任意地址欺骗攻击解析
背景
2023 年 12 月 5 日,Web3 基础开发平台 thirdweb 表示在预构建智能合约中发现了安全问题,所有使用预构建智能合约部署的 ERC20、ERC721、ERC1155 代币均受到了影响。(具体受影响的合约代码版本可以参考:https://blog.thirdweb.com/security-vulnerability/)
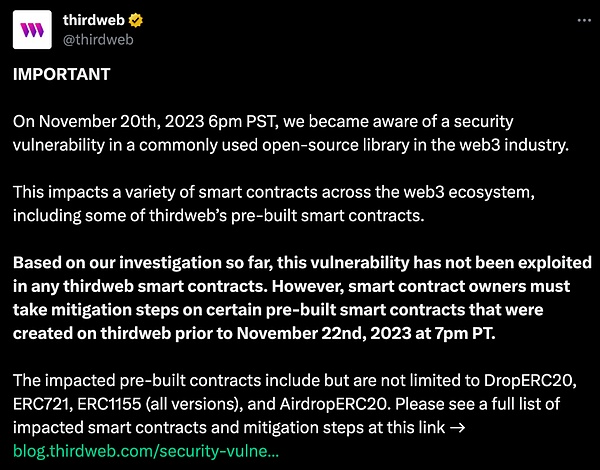
根据慢雾安全团队情报,在 2023 年 12 月 7 号,ETH 主网上的 Time 代币正是因为该漏洞遭受到攻击,攻击者获利约 19 万美金。目前仍有不少存在漏洞的代币合约正在被攻击,慢雾安全团队第一时间介入分析,并将结果分享如下:
前置知识
1. ERC-2771 是元交易的标准。用户可以将交易的执行委托给第三方 Forwarder,通常称为中继器或转发器。
通常合约中直接调用者的地址是使用 msg.sender 获取的,但在使用了 ERC-2771 的情况下,如果 msg.sender 是转发器角色的话,那么会截断传入的 calldata 并获取最后 20 个字节来作为交易的直接调用者地址。
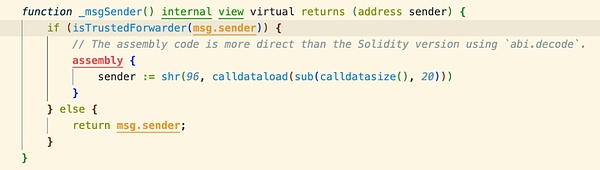
2. Multicall 是一个智能合约库,其作用是允许批量执行多个函数调用,从而减少交易成本。这个库通常用于优化 DApp 的性能和用户体验,特别是当需要进行多个读取操作时。
从代码中可以看到,thirdweb 项目存在漏洞的合约使用的 Multicall 库是通过循环调用 DelegateCall 函数来执行引用了该库的合约中的其他函数。
根本原因
漏洞的根本原因是代币合约同时使用了 ERC-2771 和 Multicall 库。攻击者通过 Forwarder 合约的 execute 函数调用代币合约的 multicall 函数,执行合约中的其他函数(如燃烧代币)。这种方式成功通过了 ERC-2771 的 isTrustedForwarder 判断,最终将函数的调用者解析为恶意 calldata 的最后 20 个字节。因此,攻击者成功欺骗了合约,使其误认为调用者是其他用户的地址,进而导致燃烧了其他用户的代币。
攻击步骤分析
此处以攻击交易 0xecdd11...f6b6 为例进行分析:
1. 攻击者首先用 5 个 WETH 在 Uniswap V2 池子中兑换成 345,539,9346 枚 Time 代币。
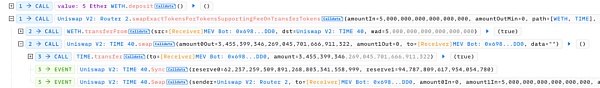
2. 接着调用 Forwarder 合约的 execute 函数,构造恶意的 data 去调用代币合约的 multicall 函数,此时代币合约会根据攻击者传入的恶意 data 去 delegateCall 执行代币合约的 burn 函数,燃烧掉池子地址中的 62,227,259,510 枚 Time 代币。
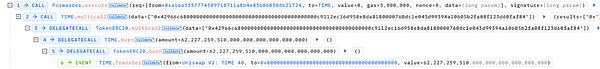
3. 由于上一步 burn 掉了池子中大量的 Time 代币,使得 Time 代币的价格被瞬间拉高,所以攻击者最后可以反向 swap 第一步获取的 Time 代币,掏空了池子中的 94 枚 WETH。

攻击原理剖析
在 Forward 合约的 execute 函数中,验证 req.from 的签名过后会用 call 交互 req.to(代币地址)。其中攻击者传入的 req.data 为
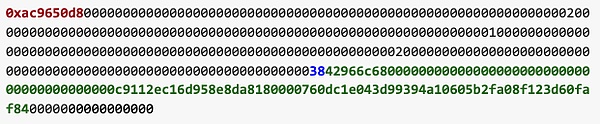
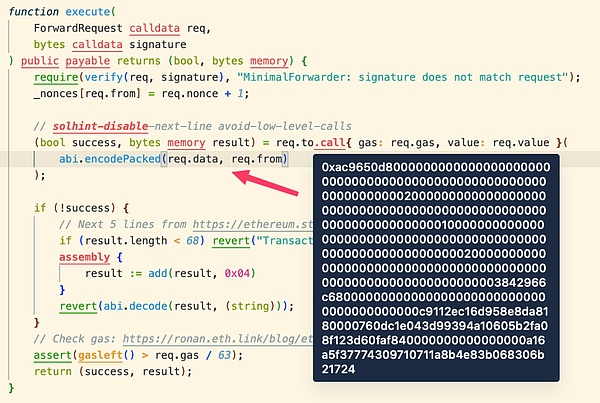
因为 0xac9650d8 为 multicall 函数的函数签名,故会调用代币合约的 multicall 函数,并且multicall 函数传入的 data 值为 0x42966c680000000000000000000000000000000000000000c9112ec16d958e8da8180000760dc1e043d99394a10605b2fa08f123d60faf84。
为什么传入 multicall 函数的 data 值中没有 req.from 呢?这是因为 EVM 底层处理 call 调用时会根据其中的偏移量而截断所需要的值,而攻击者传入的 calldata 值中设定偏移量是 38,数值长度为 1,所以刚好截取出来的 data 值是42966c680000000000000000000000000000000000000000c9112ec16d958e8da8180000760dc1e043d99394a10605b2fa08f123d60faf84。

具体可以参考 EVM opcode 中对 call 的描述(https://www.evm.codes/?fork=shanghai)。
由于 0x42966c68 为 burn 函数的函数签名,所以会根据攻击者构造的 data 值去 delegatecall 调用代币合约的 burn 函数。
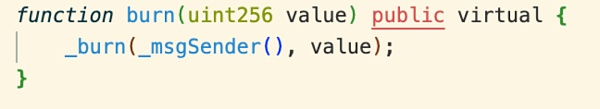
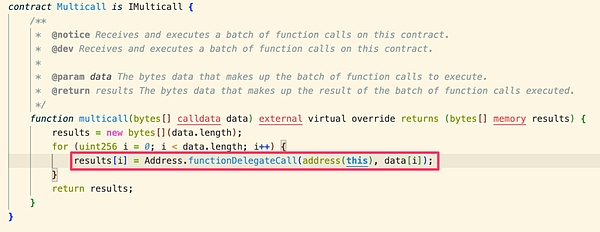
其中 _msgSender() 函数被 ERC-2771 库重写。
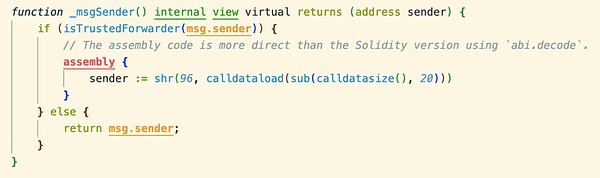
由于 multicall 是通过 delegatecall 进行调用的,所以 isTrustedForwarder 传入的 msg.sender 其实是 Forward 合约的地址,从而通过了判断,最终导致 _msgSender() 返回的值为传入的 calldata 的最后 20 个字节,即池子的地址 0x760dc1e043d99394a10605b2fa08f123d60faf84。
