暴涨的Sui势头强劲 准备打响Move生态的第一炮?
2024年,暴涨的Sui势头强劲,打响了Move生态的第一炮。
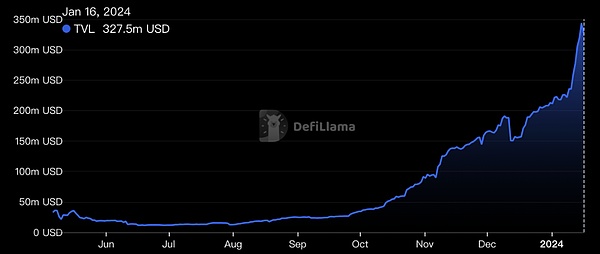
首先是近一周暴涨接近70%,让市场再次关注到这个Move系的亮眼之星,据 DefiLlama 数据,Sui TVL 已达 3.27 亿美元,24小时涨幅 6.76%,过去 7 日上涨 73.19%。当前其链上 TVL 排名前三位的协议分别为:Cetus(6244 万美元)、NAVI Protocol(6142 万美元)以及 Scallop Lend(5496 万美元)。
作为Move生态的重要一员,Sui致力于促进数字资产的安全、互操作性和可持续发展。今天,跟随Beosin研究团队的安全视角,再次看看2024年Sui还有哪些机会。

势头强劲的Sui,是Solana Killer还是ETH Killer?
Sui 是由 Mysten Labs 打造的一条高性能公链,使得开发人员能在 Sui 上构建低延时,高吞吐量的应用。Mysten Labs 由原 Facebook 的 Novi 项目负责人 Evan Cheng 创立,在2021年12月融资3600万美元,之后在2022年9月以超过20亿美元的估值融资3亿美元。
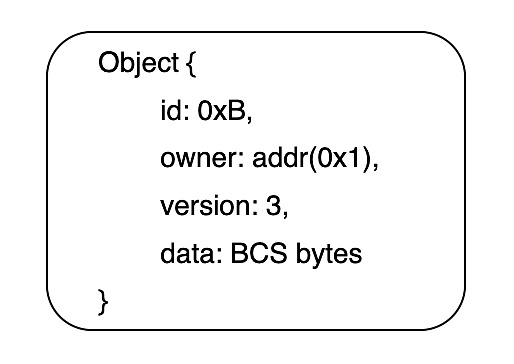
Sui 的特点是采用以对象为核心的数据模型。每个对象会存储一个全局的,唯一的ID、一份所有者的元数据、一个版本号 (version:每次该对象被调用后会加1) 和二进制规范序列化数据 (Binary Canonical Serialization) ,如下图所示:
由于采用了对象的数据模型,Sui 可以根据不同交易中的对象是否互相依赖将交易进行分组,从而在不同的节点处理不同的交易,实现并行处理多笔交易。
Sui 将对象分为owned object和shared object。
Owned object使用场景有代币和NFT。对于只包含owned object的交易,Sui 采用 Byzantine Consistent Broadcast(BCB) 共识算法来确认交易。BCB共识算法可以简单理解为首先由验证者投票是否打包交易,然后交易发起者统计投票结果,再由验证者检验统计结果是否正确来决定是否打包交易。这一算法优点在于统计过程在客户端执行,减少了验证者节点之间的沟通时间,从而快速确认交易。
Shared object使用场景为DeFi、NFT交易市场、游戏等需要与用户频繁交互的应用。对于包含shared object的交易,Sui 采用 Narwhal 和 Bullshark 协议进行排序和验证。Narwhal 是 Sui 的交易内存池,负责检查待处理的交易并生成一条有向无环图路径遍历这些交易。Bullshark 对某一特定的有向无环图遍历达成共识,从而确认这些交易的特定顺序。
基于以上的设计,目前Sui测试的TPS最高达到了297,000,确认交易的时间约为480ms,性能表现优异。
相比于Solana和以太坊,Sui有哪些优势?
