SharkTeam:Prisma Finance被攻击事件分析
2024年3月28日,Prisma Finance遭受闪电贷攻击,项目方损失约1221万美元。

SharkTeam对此事件进行了技术分析,并总结了安全防范手段,希望后续项目可以引以为戒,共筑区块链行业的安全防线。
一、攻击交易分析
攻击者1:0x7e39e3b3ff7adef2613d5cc49558eab74b9a4202(简记为0x7e39)
攻击合约1:0xd996073019c74b2fb94ead236e32032405bc027c(简记为0xd996)
攻击者2:0x7fe83f45e0f53651b3ed9650d2a2c67d8855e385
攻击合约2:0x4148310fe4544e82f176570c6c7b649290a90e17
被攻击的目标合约:0x1cc79f3f47bfc060b6f761fcd1afc6d399a968b6
攻击包含16笔交易,以第一笔攻击交易为例:
0x00c503b595946bccaea3d58025b5f9b3726177bbdc9674e634244135282116c7
攻击流程如下:
1. 读取地址0x56a201b872b50bbdee0021ed4d1bb36359d291ed(简记为0x56a2)在目标合约中的所有抵押物和债务。
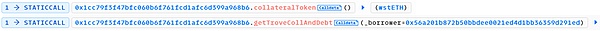
返回结果如下:
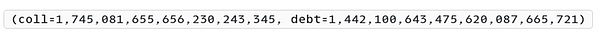
地址0x56a2在目标合约中抵押物共有1,745 wstETH,总债务共有1,442,100 mkUSD。
2. 攻击者0x7e39通过攻击合约0xd996调用mkUSD债务合约中的flashLoan函数。
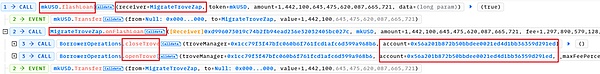
参数receiver设置为MigrateTroveZap,amount为上面查询到的全部债务。

然后,在flashLoan函数中会调用receiver(这里是MigrateTroveZap)中的onFlashLoan函数。
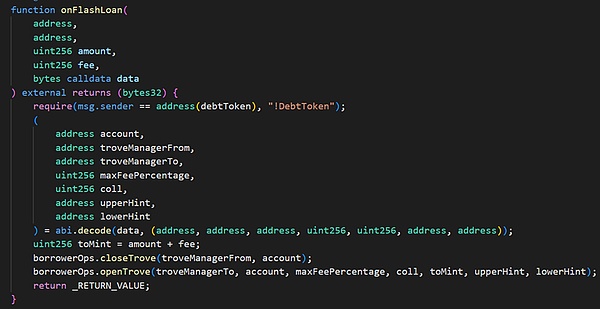
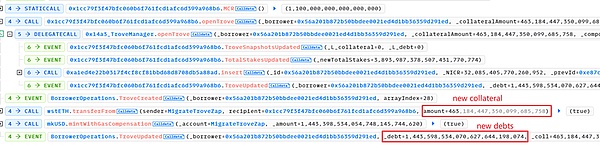
onFlashLoan函数通过闪电贷先偿还原来的所有债务,提取抵押物到receiver,然后receiver将一定数量的抵押物重新抵押,并借取一定的债务。其中主要调用了2个函数:
(1)closeTrove函数,偿还债务并将所有的抵押物(1745.08 swtETH)从troverManager提取到receiver(这里是MigrateTroveZap合约);
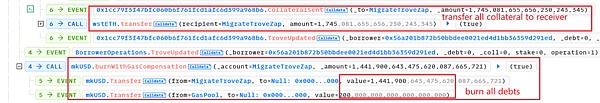
(2)openTrove函数,由receiver将463.18 wstETH重新抵押到troverManager中,并负债1,443,598 mkUSD。
从上面数据可以看出,flashLoan函数执行完成后,receiver中仍然保留了从troverManager中提取的属于地址0x56a2的抵押物,数量约为1745.08 – 463.18 = 1281.90 wstETH。
3. 攻击者0x7e39通过攻击合约0xd996从Balancer中通过闪电贷借取了1 wstETH。
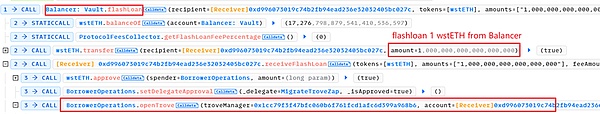
然后,抵押1 wstETH并借取债务2000 mkUSD,加上fee,共计负债2200 mkUSD。
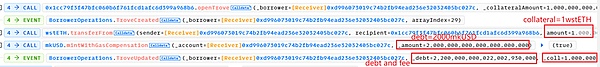
4. 与步骤2类似,调用mkUSD债务合约中的flashLoan函数,这里参数receiver仍然设置为MigrateTroveZap,amount为上一笔质押1 wstETH后的全部债务,即2000 mkUSD。在FflashLoan函数中会调用receiver中的onFlashLoan函数,然后调用closeTrove和openTrove函数。

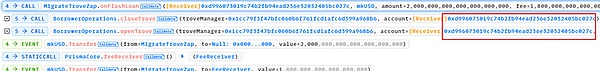
只是,这里closeTrove和openTrove函数中的参数account不再是上面的地址0x56a2,而是质押了1 wstETH的攻击合约0xd996。
(1)closeTrove函数,偿还债务并将所有的抵押物(1 swtETH)从troverManager提取到receiver(这里仍然是MigrateTroveZap合约)。此时receiver中共有1281.90 +1=1282.90 wstETH.
