报告解读之年度十大攻击事件
本篇主要聚焦于 2023 年十大攻击事件。
十大攻击事件
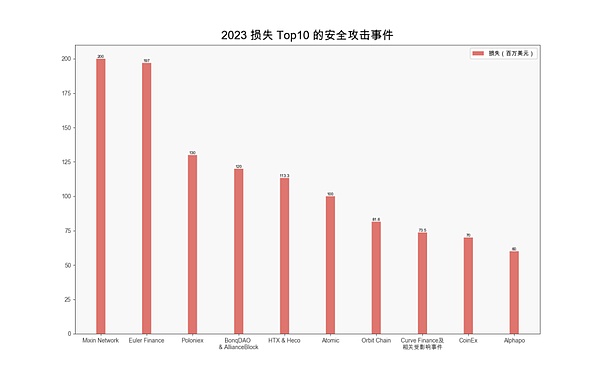
(2023 损失 Top10 的安全攻击事件)
Mixin
2023 年 9 月 23 日,Mixin Network 云服务提供商数据库遭到攻击,导致主网部分资产丢失,涉及资金约 2 亿美元,是 2023 年损失最大的攻击事件。随后,Mixin 官推称,已联系谷歌和慢雾安全团队协助调查。官方表示将最多赔付 50% 的损失,剩余部分以债券代币形式赔付,并用利润进行回购。
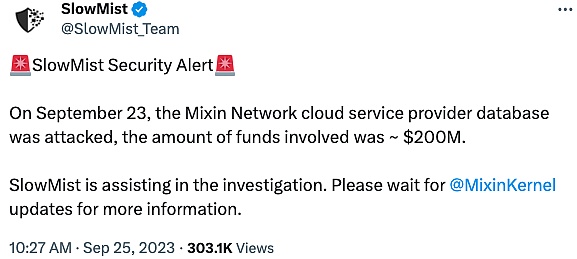
(https://twitter.com/SlowMist_Team/status/1706133260869468503)
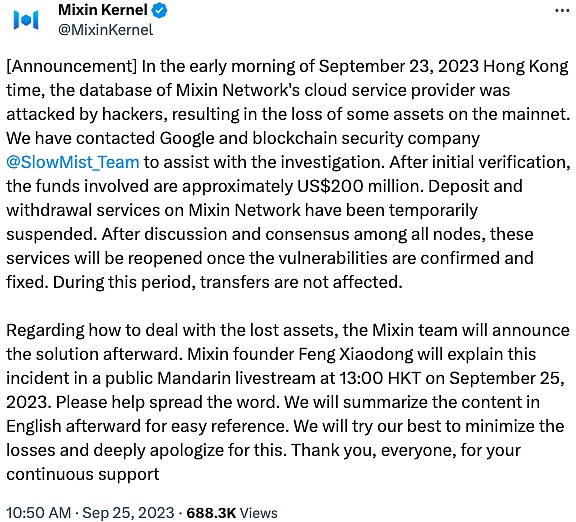
(https://twitter.com/MixinKernel/status/1706139175018529139)
Euler Finance
2023 年 3 月 13 日,DeFi 借贷协议 Euler Finance 遭到攻击,攻击者获利约 1.97 亿美元。据慢雾安全团队分析,攻击者的整个攻击流程主要是利用闪电贷的资金去存款,之后在两次叠加杠杆借贷后通过将资金直接捐赠给储备地址来触发清算逻辑,最后通过软清算自己来套利出之前剩余的所有资金。攻击的主要原因有两点:第一点是将资金捐赠给储备地址后没有检查自身是否处于爆仓状态,导致能直接触发软清算的机制,第二点是由于高倍杠杆触发软清算逻辑时,yield 数值会增大,导致清算者只需转移一部分的负债到自身即可获得被清算人的大部分抵押资金,由于抵押资金的价值是大于负债的价值(负债因为软清算只转移了一部分),所以清算者可以成功通过自身的健康系数检查而提取获得的资金。4 月 4 日,Euler Labs 在推特上表示,经过成功协商,攻击者已归还 3 月 13 日从协议中盗取的所有资金。
2024 年 1 月 10 日,Euler Labs 的 CEO Michael Bentley 发布名为《战争与和平》的博客,其中记述了这起攻击事件的背景、处理过程等细节。
(https://medium.com/eulerfinance/war-peace-ab2670711175)
(https://twitter.com/euler_mab/status/1745079435332550836)
Poloniex
2023 年 11 月 10 日,Poloniex 交易所遭黑客攻击,造成的损失约为 1.3 亿美元。据慢雾安全团队分析,从攻击者这种迅速、专业的手法来看,猜测是典型的 APT 攻击,攻击者或为朝鲜黑客组织 Lazarus Group。孙宇晨表示:"Poloniex 团队已成功识别并冻结了与黑客地址相关的部分资产。目前,损失在可控范围内,Poloniex 的营业收入可以弥补这些损失,将全额偿还受影响的资金。”
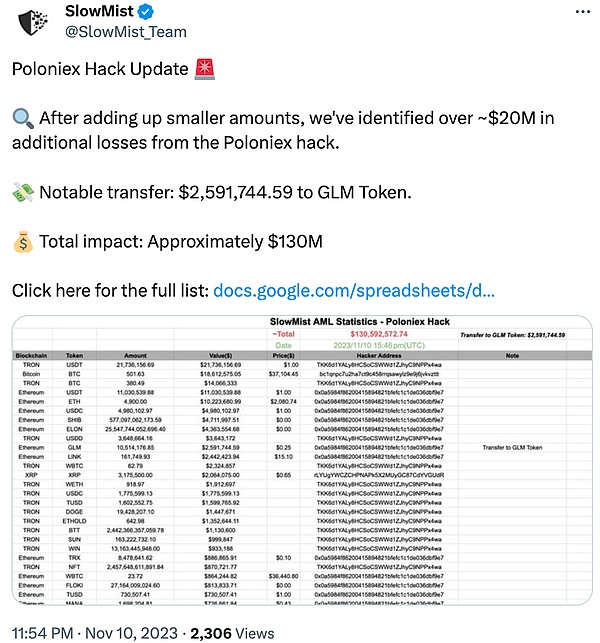
(https://twitter.com/SlowMist_Team/status/1723006264693657708)
BonqDAO & AllianceBlock
2023 年 2 月 2 日,非托管借贷平台 BonqDAO 和加密基础设施平台 AllianceBlock 因 BonqDAO 的智能合约漏洞而被黑客攻击,损失约 1.2 亿美元。其中黑客从 BonqDAO 的一个金库中移除了大约 1.14 亿 WALBT(1100 万美元)、AllianceBlock 的包装原生代币和 9800 万 BEUR 代币(1.08 亿美元)。据慢雾安全团队分析,此次攻击的根本原因在于攻击者利用预言机报价所需抵押物的成本远低于攻击获得利润从而通过恶意提交错误的价格操控市场并清算其他用户。此外 AllianceBlock 表示该事件与 BonqDAO 金库无关,没有智能合约被破坏,两个团队都致力于消除流动性,以减轻黑客将被盗代币转换为其他资产的行为。详情可见 AllianceBlock 回应 BonqDAO 黑客攻击的声明。
(https://medium.com/allianceblock/allianceblock-issues-statement-in-response-to-bonqdao-hack-6510a61fcf5c)
HTX & Heco Bridge
2023 年 11 月 22 日,HTX(原 Huobi)及其相关的 Heco 跨链桥被黑客攻击,总金额达 1.133 亿美元。孙宇晨于推特回应了此次攻击事件:“HTX 和 Heco 跨链桥遭受黑客攻击。HTX 将全额补偿 HTX 热钱包损失。暂停充值和提现。请社区放心, HTX 所有资金安全。我们正在调查黑客攻击的具体原因。一旦我们完成调查并查明原因,我们将恢复服务。”