(1) 底层设计更安全
Sui支持的Move智能合约需先进行字节验证随后再执行。Move语言有内置的字节码验证器以检查资源、类型和内存安全。这样可以在执行合约前检查许多常见错误并且避免合约遭受恶意代码的攻击。
(2) 原生资源安全
Sui以对象 (object) 为核心的数据模型允许开发者使用 copy、drop、store、key这四个关键词对资源进行权限设置和编程,而Solana无原生的资源安全,资源安全由各个合约自行实现。
(3) 更注重用户安全
Sui提供交易预执行服务,钱包服务提供商可以在预执行合约后将合约执行结果和合约权限告知用户,帮助他们在交互dApp时能够在签署交易前清楚地知道交易可能造成的后果,大大降低欺诈风险。
Sui上的三剑客,还有哪些机会可以参与?
目前Sui头部项目有一站式DeFi项目Cetus、借贷项目NAVI Protocol和Scallop Lend,这三剑客占据Sui生态50%的TVL。
1. Cetus
Cetus设定的主要目标是开发灵活且强大的一级流动性网络,为Aptos和Sui的资产交易提供便利。该协议的目标是为DeFi生态系统中的消费者提供最好的交易体验和效率。它通过重点流动性协议以及一系列相关的可互操作操作模块来实现这一点。
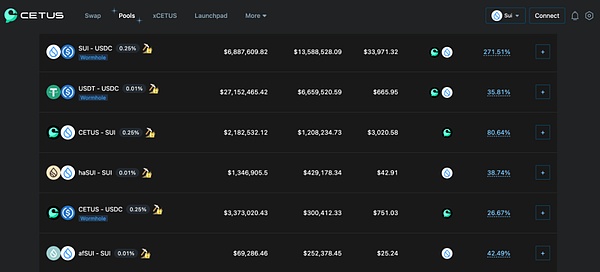
https://app.cetus.zone/pool/list
目前部分流动性池子获得Sui官方的流动性激励,获得CETUS奖励的同时还可获得SUI代币奖励。
2. NAVI Protocol
NAVI Protocol提供主流代币、稳定币和CETUS代币的借贷服务。NAVI的创新功能,例如自动杠杆金库和隔离模式,使用户能够利用其资产并以最小的风险获得新的交易机会。NAVI的设计为不同风险级别的数字资产提供了支持,同时其先进的安全功能确保了用户资金的保护和系统性风险的缓解。
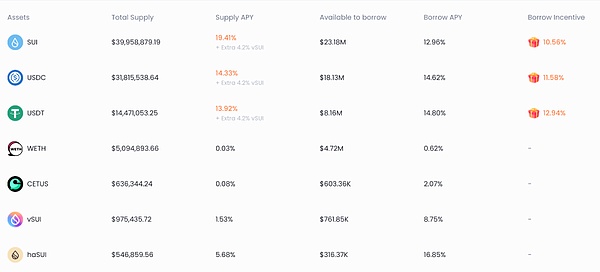
https://app.naviprotocol.io/market
目前NAVI与OKX DeFi合作推出了代币额外加息服务,用户可存入USDC享受高达35%的APY。其奖池总共为50000USDC和100000CETUS,奖池领完即止。
3. Scallop Lend
Scallop Lend是Sui生态第一大的借贷协议,也是第一个获得 Sui 基金会官方资助的 DeFi 协议。与NAVI Protocol类似,Scallop Lend提供8种代币的借贷服务,并提供面向专业交易者的 SDK。在2024年1月1日Scallop Lend完成空投快照,空投第一阶段开启。
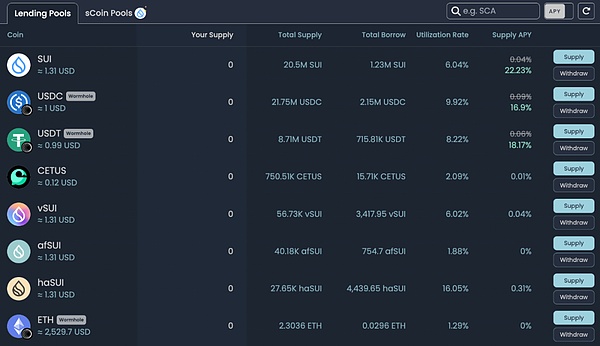
https://app.scallop.io/
错过本次空投活动的用户可以继续使用Scallop Lend的借贷服务以获得Scallop Lend第二阶段的空投奖励。
Beosin推出针对Move智能合约的安全审计服务
Beosin与Sui的合作从去年已开始,此前Beosin安全团队发现了多个公链的漏洞。其中一个漏洞比较有意思,我们与Sui团队沟通后,征得同意可以将其详细信息公开。这是Sui公链p2p协议中的一个拒绝服务漏洞,该漏洞可导致Sui网络中的节点因内存耗尽而崩溃。这个拒绝服务漏洞是由一个古老的攻击方式引起的——“内存炸弹”,详情可阅读:《Beosin发现Move VM严重级别漏洞:可导致 Sui、Aptos 等公链全网崩溃,甚至可能硬分叉》。
Move合约可能出现的漏洞点
1) 开发者在使用Aptos、Sui,或者其他基于Move的blockchain中独特的Framework进行开发时,应保持一定程度的安全意识,确保供应链安全。
2) 函数权限问题。对于一些函数调用的权限要仔细划分,因为一些关键函数会涉及到治理,严重的会影响到资金安全,针对这种函数调用需要对调用者进行鉴权。
3) 业务逻辑在设计和代码实现时,均需注意其中的逻辑问题。如一些DeFi项目关于闪电贷的实现,此前Beosin对Move版本的闪电贷进行了研究,详情可查看《Web3技术研究 | Solidity闪电贷实现方式与Move以及Rust闪电贷实现方式有何不同?》。
4) 关于Move系项目,在模块升级时需要注意代码的 owner 在初始部署后是不可改变的,且部署者的地址在部署后永远拥有升级权限。
Move合约审计服务与审计项
Beosin安全团队在2022年年底已推出针对Move智能合约的安全审计服务,旨在提前发现并协助项目方修复项目中的安全风险,保障用户与项目方的资产安全。其主要安全审计项包括:
•溢出漏洞
•重放攻击
•不安全的随机数
•交易顺序依赖
•拒绝服务
•访问控制
•权限不当
•业务设计
•业务实现
•可操纵的代币价格
•套利攻击
•Gas优化
•第三方模块安全
•能力安全
•资源安全
•升级安全
•中心化风险
Beosin Move智能合约安全审计服务的详细信息可查看《Beosin | 正式推出针对Move智能合约的安全审计服务,从安全角度看Move语言(上)》。
此外,Beosin于2023年推出Move Lint静态检测工具,帮助开发者实现
自动化发现合约中的潜在安全隐患,定位漏洞产生的位置,增强合约的安全性。详细介绍可查看《Beosin推出Move Lint静态检测工具,通过最佳实践提高Sui公链智能合约开发的安全性》。
2024年Sui会实现更快的增长吗?
Move智能合约语言被设计为安全且可靠的,以避免一些传统智能合约语言(如Solidity)中存在的漏洞和安全风险。这使得Sui的合约更加可信和安全,为用户提供了更好的保障。
Sui在2024年开始发力,注重生态发展成为其打法之一,Sui的总锁定价值(TVL)已达到3.27亿美元,显示出用户对该项目的信任和参与度,表明其生态系统的快速增长和用户的持续增加。此外,Sui在非EVM链上TVL排名中位列前三,与其他协议如Cetus、NAVI Protocol和Scallop Lend一起,共同推动着Move生态系统的发展。
2024年的Sui会起飞吗,我们拭目以待。
The soaring momentum in 2008 started the first shot of the ecology. First, the soaring in the past week drew the market's attention to the bright star of this department again. According to the data, it has increased by 100 million US dollars per hour. At present, the top three agreements in its chain are 10,000 US dollars and 10,000 US dollars respectively. As an important member of the ecology, it is committed to promoting the security, interoperability and sustainable development of digital assets. Today, follow the research team's security perspective to see what other opportunities are there in 2008. A high-performance public chain created by enables developers to build low-latency and high-throughput applications on the Internet. It was founded by the original project leader. After raising $10,000 in a year, it raised $100 million in a year with an estimated value of more than $100 million in a year. Its characteristic is that it adopts an object-centered