结论
本次攻击的根本原因在于合约同时引用了 Multicall 和 ERC2771Context,攻击者可以在转发请求中插入恶意 calldata,利用 Multicall 的 delegatecall 功能来通过受信任转发器的判断,并操纵子调用中 _msgSender() 的解析,从而可以操控任意用户的代币。
慢雾安全团队建议项目方在编写代币合约时,不要同时使用 Multicall 和 ERC2771Context,如果预期需求需要同时引用的话,则必须检查 calldata 长度是否符合预期或使用 openzeppelin 官方最新版本的 Multicall 和 ERC2771Context 合约。
参考
攻击者地址:0xfde0d1575ed8e06fbf36256bcdfa1f359281455a
攻击合约:0x6980a47bee930a4584b09ee79ebe46484fbdbdd0
相关攻击交易:https://etherscan.io/tx/0xecdd111a60debfadc6533de30fb7f55dc5ceed01dfadd30e4a7ebdb416d2f6b6
受影响的版本详情:https://blog.thirdweb.com/security-vulnerability/
缓解工具:https://mitigate.thirdweb.com
Background: The basic development platform indicated that security problems were found in the pre-built smart contracts, and all tokens deployed by using the pre-built smart contracts were affected. For the specific affected contract code version, please refer to the tokens on the main network of the month, according to the information of the slow fog security team. It is precisely because of this vulnerability that the attacker made a profit of about 10,000 US dollars. At present, many token contracts with vulnerabilities are still being attacked, and the slow fog security team immediately intervened and analyzed and shared the results as follows. Knowledge acquisition is the standard of meta-transaction. Users can entrust the execution of a transaction to a third party, usually called a repeater or a repeater. Usually, the address of the direct caller in the contract is obtained by using, but if it is used as a repeater role, it will truncate the incoming and obtain the last byte as the address of the direct caller of the transaction. It is an intelligent contract library whose function is to allow multiple function calls to be executed in batches, thus reducing the transaction cost. This library is usually used to optimize performance and users. Experience, especially when multiple reading operations are needed, it can be seen from the code that the library used in the contract with loopholes in the project is to execute other functions in the contract that refer to the library by calling functions circularly. The root cause of the loophole is that the token contract uses the judgment that the library attacker calls the functions of the token contract to execute other functions in the contract, such as burning tokens, and finally resolves the caller of the function as the last malicious one. Bytes, therefore, the attacker