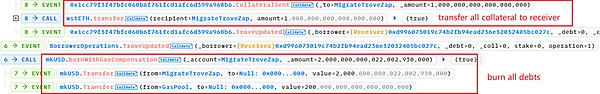
(2)openTrove函数,由receiver将1282.80 wstETH(几乎全部)重新抵押到troverManager中,并负债2001.8 mkUSD。
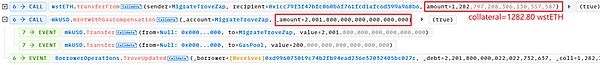
实际上,这里抵押物中1281.80 wstETH是不属于攻击合约0xd996,而是属于上面的地址0x56a2。
5. 最后,攻击者0x7e39通过攻击合约0xd996单独调用closeTrove函数,将抵押的1282.80 wstETH 提取到了攻击合约0xd996中。
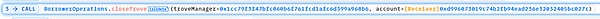
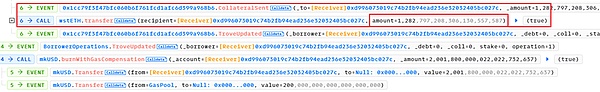
偿还闪电贷后,攻击者仍获利1281.80 wstETH,约2.30M USD。
二、漏洞分析
本次事件的根本原因是项目合约存在逻辑和权限校验,使得攻击者可以利用该漏洞获取其他账户地址的质押资产。
攻击者最终获得的wstETH是原本地址0x56a2在troverManager合约中的抵押物,通过mkUSD合约的flashLoan函数,自定义MigrateTroveZap合约中onFlashLoan函数的参数,利用 MigrateTroveZap将其转变为攻击合约的抵押物,然后将其提取出来。
攻击者通过mkUSD合约中的flashLoan函数以及MigrateTroveZap合约中的onFlashLoan函数操纵其他账户地址的抵押和提取。

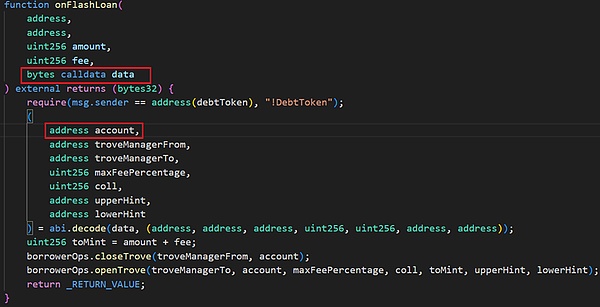
(1)flashLoan函数中缺少对参数receiver地址的校验,因为onFlashLoan函数中receiver会接收account的所有抵押物,因此需要对receiver进行可信的校验;
(2)onFlashLoan函数中缺少对account地址的校验,因为closeTrove和openTrove函数都是操作的account的资产,因此需要对account增加权限方面的校验;
除了对这两个地址参数的校验外,可能还需要对flashLoan函数中的数量参数以及实现逻辑进行校验。
三、安全建议
针对本次攻击事件,我们在开发过程中应遵循以下注意事项:
(1)项目在设计和开发过程中,要保持逻辑的完整性和严谨性,尤其是涉及到资产的转移过程中,更要加强对函数调研权限的校验,保证调用者、调用函数、函数参数、转账逻辑等都是安全可信的。
(2)项目上线前,需要找专业的第三方审计团队进行合约审计。
About Us
SharkTeam的愿景是保护Web3世界的安全。团队由来自世界各地的经验丰富的安全专业人士和高级研究人员组成,精通区块链和智能合约底层理论。提供包括风险识别与阻断、智能合约审计、KYT/AML、链上分析等服务,并打造了链上智能风险识别与阻断平台ChainAegis,能有效对抗Web3世界的高级持续性威胁(Advanced Persistent Threat,APT)。已与Web3生态各领域的关键参与者,如Polkadot、Moonbeam、polygon、Sui、OKX、imToken、Collab.Land等建立长期合作关系。
官网:https://www.sharkteam.org
Twitter:https://twitter.com/sharkteamorg
Telegram:https://t.me/sharkteamorg
Discord:https://discord.gg/jGH9xXCjDZ
The project party suffered a lightning loan attack on October, and the loss was about USD 10,000. This incident was analyzed technically and the security precautions were summarized. I hope that the follow-up projects can take it as a warning to build a security line for the blockchain industry. An attack transaction analysis: The attacker's brief description is the attack contract brief description is the attacker's attack contract. The attack on the attacked target contract includes a transaction. Take the first attack transaction as an example. The attack process is as follows: Read the address brief description as all the collateral and debts in the target contract. The return results are as follows. In the target contract, the collateral has a total debt. The attacker calls the function parameter in the debt contract by attacking the contract and sets it to all the debts queried above. Then, the function in the function will be called to repay all the original debts by lightning loan, and then a certain amount of collateral will be mortgaged again and a certain amount of debts will be borrowed. Among them, a function function is mainly called to repay the debts and extract all the collateral from here, which is the contract function. Re-mortgaging into the consolidated debt can be seen from the above data that the amount of collateral belonging to the address still remains after the function is executed, which is about the amount of collateral that the attacker borrowed from the contract through lightning loan, and then mortgaged and borrowed the debt and added the total debt, which