惊魂一夜 Ledger Connect Kit安全事件分析
2023年12月14日,据 Beosin EagleEye 安全态势感知平台消息,大量去中心化应用由于使用 Ledger 被恶意植入的库导致用户资产被盗,黑客获利超60万美元。Beosin 安全团队第一时间对事件进行了分析,结果如下。
connect-kit简介
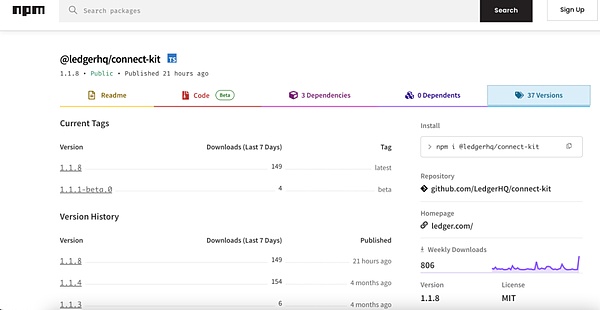
connect-kit是Ledger的一个Javascript库,允许用户将其 Ledger 设备连接到第三方 DApp。库链接地址: https://www.npmjs.com/package/@ledgerhq/connect-kit
漏洞分析
该事件发生的原因是因为一名前 Ledger 员工被网络钓鱼攻击,而Ledger并未取消该员工的代码访问权限,攻击者从而获得了其 NPMJS 帐户的访问权限。随后,攻击者发布了 Ledger Connect Kit 的恶意版本(受影响版本为 1.1.5、1.1.6 和 1.1.7)。
攻击流程
早在4个月前,攻击者便发布了 Ledger Connect Kit 1.1.5 恶意版本,并在两个月前先后发布了 Ledger Connect Kit 1.1.6 和 Ledger Connect Kit 1.1.7 两个恶意版本,通过CDN分发,利用恶意代码将用户的资金转移到指定的黑客钱包地址。
资金追踪
目前黑客的资金地址(0x658729879fca881d9526480b82ae00efc54b5c2d)已被 EagleEye 标记为 Ledger Exploiter,用户可以在 EagleEye 网站上对其进行实时监控:
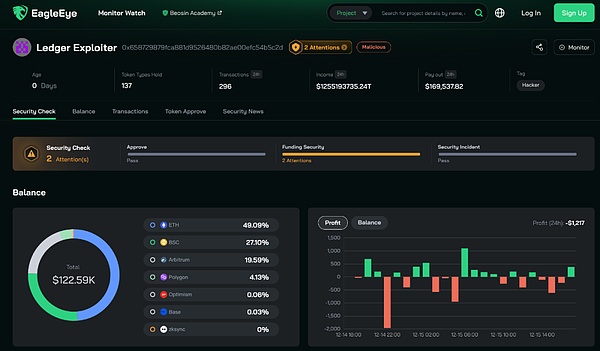
链接:https://eagleeye.space/address/0x658729879fca881d9526480b82ae00efc54b5c2d
此次攻击涉及多条公链,黑客转移了众多用户在Ethereum、BNB Chain、Arbitrum、Base、Fantom等网络的资产,获利超60万美元。
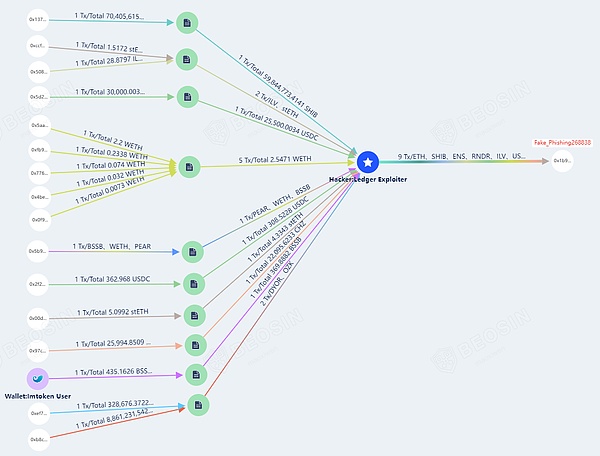
根据Beosin trace查询显示,截止发文时,以太坊上的被盗资金部分被发到了 Fake_Phishing268838 钓鱼地址:
0x1b9f9964a073401a8bc24f64491516970bb84e47
其余还保存在攻击者地址中(由于代币种类过多,以下图片仅展示部分信息)
KYT反洗钱分析平台
BSC链上被盗资金目前全部保存在攻击者地址中:
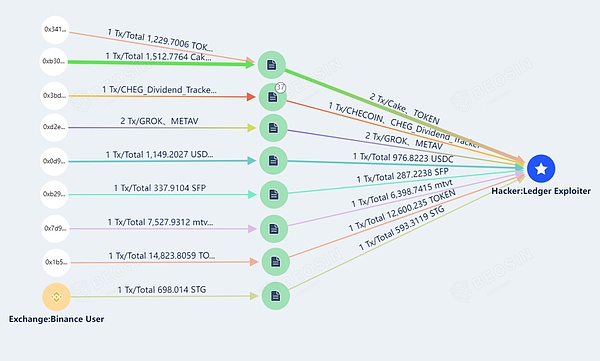
本次事件涉及大量公链上的用户被盗,这里仅展示以太坊和BSC上的被盗情况
安全建议
本次事件再次反映了供应链安全的重要性。在Web3安全中,供应链安全经常被开发者和安全团队忽视,而黑客可以通过软件供应链的各个环节植入恶意代码,窃取用户信息和数字资产,进行大规模的攻击。
Beosin 对防范此类安全事件的建议如下:
1. 在选择和使用第三方软件或组件时,需进行安全审查和验证。了解第三方的安全标准和实践,确保软件没有被篡改或植入恶意代码。
2. 采用安全的开发实践,如使用安全编码标准、代码审查、漏洞扫描和安全测试等,确保软件在开发过程中始终处于安全状态。
3. 及时应用软件供应商发布的安全更新和补丁,以修复已知的漏洞和缺陷。保持软件处于最新版本,减少被攻击的风险。
4. 采用多层次的安全防御策略,包括网络安全、终端安全和数据安全等。使用入侵检测系统、终端安全软件和数据加密等措施,提高整个软件供应链的安全性。
5. 建立监测和响应机制,及时检测异常活动和潜在的供应链攻击,并采取相应的应对措施,如隔离受感染的代码库、及时修复漏洞和恢复数据等。
6. 提供员工培训和意识提升,使其能够识别社会工程学攻击与供应链攻击,并采取适当的防范措施,如警惕钓鱼邮件、不随意下载附件等。开发团队的员工权限需要及时更新,交接代码权限需做到透明清晰。
Beosin 作为一家全球领先的区块链安全公司,在全球10多个国家和地区设立了分部,业务涵盖项目上线前的代码安全审计、项目运行时的安全风险监控、预警与阻断、虚拟货币被盗资产追回、安全合规KYT/AML等“一站式”区块链安全产品+服务,公司致力于Web3生态的安全发展,已为全球3000多个企业提供区块链安全技术服务,包括HashKey Group、Amber Group、BNB Chain等,已审计智能合约和公链主网超3000份,包括PancakeSwap、Ronin Network、OKCSwap等。
According to the news of the security situation awareness platform, a large number of decentralized applications were used. Due to the use of maliciously implanted libraries, users' assets were stolen, and hackers' profits exceeded $10,000. The security team analyzed the incident at the first time. The results are as follows: Yes, a library allowed users to connect their equipment to a third-party library. Vulnerability analysis of the link address. The reason for this incident was that a former employee was attacked by phishing without canceling his code access rights, and the attacker gained access to his account. Permission Then the malicious version released by the attacker, the affected version is and the attack process. As early as two months ago, the attacker released the malicious version and two malicious versions two months ago. By distributing malicious codes, the user's funds were transferred to the designated hacker wallet address. At present, the hacker's fund address has been marked as a link for users to monitor it in real time on the website. This attack involves many public chains, and hackers have transferred many users' assets waiting for the network to be