跌宕起伏 Blast生态Munchables遭黑客攻击分析
2022年3月27日,据Beosin KYT反洗钱分析平台监测,Blast 生态Web3 游戏平台 Munchables 遭遇黑客攻击,黑客获利约17,413.96ETH,损失超6200W。
据了解,Munchables 是Blast Big Bang 获奖项目,近期还刚宣布完成Manifold 和 Mechanism Capital 共同领投的 Pre-Seed 轮融资。
Munchables 公布遭受攻击后,其TVL从9600万美元大幅下跌至3400多万美元。关于本次事件,Beosin安全团队第一时间进行了分析。

● 攻击交易
https://blastexplorer.io/tx/0x3d08f2fcfe51cf5758f4e9ba057c51543b0ff386ba53e0b4f267850871b88170
https://blastexplorer.io/tx/0x9a7e4d16ed15b0367b8ad677eaf1db6a2a54663610696d69e1b4aa1a08f55c95
● 攻击者地址
0x6e8836f050a315611208a5cd7e228701563d09c5
● 被攻击合约
0x29958e8e4d8a9899cf1a0aba5883dbc7699a5e1f
漏洞分析
此前,链上侦探ZachXBT针对此次攻击的原因调查后表示,Munchables 被盗或因雇佣了伪装成开发者的朝鲜黑客。
ZachXBT说道:“Munchables 团队雇佣的四名不同的开发人员与漏洞利用者有关联,他们很可能是同一个人。他们相互推荐工作、定期向相同的两个交易所存款地址转账,以及为彼此的钱包充值。”
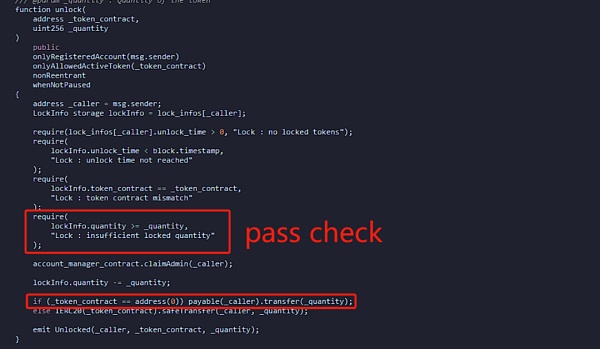
Beosin安全团队分析之后发现本次攻击主要是朝鲜黑客开发者合约利用合约升级功能,预先将自己的抵押账本进行了设置,随后在合约积累资金后,通过调用unlock函数提出了合约中的ETH。
攻击流程
攻击准备阶段:
黑客开发者预先创建含有后门的实现合约0x910fFc04A3006007A453E5dD325BABe1e1fc4511并将黑客自己的抵押账本预先设置为极大值。
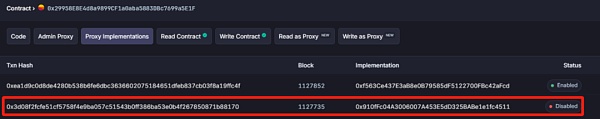
攻击阶段:
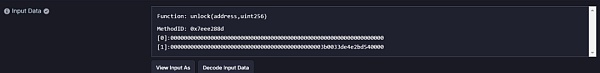
攻击者调用unlock函数取出ETH,由于在攻击准备阶段黑客已经设置了抵押账本,检查很简单地被绕过。
被盗之后,Munchables在社交媒体上对其此前发布的共享私钥公告进一步解释称,共享私钥是为了协助安全人员追回用户资金。具体来说,是包含持有62,535,441.24美元加密资产的私钥、持有73 WETH 的私钥以及包含其余资金的所有者私钥。
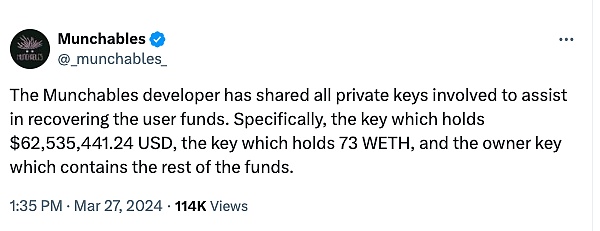
正在项目方以及用户们焦虑的时候,北京时间下午 14 时,Munchables 攻击者向某多签钱包退还了所有的 1.7 万枚 ETH。
截止发文时,被盗资金已退回并发往多签了合约。
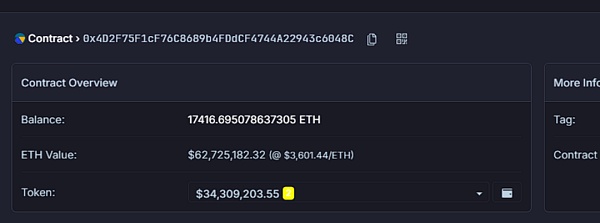
半小时后,Blast 创始人 Pacman 于 X 平台公告,Blast 核心贡献者已通过多重签名获得 9700 万美元的资金(分别为被盗的 1.74 万枚 ETH 和协议内剩余未被取走的 9450 枚 wETH,目前价值 9600 万美元)。感谢前 Munchables 开发者选择最终退还所有资金,且不需要任何赎金。Munchables 也转发此公告表示:“所有用户资金都是安全的,不会强制执行锁定,所有与 Blast 相关的奖励也将被分配。未来几天将进行更新。”
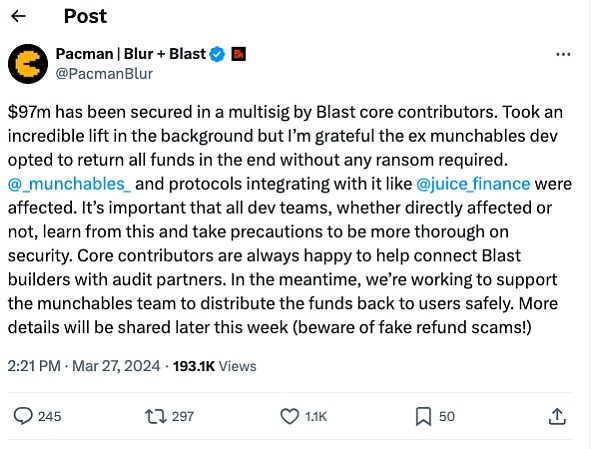
同时此前同步受到 Munchables 攻击事件影响的 Juice 也宣布了资金的安全,其所有的 wETH 均已从 Munchables 开发者手中取回,Jucie 正在与 Pacman 和 Blast 协调将 wETH 转移回 Juice,以便用户能够提款。
整个事件的峰回路转令人意外,尽管我们暂时还不知道黑客退还资金的原因,但这次经历再次敲响了安全的警钟,也让我们深刻认识到安全的重要性。
According to the monitoring of anti-money laundering analysis platform, the eco-game platform was attacked by hackers. It is understood that the winning project has just been announced recently. After the attack, it has dropped sharply from $10,000 to more than $10,000. About this incident, the security team analyzed the attacker's address at the first time, and the contract vulnerability was analyzed. After investigating the cause of the attack, the chain detective said that it was stolen or hired a DPRK disguised as a developer. Fresh hackers