校验缺失 —— 借贷项目 SenecaUSD 安全事件分析
北京时间2024年2月28日,据Beosin trace资金分析平台显示,ETH链上的SenecaUSD项目合约存在漏洞,黑客利用精心构造的calldata参数,调用transferfrom将授权到该项目合约的代币转移到自己地址上,最后兑换为ETH。目前黑客已归还80%资金,剩余20%用作白帽奖励。以下是Beosin对此次攻击事件的分析。
漏洞分析
Seneca项目合约中存在一个performOperations函数,该函数传入的参数来选择执行不同的函数逻辑。
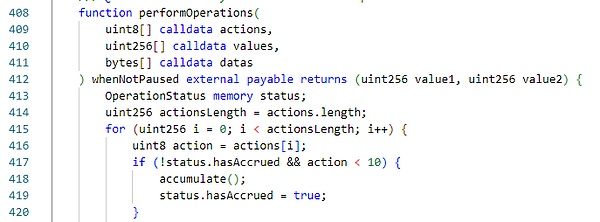
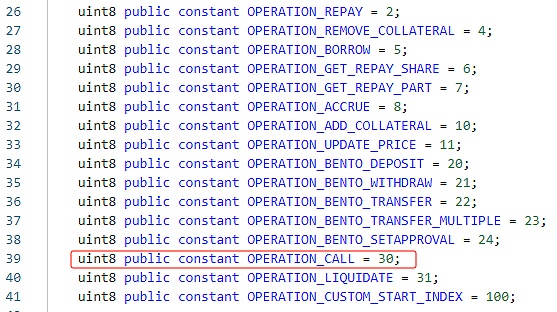
可以看到,当用户指定action为30时,函数将选择调用_call函数,并且传入用户指定的调用参数。
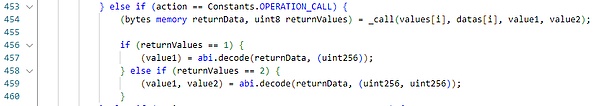
_call函数只检查了一下调用地址的黑名单,随后便直接调用了用户指定地址的指定函数,期间并未对调用者以及调用参数做任何限制性检查。
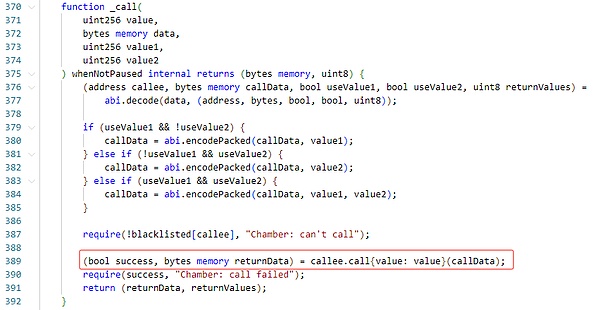
如果调用者在这里构造非法的调用数据,便可能导致攻击事件的发生。
攻击流程
本次事件攻击者通过多次相同的手法进行攻击,这里以0x23fcf9d4517f7cc39815b09b0a80c023ab2c8196c826c93b4100f2e26b701286这笔交易为例。我们来看看此次攻击者是如何构造调用数据以及实施攻击的。
1. 攻击者直接调用performOperations函数,并构造了以下参数,其中actions传入了上述的30,将调用_call函数。
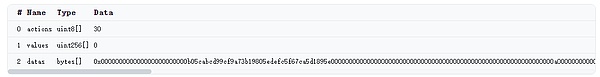
2. Datas数据为:
0x000000000000000000000000b05cabcd99cf9a73b19805edefc5f67ca5d1895e
00000000000000000000000000000000000000000000000000000000000000a0
0000000000000000000000000000000000000000000000000000000000000000
0000000000000000000000000000000000000000000000000000000000000000
0000000000000000000000000000000000000000000000000000000000000000
0000000000000000000000000000000000000000000000000000000000000064
23b872dd0000000000000000000000009cbf099ff424979439dfba03f00b5961
784c06ce00000000000000000000000094641c01a4937f2c8ef930580cf39614
2a2942dc00000000000000000000000000000000000000000000004b180b8661
8eddc3ab00000000000000000000000000000000000000000000000000000000
根据解析规则来看,第一个32字节为callee=0xb05cabcd99cf9a73b19805edefc5f67ca5d1895e。
第二个callData在a0处,100(0x64)字节,则得到
callData为:
0x23b872dd0000000000000000000000009cbf099ff424979439dfba03f00b5961784c06ce00000000000000000000000094641c01a4937f2c8ef930580cf396142a2942dc00000000000000000000000000000000000000000000004b180b86618eddc3ab
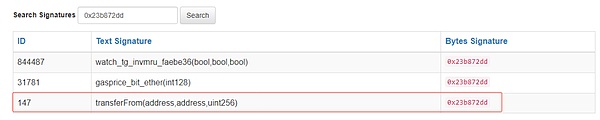
3. 查询函数选择器,根据callData数据可知,callData指定的是transferFrom函数。那本次调用我们可以解析出来为:
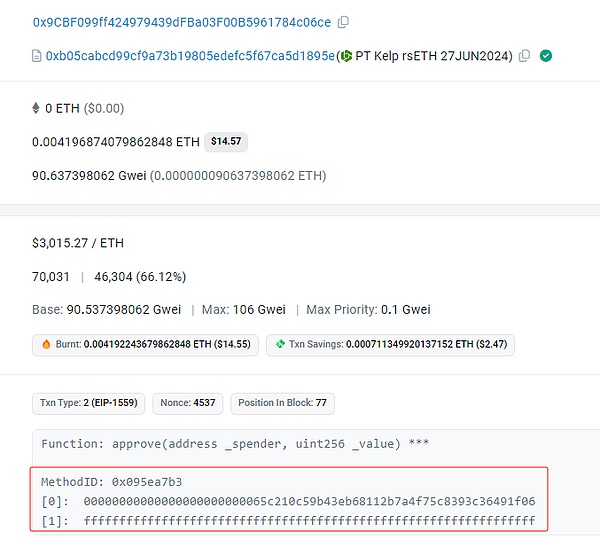
0xb05cabcd99cf9a73b19805edefc5f67ca5d1895e.transferFrom(0x9cbf099ff424979439dfba03f00b5961784c06ce,0x94641c01a4937f2c8ef930580cf396142a2942dc,1385238431763437306795)。
4. 由于在之前的交易中,0x9cbf099ff424979439dfba03f00b5961784c06ce向0x65c210c59b43eb68112b7a4f75c8393c36491f06地址授权过最大值,所以这里攻击者通过transferFrom函数直接将0x9cbf099ff424979439dfba03f00b5961784c06ce的超1385枚PT-rsETH-27JUN2024(0xb05cabcd99cf9a73b19805edefc5f67ca5d1895e)代币转移到自己的地址上。
5. 随后攻击者将PT-rsETH-27JUN2024代币兑换为ETH。
