UTXO同构绑定技术——扩容的新圣杯
作者:DaPangDun 来源:X,@DaPangDunCrypto
“UTXO同构绑定技术”是我认为这一轮BTC生态发展中一个十分重要的创新,我曾多次表明该技术的重要性及创新性。然而,我发现很多人对于该项技术的意义依然不了解,这里面有技术认知的问题,也有意识形态的问题,所以写此文专门阐述一下我对于这项技术的认知脉络和判断。
一、BTC拓展的必要性
让我们先来思考这样一个问题:BTC为什么需要扩展?
这个问题的涉及的是--BTC网络拓展的必要性这个核心问题,如果没有必要,那么整个生态其实都是伪命题。
我们可以从很多方面来解释这个问题,比如:
1)BTC的减半周期,矿工收益下降,需要更多的链上活动来提升收入从而维持网络安全,而更多的链上活动就需要拓展生态来促发;
2)BTC网络的TPS很低,无法满足很多场景的使用需求,需要有一种手段来进行拓展,让网络更加的有力;
3)BTC的网络费用很贵,不方便大规模普及,特别是随着BTC价格的水涨船高,与普通人之间的距离也越来越远,会偏离最开始的初衷;
4)BTC网路能提供的操作码非常有限,仅能实现非常少的功能定义或组合操作,且脚本语言是非图灵完备的,极其难实现智能合约,因此需要一种方法让其具备这样的特性;
5)BTC是数据是完全公开的,虽然可以采用类似于HDWALLET等技术来提供一定程度的隐私,但是在绝大部分情况下都是有迹可查的,缺乏隐私性,因此需要一种方法来增强其隐私性;
6)......
事实上,如果要写,您会发现会有非常多的理由,也许有的理由并不是那么充分,但是这些都反映出一个问题,即:BTC网络确实需要拓展!
二、BTC拓展的常见选项
一般的拓展会选择其中的一项或者几项作为目标,然后设计出方案实现这样的目标。以常见的拓展方案为例:
1)侧链的思路就是自己打造一条链,大多数是通过多签的形式来锚定BTC,然后在自己链上有自己的共识机制,加入一些自己的特殊设定环节来实现对应功能。像Liquid就增加了脚本操作码、资产发行功能还有隐私资产的概念;
2)闪电网络的思路是利用逻辑算法来实现一个链下的安全快速交互,实现大规模普及支付的可能性;
3)客户端验证的思路是采用一次性密封技术和链下技术来把数据放在链下进行运算,这样就同时具备了主网安全性继承和智能合约的能力;
4)铭文类的思路是基于UTXO来进行有限的处理,实现发行资产的功能,并根据情况来实现其他增强功能;
5)兼容EVM等的思路大多数是异化的多签桥作为起点,然后用类似于侧链的结构来构建一条兼容EVM的链,在这条链上利用EVM上成熟的经验来构筑Dapp等实现落地应用;
6)模块化的思路是参考EVM系的发展路径,对于BTC拓展中的可能用到的部分进行模块化,比如DA层等;
7)Bitvm的思路是就利用这有限的操作码通过类似于“电路”的思路来构建复杂的功能;
8)......
当然,还有其他的技术路线,新的创意(大多数是微创新)也在不停的推出,但是大体上当我们了解这些脉络之后,能够相对快速的判断一个新思路的核心内涵。
在这些拓展上,演变了非常多的争论。当然,crypto中永远存在着争论,比如“正统和非正统”之争,“原生性和非原生性”之争,“是否应当利用BTC当作Gas”之争,“长期性和落地性”之争等等,有的甚至演变成了社区之间的冲突。从一个技术研究者的角度来说,我认为“大可不必”,很难有人可以100%预见到未来的结果,所以遵从自己的价值判断来选择认可的技术路线即可。
三、UIB的横空出世
在诸多路线中,跨链桥的形式因其“安全性”受到一定的质疑,一层资产协议因其基于UTXO上的拓展开发能力有限而备受苦恼,Bitvm因其偏向复杂的建设周期而需要等待,兼容EVM又被很多BTC圈内人士认为正统性太差。
是否有一种方法,既能体现原生性,有能保证安全性,还能具有较高拓展性呢?