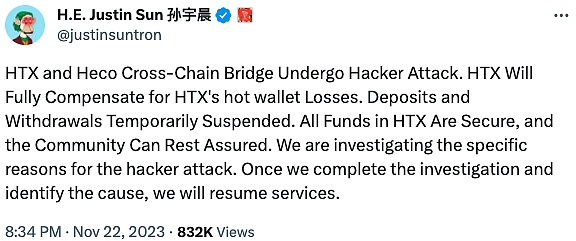
(https://twitter.com/justinsuntron/status/1727304656622326180)
Atomic Wallet
2023 年 6 月 3 日,多名 Atomic Wallet 用户在社交媒体发文称自己的钱包资产被盗。Atomic 表示目前不到 1% 的月活用户受到影响/已上报。据慢雾安全团队分析,Atomic 钱包官方紧急下线 cloudflare 的下载站点与 sha256sum 验证站点,由此猜测可能是在历史版本下载这个环节上出现了安全问题。预计造成至少 1 亿美元的损失。
Orbit Chain
2023 年 12 月 31 日,跨链桥协议 Orbit Chain 遭黑客攻击,损失 8160 万美元。Orbit Chain 发推表示,团队已要求全球主要加密货币交易平台冻结被盗资产。2024 年 1 月 11 日,Orbit Chain 推特更新称将向决定性情报提供者发放最高 800 万美元赏金。
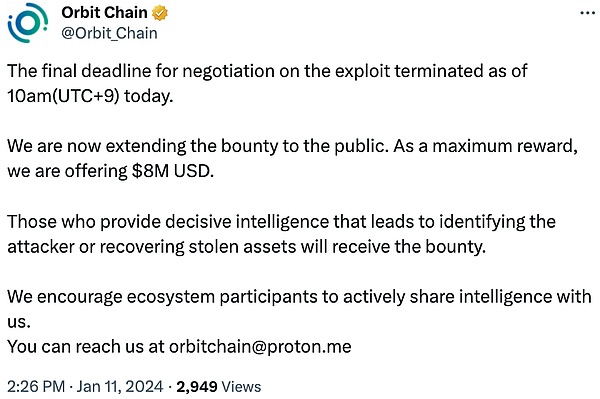
(https://twitter.com/Orbit_Chain/status/1745331289098711041)
Curve Finance 及相关事件
2023 年 7 月 30 日,Curve Finance 推特称,由于递归锁出现故障,许多使用 Vyper 0.2.15 的稳定币池(alETH/msETH/pETH) 遭到攻击。crvUSD 合约和其它资金池不受影响。截至目前,Curve Finance 稳定币池黑客攻击事件已造成 Alchemix、JPEG'd、MeTRONomeDAO、deBridge、Ellipsis 和 CRV/ETH 池累计损失 7350 万美元。8 月 6 日, Alchemix 发推表示,Curve Finance 黑客已将 Alchemix 在 Curve 池中的资金全部归还。8 月 19 日,MeTRONomeDAO 表示名为 "c0ffeebabe" 的 MEV bot 已收回大部分被盗资金并归还给了 MeTRONome。
CoinEx
2023 年 9 月 12 日,加密货币交易所 CoinEx 遭遇黑客攻击,初步确定事件原因为热钱包私钥泄露,造成的损失预计已达 7000 万美元,影响波及多个区块链。CoinEx 推特称,已识别并隔离与黑客攻击相关的可疑钱包地址,存取款服务已暂停。9 月 13 日,慢雾安全团队在分析过程中发现 CoinEx 黑客与 Stake.com 黑客、Alphapo 黑客存在关联,CoinEx 黑客或为朝鲜黑客团伙 Lazarus Group。
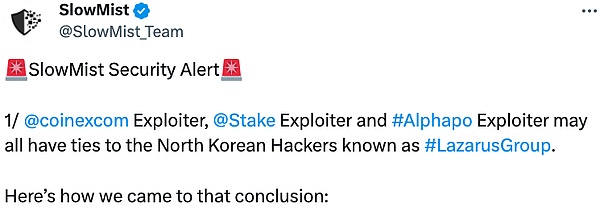
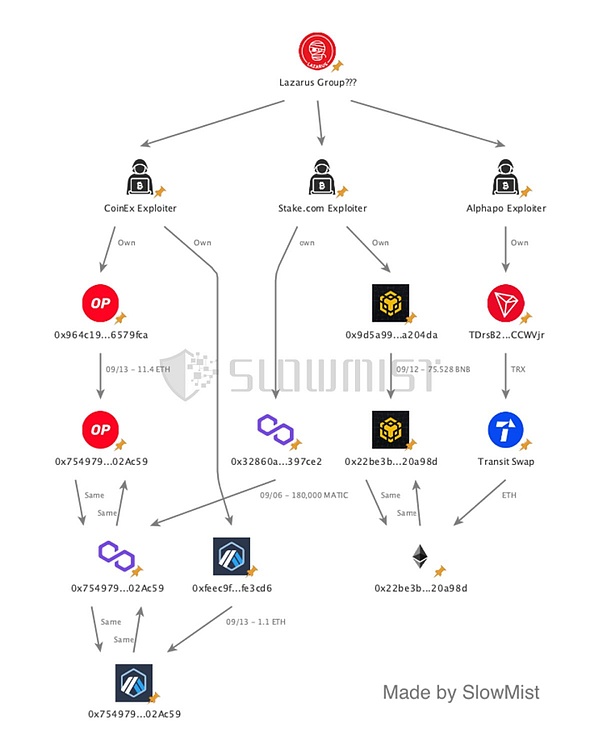
(https://twitter.com/SlowMist_Team/status/1701919426009035190)
Alphapo
2023 年 7 月 23 日,加密货币支付服务商 Alphapo 热钱包被盗,损失约 6000 万美元,包括 Ethereum、TRON 和 BTC。被盗资金首先被在以太坊上交换为 ETH,然后跨链到 Avalanche 和 BTC 网络。Alphapo 处理许多博彩服务的支付,比如 HypeDrop、Bovada 和 Ignition。此次黑客攻击很可能是由 Lazarus Group 完成。
总结
2023 年十大攻击事件导致共计约 11.45 亿美元的损失,其中 Euler Finance 的被盗资金成功全部收回,Curve Finance 及相关事件收回了部分被盗资金。慢雾安全团队建议项目方进行全面的审计,及时发现并修复潜在的安全漏洞;建立健全的应急计划,以便在遭受攻击时能够快速、有效地应对;在安全事件发生后,主动披露,承担责任,并采取切实可行的补救措施,控制影响范围和程度。
完整报告下载:
https://www.slowmist.com/report/2023-Blockchain-Security-and-AML-Annual-Report(CN).pdf
