和4nBE中的所有SOL随后都被转换为USDC。
③ 跨链至以太坊:这些USDC经过Wormhole从Solana网络跨链到以太坊,并通过多次交易将这些USDC发送到4个不同的ETH地址。
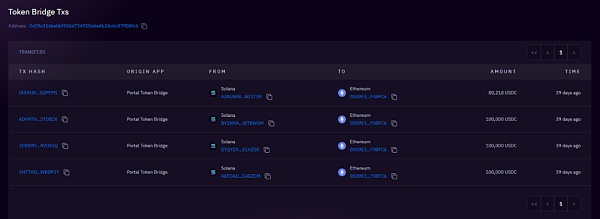
380k USDC经过4次交易跨链至0x09e3
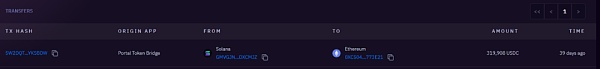
319k USDC跨链至0xc504
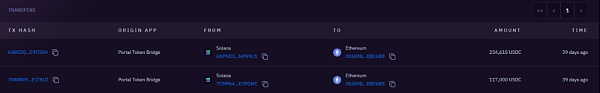
351k USDC跨链至0x6898
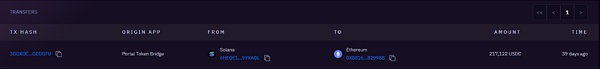
217k USDC跨链至0x8816
④ 最终清洗:进入以太坊网络后,USDC被换成ETH。然后,被盗资金通过Railgun(隐私混合器)进行清洗,并通过eXch(即时交换)进行交换,以进一步混淆资金。
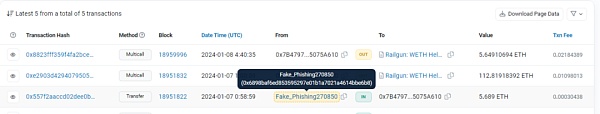
传输至Railgun的交易示例
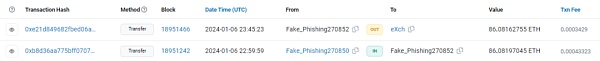
传输至eXch的交易示例
恶意前端盗取资金流向
① 整合与转换:通过恶意前端窃取的用户资产被整合为SOL,然后兑换成约5.86万美元的USDC。
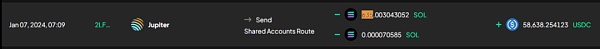
② 通过Allbridge跨链至以太坊:这些USDC在Allbridge经过2笔交易跨链到以太坊网络,地址为0x7ca.....d8fec。
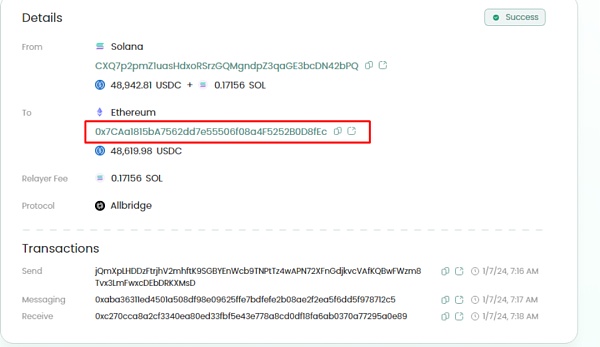
③ 最终清洗:桥接至以太坊的USDC被兑换为26枚ETH。随后,这些资金通过多次存入FixedFloat。
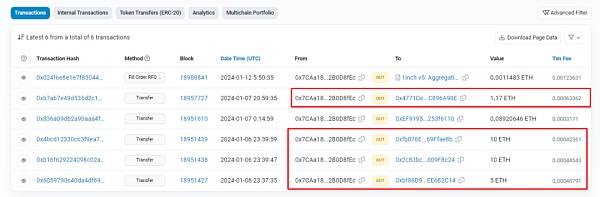
被盗资金最终分布
跨链到以太坊网络的被盗资金最终主要集中在三个地方:
eXch: 约292ETH
Railgun: 约263ETH
FixedFloat: 约26ETH
The event overview positioned itself as a pledge agreement on the network to encourage users to deposit and get rewards. The project promised to make an airdrop on, and gained the attention of the community. However, the promise of, was never fulfilled, and the withdrawal scam was implemented on, and the user's deposit was transferred from the project contract at that time, and a malicious front section was deployed to mislead the user to authorize an emergency relocation and steal about $10,000 here. This is the largest withdrawal scam we have discovered so far, and then its social account was closed. The website is the same as the incident we reported before. This incident once again highlights the inherent risk of exiting the scam in the field, emphasizing the user's vigilance and the importance of the team. The first step of the scam timeline is to lay a trap. The project uses the promotion of social media to improve its credibility and attract more users. The team published an article claiming that it will air-drop the token pledge and recommend other users to get more rewards. From March to March, users will start to receive empty tokens in their deposited contracts. The lure of investment commitment and the influence of online marketing, the agreement exceeded 10,000 US dollars. The second step was to implement a scam to steal contract funds. The team initiated a scam to withdraw about 10,000 US dollars deposited by the user into the wallet. The first transaction was transferred from the contract to the wallet, and the second transaction was transferred from the contract to the wallet to deploy malicious front-end fraud again. Subsequently, the team deployed the front-end with malicious code under the guise of emergency migration with the help of previous theft, and the official social media account of the project also released the evil. Italian front-end tricked users into trading, resulting in the theft of about 10,000 US dollars of additional assets, which disappeared completely. Then it stopped its social media account and closed its official website and began to transfer funds. Step 3: The stolen funds flowed to the initial transfer contract. A total of about 10,000 US dollars were stolen and then sent to the address mixed conversion. Then, all of them were converted into cross-chain to Ethereum, which crossed the chain from the network to Ethereum and passed many times. The transaction sends these to different addresses, and then the stolen funds are cleaned by privacy mixer and exchanged by instant exchange to further confuse the transactions to which the funds are transmitted. After a transaction, the address of the cross-chain to the Ethereum network was finally cleaned and the bridge to the Ethereum was converted into gold, and then these funds were deposited in stolen funds for many times and finally distributed. The stolen funds that crossed the chain to the Ethereum network were finally concentrated in three places. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
经验总结
MangoFarmSOL骗局是2024年迄今为止最大规模的退出骗局。该骗局的手法与2023年Harvest Keeper事件有相似之处。这两个项目在第一次盗窃发生之后又部署了恶意前端,进一步盗取用户资金。
MangoFarmSOL退出骗局预计造成了132万美元的损失,凸显了去中心化项目审查的迫切需要。
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。


















