详解Socket攻击事件始末
2024 年 1 月 16 日,Socket Tech遭到攻击,损失约 330 万美元。 攻击者利用了Socket某合约中数据验证环节的漏洞,通过恶意数据输入盗取了授权合约的用户资金。 这次攻击共给 230 个地址带来损失,最大的单地址损失约为 65.6 万美元。
背景介绍
Socket 是一种服务于跨链安全、高效数据和资产传输的互操作性协议。 Socket Gateway合约是与 Socket 流动性层所有交互的接入点,所有资产桥接器和 DEX 在此汇聚成一个唯一的元桥接器,并根据用户偏好(如成本、延迟或安全性)选择最佳交易路由。
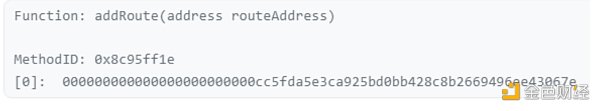
黑客攻击发生的前三天,Socket合约管理员执行了addRoute命令,在系统中加入了一条新路由。 添加路由的目的是扩展Socket网关的功能,但却无意中引入了一个关键漏洞。
下图为通过合约管理员添加路由的记录
事件梗概
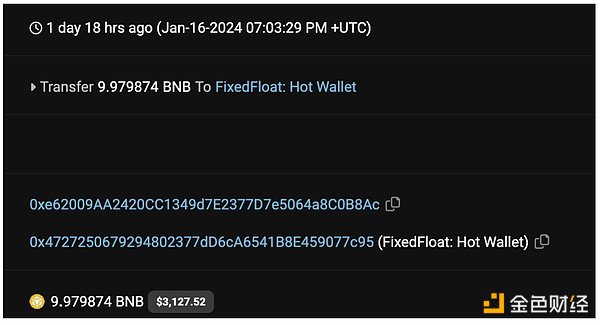
1. 北京时间1月16日15:03,攻击者钱包转入攻击所用资金,我们的时间分析表明这笔资金来自0xe620,与从Tornado Cash提取的10 BNB有关。
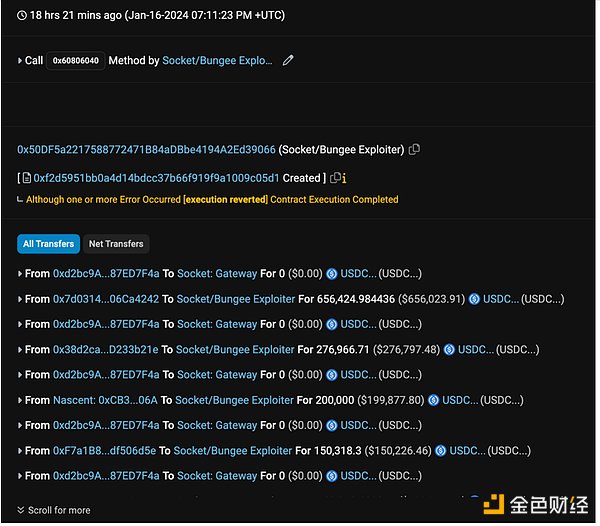
2. 这些资金被用于创建和执行两个合约,来利用Socket的漏洞。 第一个合约针对的是授权了 SocketGateway 的地址中的 USDC(截图如下);127 名受害者被骗走约 250 万美元。
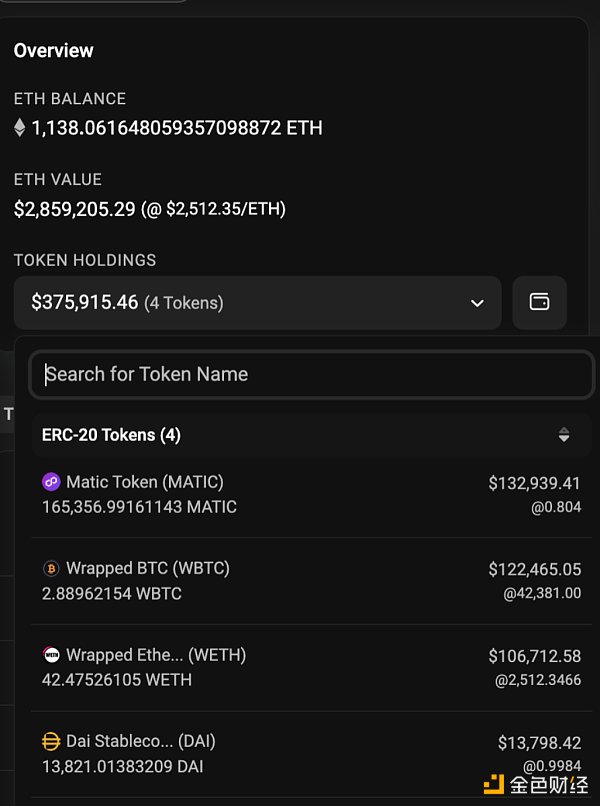
3. 接下来,第二个合约则将目标对准了受害者地址内的WETH, USDT, WBTC, DAI 与MATIC。于是,另外104名受害者损失了如下资产:
- 42.47526105 WETH
- 347,005.65 USDT
- 2.88962154 WBTC
- 13,821.01 DAI
- 165,356.99 MATIC
4. 攻击者将USDC与USDT转换成了ETH。
漏洞来源
被攻击者利用的漏洞存在于新添加的路由地址 routeAddress内的performAction函数中。
该地址内的performAction函数原本的功能是协助Wrapping与Unwrapping的功能。 然而,该函数中出现了一个关键漏洞:用户在无需验证的情况下,直接在.call() 中通过swapExtraData调用外部数据,这意味着攻击者可以执行任意恶意函数。
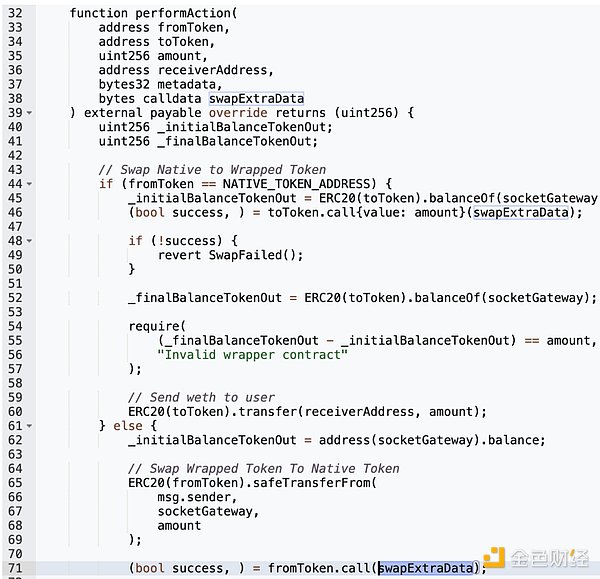
在这次事件中,攻击者制作了一个恶意的 swapExtraData 输入,触发transferFrom函数。 该恶意调用利用了用户对 SocketGateway 合约的授权,从他们那里盗走了资金。
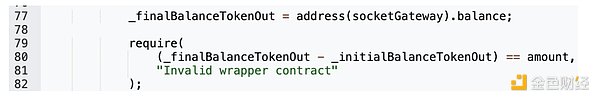
虽然合约会通过检查余额检查确保 fromToken.call() 调用后用户余额会出现正确的变化,但该函数没有考虑攻击者将金额设置为0的情况。
还原攻击流程
1. 使用攻击合约,攻击者在Socket Gateway合约上调用了0x00000196()。
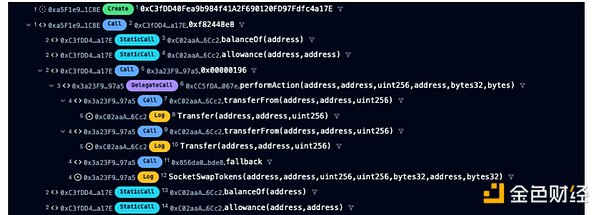
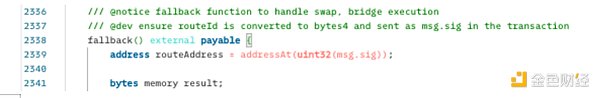
2. fallback() 使用六进制签名 196 调用了有漏洞的路由地址合约(routerAddress)。
3. 在下面的截图中,我们可以看到攻击者使用的虚假输入,Swapping数量全部为0。
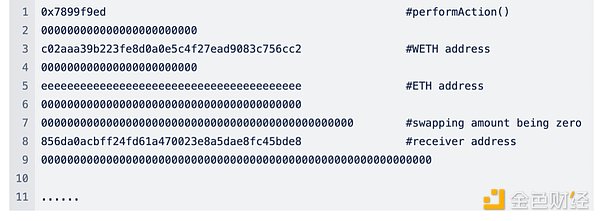
4. 接下来将调用WrappedTokenSwapperImpl.performAction() 进行Swap。
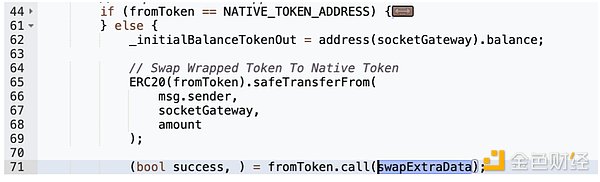
5. 在没有进行任何验证的情况下,虚假的SwapExtraData被fromToken (WETH)接受并执行。
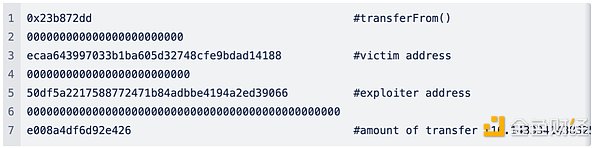
6. 攻击者重复执行以上流程,直到受害者资产耗尽。 恶意交易出现后,Socket 迅速调用了 disableRoute,屏蔽了之前有漏洞的路由,阻止了更大范围的攻击。
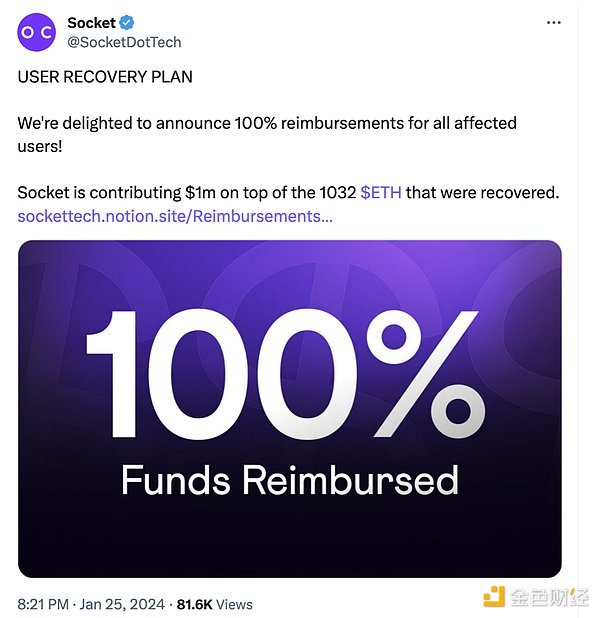
7. 1月23日,Socket宣布已经追回1032枚ETH,并在25日宣布将全额补偿所有损失。本次事件得到解决。
事件总结