data model. Each object will store a global and unique copy of the owner's metadata, and a version number will be added every time the object is called. As shown in the following figure, due to the adoption of the number of objects, According to the model, transactions can be grouped according to whether the objects in different transactions depend on each other, so that different transactions can be processed at different nodes to realize parallel processing of multiple transactions. The objects can be divided into and used in scenarios with tokens, and the transaction consensus algorithm can be simply understood as the calculation that the verifier votes whether to package the transaction, and then the transaction initiator counts the voting results, and then the verifier checks whether the statistical results are correct to decide whether to package the transaction. The advantage of this method lies in that the execution of the statistical process at the client reduces the communication time between verifier nodes, thus quickly confirming that the transaction usage scenario is an application that needs frequent interaction with users, such as trading market games, etc. The transaction memory pool is responsible for checking the transactions to be processed and generating a directed acyclic graph path to traverse these transactions, and reaching a consensus on a specific directed acyclic graph traversal to confirm that the specific order of these transactions is based on the above. At present, the design has reached the highest time to confirm the transaction, which is about excellent performance. What are the advantages compared with Ethereum? The underlying design is more secure. The intelligent contract needs byte validation before execution. The language has a built-in bytecode validator to check the resource type and memory security, so that many common errors can be checked before execution of the contract and the contract can be prevented from being attacked by malicious code. The object-centered data model allows developers to use these four levels. Key words set permissions and program resources without original resource security. Resource security is realized by each contract itself, paying more attention to user safety, providing transaction pre-execution services, and wallet service providers can inform users of contract execution results and contract permissions after pre-execution of contracts, helping them to clearly know the possible consequences of transactions before signing transactions, greatly reducing the risk of fraud. What other opportunities can the Three Musketeers have to participate in the current head project? There is a one-stop project loan. The main goal of the project and the setting of the ecology occupied by the three musketeers is to develop a flexible and powerful first-level liquidity network to facilitate the asset transaction of Hehe. The goal of this agreement is to provide the best trading experience and efficiency for consumers in the ecosystem. It is achieved through key liquidity agreements and a series of related interoperable modules. At present, some liquidity pools receive official liquidity incentives and rewards, and at the same time, they can also receive token rewards to provide mainstream tokens to stabilize coins and coins. The innovative functions of token lending service, such as automatic leveraged vault and isolation mode, enable users to use their assets and obtain new trading opportunities with minimum risk. The design provides support for digital assets with different risk