这就是UIB,全称:UTXO ISOMORPHIC BINDING
这项技术利用了UTXO模型的同源特性,通过“一次性密封”的方式,可以将目标链A的UTXO映射到另外一条图灵完备的UTXO链B。
这项技术由Cell Studio的创始人Cipher提出并具体实践在CKB上。
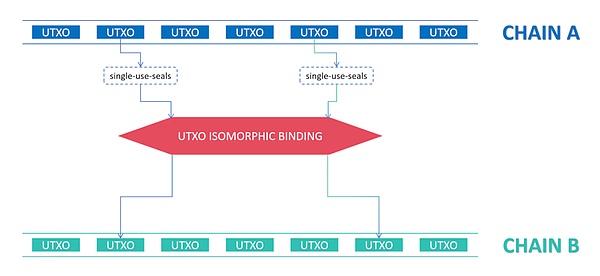
我们来仔细看这样一个概念描述:
1)首先双方都必须是基于UTXO的,这点毋庸置疑;
2)A链原则上来说可能是非图灵完备的,否则他可以在本链上进行拓展;当然,即使是图灵完备的,这种同构方式也可以实现原生的资产映射;
3)B链需要是图灵完备的,因为映射的过程需要B链的约束来验证状态计算的正确性和变更所有权的有效性;
4)原则上来说,基于A链的资产发行协议都可以采用同构的形式做这样的映射;
请仔细阅读上面的四条,然后你会发现“UIB的横空出世”这个描述并不是夸张!
1)从原生性上来说,他没有任何的跨链桥的方式,非常原生;
2)在解析上,B链提供了一个公开的DA层来为其他模块的构建提供基础;
3)从安全性上,有可能实现与A链等同的安全性(当然这部分我不是特别确定,虽然有相关的理论说明)
4)从拓展性上,完全承接了B链的拓展性性能;
也就是说:UIB让你可以在【原生性】【安全性】【拓展性】上找到了一个绝佳的平衡点
当然,他的限制是:你需要有这样的B链,还要有实现协议需要的各种组件代码。
四、UIB的叙事空间
UIB在BTC生态中大有可为
它可以让具有B链特性的公链成为BTC的L2,资产通过原生的方式进行映射,映射之后在B链上进行各种拓展开发。
具体脉络如下:
1)以最近很火的RGB++为例,就是一个新的一层资产协议,可以通过UIB来映射在CKB上。同时,二层资产也可以通过LEAP的方式同构成一层资产,提升正统性。

2)更进一步,BTC主网上的其他一层资产协议也可以通过UIB的方式同构到CKB网络。这会极大的激活当前各种一层资产协议中沉淀的资金,使其有更多的使用场景和玩法。
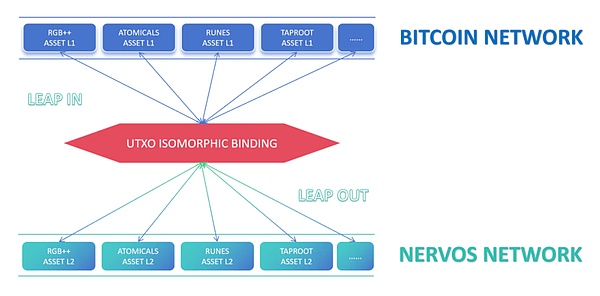
UIB可以连接其他UTXO链
再进一步,是否有其他网络也可以代替CKB网络呢?当然可以,UIB是可以独立于CKB而作为一个中间层协议的。我们可以将上面的各种资产协议同构到其他的图灵完备的UTXO链,每一条链都能完善和扩充UIB技术协议。

接着进一步,我们不只是BTC网络上有一层资产,其他很多UTXO链也有一层资产协议,他们上面沉淀的资金或社区虽然没有BTC网络那么大,但是整体上也是一股巨大的力量,但是受限于早期架构的设计,这些网络中大部分也没有图灵完备的能力,它们也会成为UIB技术应用的场景用例。通过这种方式,UIB技术实现了UTXO世界中各条链资产之间的原生联结。
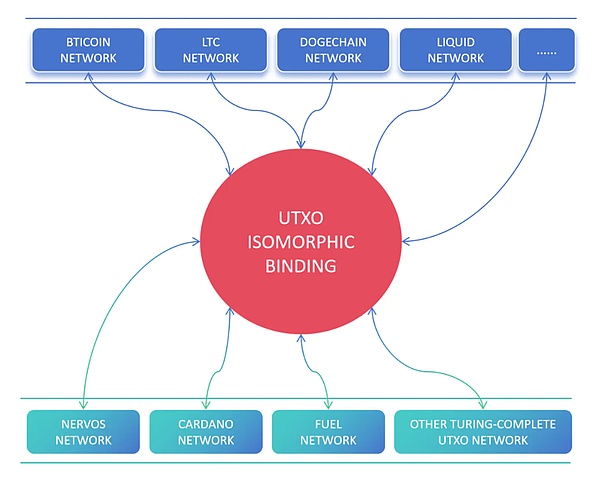
那么,这里的OTHER TURING-COMPLETE UTXONETWORK有哪些呢?
1)显然,最近公布融资的UTXO STACK就是其中的一部分;利用UTXO STACK可以一键部署同源于CKB架松的链,这些链天生就可以利用上UIB的技术,通过共享CKB网络安全性的方式,将CKB网络推上诸如COSMOSHUB的位置(我不确定我的这个说法是否合适);
2)会有越来越多的具备图灵完备的UTXO网络推出,这些网络通常会具有自己的独特特性来实现某些维度的极度特征化以适应其独特的定位属性;
3)借鉴这个思路,也会有基于其他网络的UTXOSTACK,他们服务于于其他网络自身来拓展生态圈并提升主要网络的地位;
这个族群会越来越大,这也会让UIB技术得到越来越广泛的采用。
所以,你看清这个脉络了吗?!
五、所以,UIB是什么?
所以,现在再来看UIB,您认为它是什么?
它是一个中间层,可以同构各个UTXO世界中的一层资产到二层让其进入智能合约的时代!
它是一个通用技术,可以用在UTXO世界中的很多地方,将各个分离的小世界联系起来!
它是一项在BTC生态发展中的一个重要的创新!
它是UTXO世界新的圣杯!
The author's source isomorphism binding technology is a very important innovation in this round of ecological development. I have repeatedly indicated the importance and innovation of this technology. However, I found that many people still don't understand the significance of this technology. There are both technical cognition problems and ideological problems, so I wrote this article to explain my cognitive context and the necessity of judging the expansion. Let's first think about why such a problem needs to be expanded. It is the core problem of the necessity of network expansion. If it is not necessary, then the whole ecology is actually a false proposition. We can explain this problem from many aspects. For example, the decline of miners' income in half cycle requires more chain activities to improve their income, so as to maintain network security. More chain activities need to expand the ecology to promote the low level of the network, which cannot meet the needs of many scenarios. It is necessary to have a means to expand the network and make it more powerful. The network cost is very expensive and inconvenient. Large-scale popularization, especially with the rising price, will deviate from the original intention. The operation code that the network can provide is very