在有着无限额用户授权的路由合约中,恶意 calldata 攻击并不罕见。 以前类似的攻击包括 Dexible 和 Hector Bridge。 2023 年 2 月 17 日,去中心化交易所 Dexible 被攻击,损失超过 150 万美元。 漏洞利用者向 Dexible 的 fill() 函数输入恶意 calldata,以窃取用户资产。 2023 年 6 月 2 日,Hector 网络的协议被攻击。攻击者部署了一个虚假的 USDC合约,并通过恶意 calldata,将 65.2万枚真实的USDC从受害者的合约中转移出去。
区块链聚合平台通常通过封装一系列桥和路由合约来提高流动性,减少损耗。然而,这种复杂的封装会给安全性带来更多难题。我们欣慰地看到Socket此次事件可以得到解决,CertiK将继续致力于为平台提供全方位审计与检测,降低各类聚合风险,提高社区信任和整个行业的安全水平。
The attacker took advantage of the loopholes in the data verification link in a contract and stole the user's funds of the authorization contract through malicious data input. The attack brought the biggest loss to an address, with the loss of about $10,000. Background introduction is an interoperability agreement that serves the cross-chain safe and efficient data and asset transmission. The contract is an access point that interacts with all the assets in the liquidity layer, and all the assets bridges are gathered here into a unique meta-bridge according to the users. Preferences, such as cost delay or security, choose the best transaction route. Three days before the hacker attack, the contract administrator executed an order to add a new route to the system. The purpose of adding a route is to expand the function of the gateway, but it inadvertently introduced a key loophole. The following picture shows the record of adding a route through the contract administrator. The summary of the incident is Beijing time. Our time analysis shows that the funds used by the attacker's wallet to transfer to the attack are related to the withdrawal from. These funds were used to create. And two contracts were executed to exploit the vulnerability. The first contract was aimed at the screenshot in the authorized address, and the following victim was defrauded of about ten thousand dollars. Then the second contract targeted the sum in the victim's address, so another victim lost the following assets. The attacker converted the sum into the vulnerability source, and the vulnerability exploited by the attacker existed in the function in the newly added routing address. The original function of the function in the address was to assist the sum, but one appeared in the function. Key vulnerability users directly