This article mainly focuses on the security attacks of the top ten attacks in 2008. The database of cloud service providers was attacked on October, which resulted in the loss of some assets of the main network, involving about $100 million, which was the biggest attack in 2008. Later, the official said that he had contacted Google and the slow fog security team to assist in the investigation. The official said that the rest of the losses would be paid in the form of bond tokens and repurchased with profits. The loan agreement was attacked, and the attacker made about $100 million. According to the slow fog, The security team analyzed the attacker's whole attack process, which mainly used the funds of lightning loan to deposit, and then directly donated the funds to the reserve address after two superimposed leveraged loans to trigger the liquidation logic. Finally, all the remaining funds were arbitrage through soft liquidation. There are two main reasons for the attack. The first point is that after donating the funds to the reserve address, it is not checked whether it is in a burst state, which can directly trigger the soft liquidation mechanism. The second point is that the high leverage triggers the soft liquidation. The value of the calculation logic will increase, which will cause the liquidator to obtain most of the mortgaged funds of the liquidator only by transferring part of the liabilities to himself. Because the value of the mortgaged funds is greater than the value of the liabilities, the liquidator can successfully withdraw the obtained funds through his own health coefficient check. On March, he tweeted that the attacker had returned all the funds stolen from the agreement after successful negotiation. On March, he published a blog called War and Peace. It describes the background, handling process and other details of this attack. According to the analysis of the slow fog security team, the loss caused by the hacker attack on the exchange on March is about 100 million US dollars. From the quick and professional approach of the attacker, it is speculated that it is a typical attacker or a hacker organization for North Korea. Sun Yuchen said that the team has successfully identified and frozen some assets related to the hacker address. The current loss of operating