空手套白狼 —— YIEDL 被黑分析
By: Sissice
背景
2024 年 4 月 24 日,据慢雾安全团队情报,BSC 链上的 YIEDL 项目遭攻击,攻击者获利约 30 万美元。慢雾安全团队对该攻击事件展开分析并将结果分享如下:
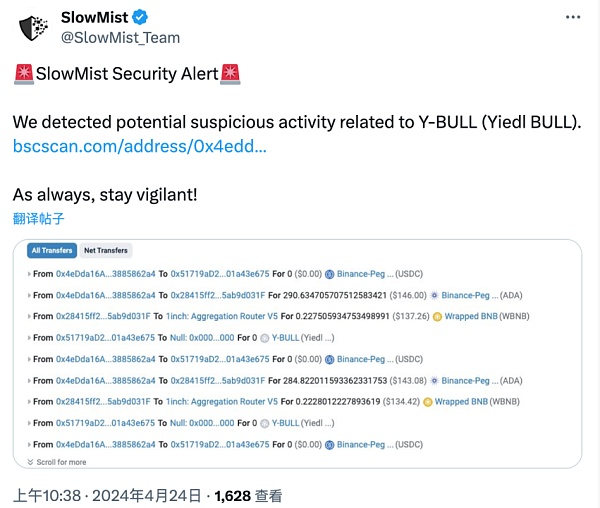
(https://twitter.com/SlowMist_Team/status/1782962346039898473)
相关信息
攻击者地址:
0x322696471792440499b1979e0a440491e870667a
被攻击合约地址:
0x4edda16ab4f4cc46b160abc42763ba63885862a4
部分攻击交易:
0x49ca5e188c538b4f2efb45552f13309cc0dd1f3592eee54decfc9da54620c2ec
0x3629ad588ac120163792e92b6c43bd4bdc5bf35cac66eb7f3a0267df93abc849
0x0a89b8670c40b4067b9522a5933c3bf8c44c968103aa642b04c65d49ad9e6457
0x5e468cba495e5f6165418fb9d87d824309c54261055425f33f588dd3b3abbcea
0x8710034dadecfc8c26f651c612f613fffdece6e2f9957b9ec8ab843218168c1d
0x9da398ed274c8cfa774b36003fa8c930d3430d0fc5889b5008830fd6463f68a9
0x2e3d4332f66a334e0170187011ed673dc222f95bf4443b618e08f8052437ef7a
0x5a15fdc57c35f2305aaa0bb95b109ad412b17406d737d137190fe5867393339d
0x8ef3765665cd849cdf9132ab37caf6aa0f891e1f7d9f418f86a6ab6ea38b6f5b
0xa9fa04b033afbed2218679aea92e9429a5f7839d0b4c65358ebf9ba20efcd021
攻击核心
本次事件的攻击核心是利用合约处理 redeem 函数调用时未能充分验证用户输入的外部参数。该参数是控制资产兑换的关键数据,通常包含特定的交易指令或路由信息。攻击者通过恶意构造这一外部参数,实现了未授权的���产转移。
交易分析
攻击者多次调用 redeem 函数,申请赎回数量为 0 的资产,此行为本身看似无害,因为赎回数量为零时通常不会触发任何实际的资金流动:
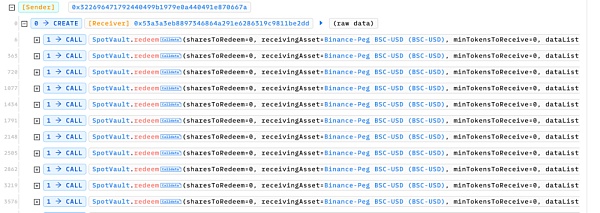
But following the redeem function reveals that the function will traverse the list of assets allowed by the contract, and if the current asset is not the asset the user wishes to receive, it will parse the dataList parameter and externally call the corresponding function in the 1inch Router. execute asset exchange operation.
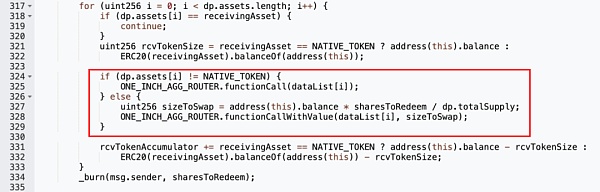
And because the dataList passed here is not checked and verified, it allows the attacker to construct malicious values to execute the unoswapTo function in the 1inch Router contract to perform arbitrary controllable token exchange operations.
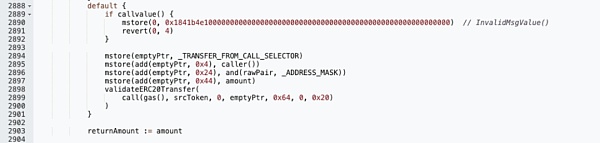
As a result, the WBNB-ADA Token in the Yiedl BULL contract was exchanged for BNB to the attacker's address.
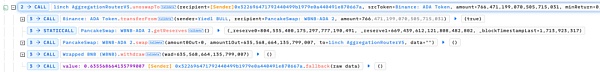
In this way, the attacker can trigger token exchange operations controlled by the dataList parameter without actually owning any redemption shares, without consuming its own assets, and profit from the contract funds multiple times.
总结
The core of this attack is that the function did not sufficiently verify the dataList parameter entered by the user, allowing the attacker to construct malicious external data and use 1inch to take away the tokens in the contract. Slow fog security team recommended that the project implement strict parameter verification mechanisms in development, especially when involving fund operations in the contract, to ensure that all external calls conform to expected behavioral norms, and thoroughly secure the logic of the contract. audit to avoid similar events from happening again.
Background: According to the information chain of the slow fog security team, the item was attacked, and the attacker made a profit of about 10,000 US dollars. The slow fog security team analyzed the attack event and shared the following related information: the attacker's address was attacked, the contract address was partially attacked, and the transaction attack core was attacked. The attack core of this incident was that the external parameters input by the user were not fully verified when the contract processing function was called. This parameter is the key data to control asset exchange. Usually, the attacker contains specific transaction instructions or routing information. By maliciously constructing this external parameter, the unauthorized transfer transaction analysis is realized. The attacker repeatedly calls the function to apply for the redemption of assets with a quantity of, which seems harmless in itself, because when the redemption quantity is zero, it usually does not trigger any actual capital flow summary. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。