call external data in without verification, which means that the attacker can execute any malicious function. In this incident, the attacker made a malicious input trigger function, which took advantage of the user's authorization to the contract and stole funds from them. Although the contract will check the balance to ensure that the user's balance will change correctly after the call, this function does not consider the situation that the attacker sets the amount to. Attacking the contract, the attacker used the hex signature to call the vulnerable routing address contract in the contract. In the screenshot below, we can see that the number of false inputs used by the attacker is all for the next call, which was falsely accepted and executed without any verification. The attacker repeatedly executed the above process until the victim ran out of assets and malicious transactions appeared, and quickly called the previously vulnerable route to prevent a wider range of attacks. Recover the pieces and announce on the day that all losses will be fully compensated. This incident has been resolved. It is not uncommon for malicious attacks to be found in routing contracts with unlimited user authorization. Similar attacks in the past included attacks on decentralized exchanges on the day of the month, and losses of more than $10,000. Explorers maliciously entered functions to steal users' assets. On the day of the month, the protocol of the network was attacked. The attacker deployed a false contract and maliciously transferred 10,000 pieces from the victim's contract. Blockchain aggregation platforms usually improve liquidity and reduce losses by encapsulating a series of bridges and routing contracts. However, this complex encapsulation will bring more difficulties to security. We are pleased to see that this incident can be solved and will continue to work hard to provide all-round audit and testing for the platform, reduce various aggregation risks and improve community trust and the security level of the whole industry. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。



