is similar to the steps of calling the function in the debt contract. The parameters here are still set to all the debts after the last pledge, that is, the function in the function will be called, and then the sum function will be called, but the parameters in the sum function here are no longer. The above address is the pledged attack contract function to repay the debt and extract all the collateral from here, which is still a contract. At this time, there are functions to re-mortgage almost all the collateral into the debt. In fact, the collateral here does not belong to the attack contract, but belongs to the above address. Finally, the attacker called the function separately through the attack contract to extract the mortgage into the attack contract. After repaying the lightning loan, the attacker still made a profit. The root cause of this incident is the existence of the project contract. In the logic and authority verification, the attacker can use this vulnerability to obtain the pledged assets of other account addresses. What the attacker finally gets is the collateral whose original address is in the contract. The function of the contract defines the parameters of the contract and transforms it into the collateral that attacks the contract, and then extracts it. The attacker manipulates the mortgage and extraction function of other account addresses through the function in the contract and the function in the contract, because there is a lack of verification of the parameter address. There is collateral, so it is necessary to check the address in the credible check function, because the sum function is an operational asset, so it is necessary to check the increase of authority. In addition to the check of these two address parameters, it may also be necessary to check the quantitative parameters and implementation logic in the function. Third, security suggestions. For this attack, we should follow the following precautions in the development process. The project should maintain the integrity and rigor of logic in the design and development process, especially involving In the process of transferring assets, it is necessary to strengthen the verification of function research authority to ensure that the caller calls function parameters, transfer logic and so on are safe and credible. Before the project goes online, it is necessary to find a professional third-party audit team to conduct contract audit. The vision is to protect the world's security team, which is composed of experienced security professionals and senior researchers from all over the world. They are proficient in blockchain and intelligent contract underlying theory, and provide services including risk identification and blocking, intelligent contract audit chain analysis and so on. And built an intelligent risk identification and blocking platform on the chain, which can effectively fight against the world's advanced persistent threats, and has established long-term cooperative relations with key participants in various fields of ecology, such as official website. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。

