obtained. According to the inquiry, the profit exceeds USD 10,000. At the time of publication, some of the stolen funds on the Ethereum were sent to the fishing address and the rest were kept in the attacker's address. Due to too many kinds of tokens, the following pictures only show some information. At present, all the stolen funds on the anti-money laundering analysis platform chain are kept in the attacker's address. This incident involves a large number of users on the public chain being stolen. Here, only the stolen situation on the Ethereum and the Internet is shown. Safety suggestions: This incident once again reflects the importance of supply chain security. Chain security is often ignored by developers and security teams, and hackers can implant malicious code through all links of the software supply chain to steal user information and digital assets and carry out large-scale attacks. Suggestions for preventing such security incidents are as follows: when selecting and using third-party software or components, you need to conduct security review and verification, understand the security standards and practices of third parties, and ensure that the software has not been tampered with or implanted with malicious code, and adopt safe development practices, such as using security coding standard code to review vulnerability scanning. Description and security testing to ensure that the software is always in a safe state during the development process, timely apply security updates and patches issued by software vendors to repair known vulnerabilities and defects, keep the software in the latest version, reduce the risk of being attacked, adopt multi-level security defense strategies, including network security, terminal security and data security, use intrusion detection systems, terminal security software and data encryption to improve the security of the entire software supply chain, establish monitoring and response mechanisms, and detect anomalies in time. Activities and potential supply chain attacks and take corresponding countermeasures, such as isolating the infected code base, timely repairing vulnerabilities and restoring data, etc., providing staff training and raising awareness so that they can identify social engineering attacks and supply chain attacks and take appropriate preventive measures, such as being wary of phishing emails and not downloading attachments at will. The employee rights of the development team need to be updated in time, and the handover code rights need to be transparent and clear. As a leading blockchain security company in many countries and places around the world, The district has set up a branch business covering the code security audit before the project goes online, the security risk monitoring, early warning and blocking of virtual currency, the recovery of stolen assets and safety compliance, etc. The one-stop blockchain security product service company is committed to the safe development of ecology, and has provided blockchain security technical services to many enterprises around the world, including audited smart contracts and public chain main network. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。