limited, and only a few function definitions or combination operations can be realized. Moreover, the scripting language is not Turing, and it is extremely difficult to realize smart contracts. Therefore, a method is needed to make it have such characteristics that the data is completely open. Although similar technologies can be used to provide a certain degree of privacy, it is in most cases. In fact, if you want to write it, you will find that there are many reasons, maybe some reasons are not so sufficient, but these all reflect a problem, that is, the network really needs to expand. The general expansion will choose one or several of them as the goal, and then design a plan to achieve this goal. Take the common expansion plan as an example. The idea of the side chain is to build a chain by itself. Anchor in the form of multi-signing, and then have their own consensus mechanism on their own chain, and add some special setting links to realize the corresponding functions, such as adding script operation code, asset distribution function and the concept of privacy assets. The idea of lightning network is to use logical algorithm to realize safe and rapid interaction under a chain, and realize the possibility of large-scale universal payment. The idea of client verification is to use one-time sealing technology and offline technology to put data under the chain for operation, so that it can have both. The idea of the inscription class is based on the limited processing to realize the function of issuing assets and the compatibility of other enhanced functions according to the situation. Most of the ideas are alienated multi-sign bridges as the starting point, and then a compatible chain is built with a structure similar to the side chain, and the mature experience is used to build a modular landing application. The idea is the development path of the reference system, and the possible parts in the expansion are modular. The idea of layering, for example, is to use this limited opcode to build complex functions through ideas similar to circuits. Of course, there are other technical routes, and most new ideas are micro-innovations, but in general, after we understand these contexts, we can judge the core connotation of a new idea relatively quickly, and there are many debates in these developments. Of course, there will always be debates, such as whether the dispute between orthodoxy and unorthodoxy and the dispute between originality and non-originality should be beneficial. From the point of view of a technical researcher, I think it is unnecessary for anyone to foresee the future results, so following their own value judgment to choose the recognized technical route can turn out to be three. Among many routes, the form of cross-chain bridge is questioned to some extent because of its security, and the first-layer asset agreement is distressed because of its limited ability to expand and develop based on it, because of its bias towards complex construction. Setting a cycle but waiting for