levels, while its advanced security function ensures the protection of users' funds and the mitigation of systemic risks. At present, it has cooperated with the company to launch an additional interest rate hike service for tokens, and users can deposit and enjoy up to their prize pool, which is the largest loan agreement in ecology while the prize pool is exhausted. The first agreement that was officially funded by the Foundation and similar loan services that provided tokens and provided airdrops for professional traders were completed on January, and the first phase of airdrops was opened to enable users who missed this airdrop activity to continue to use the loan services to get the second phase of airdrops rewards. The security audit service and cooperation for smart contracts were launched since last year. Before that, the security team found a number of loopholes in the public chain, one of which was more interesting. After we communicated with the team, With consent, the details can be made public. This is a denial-of-service vulnerability in the public chain protocol, which can lead to the collapse of nodes in the network due to memory exhaustion. This denial-of-service vulnerability is a memory bomb caused by an ancient attack method. Read and find out the details of serious-level vulnerabilities, which can lead to the collapse of the public chain network and even the possible loopholes in hard-forked contracts. Developers should maintain a certain degree of security awareness when using or other unique development based on. The authority of the function of ensuring supply chain security should be carefully divided for the authority of some function calls, because some key functions will involve governance, which will seriously affect the safety of funds. For this function call, the caller needs to be authenticated. Business logic should pay attention to the logical problems in the design and code implementation, such as some projects about the realization of lightning loan. For details, please see the technical research on the realization of lightning loan and what is the difference between the realization of lightning loan. During the module upgrade of related projects, it should be noted that the code cannot be changed after the initial deployment, and the address of the deployer will always have the upgrade right after deployment. The security team has launched a security audit service for smart contracts at the end of the year, aiming at discovering and assisting the project side to repair the security risks in advance and ensuring the asset security of users and the project side. Its main security audit items include overflow vulnerabilities, replay attacks, unsafe random number transaction sequence dependence. Inappropriate service access control authority, business design, business realization, controllable token price arbitrage attack, optimization of third-party module security capability, security resource security upgrade, security centralization risk, security audit service, details of which can be found in the official launch of security audit service for smart contracts. From a security perspective, in addition, static detection tools were launched in to help developers realize automatic discovery of potential security risks in contracts, locate vulnerabilities and enhance the security of contracts. Detailed introduction can be found in the launch of static detection tools to improve the security of public chain smart contracts through best practices. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。


