income within the controllable range can make up for these losses, and the affected funds will be fully repaid on March. The hosted lending platform and encrypted infrastructure platform were hacked and lost about $100 million because of the smart contract loopholes, among which the hacker removed about $100 million in original packaging tokens and $100 million in tokens from a vault. According to the analysis of the slow fog security team, the root cause of the attack was that the cost of collateral needed by the attacker to quote by the Oracle was much lower than that of the attack, thus manipulating the market and liquidating other users by maliciously submitting the wrong price. In addition, it was said that the incident had nothing to do with the vault. Whether the smart contract is broken or not, both teams are committed to eliminating liquidity to reduce the hacker's behavior of converting stolen tokens into other assets. For details, please see the statement in response to the hacker attack. The total amount of hacking on the original and its related cross-chain bridge reached US$ 100 million. Sun Yuchen responded to the attack and the cross-chain bridge hacking on Twitter, and will fully compensate for the loss of hot wallet, suspend recharge and withdrawal. Please rest assured that all funds are safe. We are investigating the specific reasons for hacking. Once I. We completed the investigation and found out the reason. We will resume the service. Many users posted on social media that their wallet assets were stolen, indicating that less than monthly users were affected. According to the analysis of the download site and verification site of the official emergency offline of the wallet by the slow fog security team, it is speculated that there may be a security problem in the download link in version history, which is expected to cause at least a loss of US$ 100 million. The cross-chain bridge agreement was hacked and the loss of US$ 10,000 was tweeted, indicating that the team has requested it. The world's major cryptocurrency trading platforms