compatibility is considered by many insiders to be too unorthodox. Is there a method that can not only reflect the original nature, but also ensure the safety and high expansibility? This is the full name. This technology makes use of the homologous characteristics of the model and can map the target chain to another Turing complete chain through one-time sealing. This technology was put forward by the founder and put into practice. Let's take a closer look at such a concept description. First of all, both parties must be based on this point. There is no doubt that the chain may be non-Turing complete in principle, otherwise it can be expanded on this chain. Of course, even Turing complete isomorphism can realize the original asset mapping chain, because the mapping process needs chain constraints to verify the correctness of state calculation and the effectiveness of changing ownership. In principle, chain-based asset issuance agreements can adopt isomorphic form to make such mapping. Please read the above four items carefully and then you will find the horizontal. The description of being born is not an exaggeration. From the original point of view, it does not have any way to cross the chain bridge. It is very original. From the analytical point of view, the chain provides an open layer to provide a foundation for the construction of other modules. It is possible to achieve the same security as the chain from the security point of view. Of course, I am not particularly sure about this part. Although there are relevant theories that completely undertake the expansibility of the chain, that is to say, you can find an excellent balance point in the extensibility of the original security. His limitation is that you need to have such a chain and all kinds of components needed to realize the agreement. The narrative space of code four is promising in ecology. It can make the assets of the public chain with chain characteristics be mapped in the original way and then carry out various expansion and development on the chain. The specific context is as follows: Take the recent hot one as an example, a new layer of asset agreement can be mapped on the top, and at the same time, the second layer of assets can also form a layer of assets to further enhance legitimacy. Other layer asset agreements on the main network can also be isomorphic to the network in a way, which will greatly activate the funds deposited in various current layer asset agreements, so that they can have more usage scenarios and play methods to connect with other chains. Further, is there any other network that can also replace the network? Of course, it can be independent as an intermediate layer agreement. We can isomorphize the above asset agreements to other Turing complete chains, and each chain can improve and expand the technical agreements. Then, we not only have one layer asset on the network, but also many other chains have one layer asset agreement deposited on them. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。