said that four different developers hired by the team were related to the exploiters, and they were probably the same person. They recommended jobs to each other, regularly transferred money to the same two exchange deposit addresses and recharged each other's wallets. After analysis, the security team found that this attack was mainly caused by the North Korean hacker developer's contract using the contract upgrade function to pre-set his mortgage account book, and then called the function to propose an attack flow attack in the contract. In the preparation stage, the hacker developer pre-creates an implementation contract with a back door and pre-sets the hacker's own mortgage account book to the maximum value. In the attack stage, the attacker calls the function to take out. Because the hacker has already set the mortgage account book check in the attack preparation stage, it is simply bypassed and stolen. After that, it is further explained on social media that sharing the private key is to help security personnel recover the user's funds, specifically, it includes the private key holding of US dollar encrypted assets. The private key of and the owner's private key containing the rest of the funds were anxious when the project parties and users were worried. In the afternoon of Beijing time, the attacker returned all 10,000 pieces to a multi-signed wallet. By the time of posting, the stolen funds had been returned and sent to the multi-signed contract. Half an hour later, the founder announced on the platform that the core contributors had obtained 10,000 dollars of funds through multi-signature, namely 10,000 pieces stolen and 10,000 pieces left in the agreement, with a current value of 10,000 dollars. Thanks to the former developers for choosing to finally return all the funds. Without any ransom, this announcement indicates that all users' funds are safe and will not be locked. All related rewards will also be updated in the next few days. At the same time, those affected by the attack have also announced the safety of funds. All of them have been retrieved from the developer and will be transferred back so that users can withdraw money. Although we don't know the reason why hackers return funds for the time being, this experience has once again sounded the alarm bell of security and made us deeply realize the importance of security. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。