freeze the stolen assets. The Twitter update said that it would issue a reward of up to $10,000 to decisive intelligence providers and related events. The Twitter said that due to the failure of recursive locks, many used stable fontana di trevi contracts and other fund pools were not affected. Up to now, the hacking incident in fontana di trevi has caused a cumulative loss of $10,000 to the pool. It was tweeted that the hackers had returned all the funds in the pool. The month said that most of them were stolen. The funds were returned to the cryptocurrency exchange on March, which was attacked by hackers. It was initially determined that the cause of the incident was that the loss caused by the leakage of the private key of the hot wallet was estimated to have reached 10,000 US dollars, which affected many blockchains. Twitter said that the suspicious wallet address related to the hacker attack had been identified and isolated, and the deposit and withdrawal service had been suspended. During the analysis, the slow fog security team found that hackers were related to hackers, or that the loss of the hot wallet was about 10,000 US dollars for the North Korean hacker group. Including the exchange of stolen funds in the Ethereum first, and then the payment of many gambling services across the chain and the network. For example, this hacking attack is likely to be caused by the completion of the top ten attacks in the year, resulting in a total loss of about hundreds of millions of dollars, of which all the stolen funds were successfully recovered and some of the stolen funds were recovered. The slow fog security team suggested that the project party conduct a comprehensive audit to find and fix potential security vulnerabilities in time and establish a sound emergency plan so that it can be attacked. Respond quickly and effectively to the voluntary disclosure after a security incident, take responsibility and take practical remedial measures to control the scope and degree of influence. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。


