资金追踪
在被攻击后,Seneca部署者向攻击者喊话,要求攻击者归还资金,并表示可以保留20%的资金作为白帽奖励。
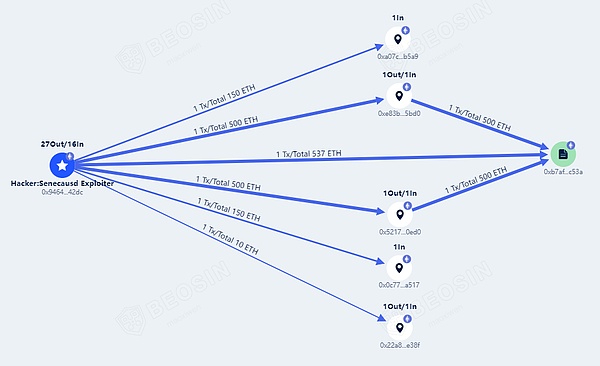
据Beosin trace资金追踪平台显示,截止发稿,攻击者已将被盗1900多枚ETH中的1537枚ETH(80%)归还到部署者指定地址,剩余370枚ETH(20%)分散保留在攻击者地址上。
According to the capital analysis platform, Beijing time, there is a loophole in the project contract on the chain. Hackers use carefully constructed parameter calls to transfer the tokens authorized to the project contract to their own addresses, and finally exchange them for the funds that have been returned by hackers at present. The following is an analysis of the attack. Vulnerability analysis shows that there is a function in the project contract, and the parameters passed in by this function are used to select and execute different function logic. It can be seen that when the user specifies as, the function will choose to call the function and And the function that passed in the user-specified call parameters only checked the blacklist of the call address, and then directly called the specified function at the user-specified address. During this period, no restrictive check was made on the caller and the call parameters. If the caller constructs illegal call data here, it may lead to an attack event. The attacker attacked this event by the same method many times. Let's take this transaction as an example to see how the attacker constructs the call data this time. And the attacker who carried out the attack directly called the function and constructed the following parameters, in which the above-mentioned data of calling the function was passed in. According to the analysis rules, the first byte was the second byte, and then it was obtained as the query function selector. According to the data, it was known that the specified function was the function. Then we can analyze this call as the attacker directly transferred the super token to his own address through the function, and then the attacker transferred the token. After being attacked, the deployer shouted to the attacker to ask the attacker to return the funds and said that the funds that can be kept were used as white hat rewards. According to the fund tracking platform, as of press time, the attacker had returned one of the stolen pieces to the address designated by the deployer, and the remaining pieces were scattered at the attacker's address. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。