successfully deceived the contract and made it mistake the caller for the address of other users, which led to the burning of other users' tokens. Here, the attack transaction is analyzed as an example. The attacker first used a token exchanged in the pool and then called the function of the contract to construct a malicious function to call the token contract. At this time, the token contract will execute the function of the token contract according to the malice introduced by the attacker and burn the tokens in the pool address because the pool was dropped in the previous step. A large number of tokens in the child make the price of tokens rise instantly, so the attacker can finally reverse the tokens obtained in the first step and empty the coins in the pool. After analyzing the signature verified in the function of the contract, he will use the interactive token address, in which the attacker passes in the function of the token contract because he signed the function of the function, and the value passed in by the function is why it is not in the value passed in the function. This is because the underlying processing calls will truncate the needs according to the offset. The key value and the offset set in the value passed in by the attacker is a numerical value, so the value just intercepted is specific. You can refer to the description in. Because the function of the function is signed, the function of the token contract will be called according to the value constructed by the attacker, in which the function is rewritten by the library, so the address of the contract is actually passed, which finally leads to the judgment that the returned value is the last byte passed in, that is, the address of the pool. Conclusion The root cause of this attack lies in At the same time, the contract refers to the function that an attacker can insert malicious exploitation into the forwarding request to manipulate any user's token through the judgment of the trusted transponder and the analysis in the sub-call. The slow fog security team suggests that the project party should not use it at the same time when writing the token contract, and if the expected demand needs to quote it at the same time, it must check whether the length is in line with the expectation or use the latest official version of the release details mitigation tool that refers to the attacker's address to attack the contract. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。


















