如何在自我托管钱包中存储加密资产
了解工作的优点、缺点和逐步设置,以通过自我托管钱包控制您的加密资产。
加密货币格局是动态的,其特点是频繁的代币发行。虽然有些人熟悉比特币等流行的加密货币

比特币
$70,186
以太坊
$3,583
索尔
187 美元
生态系统中不断涌现出无数代币。那些对持有加密货币感兴趣的人有两个主要选择:中心化交易所(CEX)钱包或私人(自我托管)钱包来存储它们,这两种方法都有优点和缺点。
本文将解释自我托管钱包,并分享设置初学者 Trust 钱包以控制您的加密资产的基本步骤。
通过中心化交易所持有加密货币的优点和缺点
中心化交易所(CEX)代表其客户持有加密代币。它符合标准的 Web2 安排,用户创建帐户,在交易所购买和出售代币,并依靠交易所仔细处理他们的帐户及其持有的资产。 CEX 类似于拥有银行或股票经纪账户,但一些相似之处仅此而已。
交易所拥有用户的代币,如果发生黑客攻击或破产等不幸事件,用户将无法追索这些资金。考虑到用户对存款和资产缺乏保护和控制,著名的格言“不是你的钥匙,不是你的硬币”的存在是为了鼓励直接所有权。交换失败并不少见;因此,谨慎的选择是考虑这一现实并避免大量暴露。
然而,CEX 为那些刚接触加密货币的人提供了一个易于访问的切入点,并且可用于购买代币以转移到其他钱包。用户可以在业内信誉良好的交易所之一创建帐户。大多数 CEX 都需要了解你的客户 (KYC)检查,用户需要提供身份证明,经批准后,可以设置他们的帐户来买卖加密货币。用户必须确保启用额外的安全功能,例如双因素身份验证,以确保帐户安全。
什么是私人自我托管钱包?
区块链本质上是公开的,使得任何特定钱包地址拥有的代币对每个人都可见。然而,自我托管钱包是“私密的”,因为用户单独控制对这些代币的访问。
自我托管钱包的独特之处在于,用户拥有使用该地址执行任何交易所需的助记词或私钥。只要用户保证私钥安全,他们就是唯一可以控制钱包中资金的人,即没有第三方可以控制或访问这些资金。
自我托管私人钱包如何运作?
自我托管钱包通常首先为用户的钱包生成一个独特的种子短语,然后用户必须将其安全地存储在安全的地方。这可以是在一张纸上或任何其他介质上。但是,用户应避免将它们作为纯脚本保留在计算机或移动设备上,因为任何有权访问种子短语的人都将完全控制钱包。
自我托管钱包可以采取多种形式,包括浏览器扩展钱包(MetaMask)、桌面应用程序(Exodus)、移动应用程序(Trust Wallet)或硬件钱包(Ledger)。这些钱包通常根据其预期用途和安全级别分为热钱包或冷钱包。
用户浏览器、桌面或手机上的钱包通常被认为是热钱包,因为它们保持与互联网的连接,更容易受到潜在的恶意黑客攻击和安全威胁,而冷钱包(硬件钱包)通常处于离线状态,仅连接到当用户需要执行交易或交互时互联网。高度关注安全性的用户经常以单向交互的方式使用冷钱包,其中硬币被转移到钱包中进行存储,但严格来说,钱包永远不会连接到任何基于互联网的应用程序。
加密钱包的演变
一些钱包正在超越通常的种子短语机制,以带来安全性和简单性,从而有助于扩大采用范围。一些移动钱包提供允许受信任联系人恢复的功能,专注于生物识别安全以保护资产。
此外,某些硬件钱包与移动应用程序配对,并利用芯片卡进行资产保护,强调需要像安全钥匙一样保护芯片卡。此外,多重签名钱包需要多次批准交易,从而增加了一层安全保障,防止未经授权的访问和潜在的欺诈。
开始和设置 Trust Wallet 的关键步骤
Trust Wallet 支持 100 多个区块链。任何人都可以在其移动设备上安装 Trust Wallet,并将其作为笔记本电脑上的浏览器扩展。首先,用户可以访问Apple App Store 或 Google Play Store 并下载移动应用程序。
用户可以按照以下简单步骤创建新帐户:
步骤 1:在移动设备上安装应用程序。
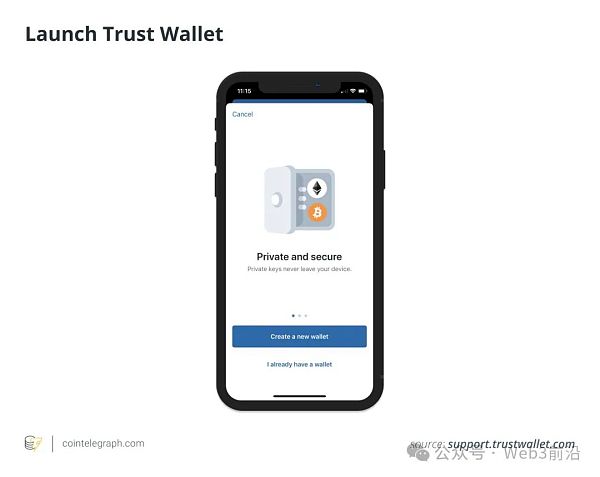
第 2 步:在帐户设置阶段安全地写下助记词并确保其安全。这一点至关重要。如果用户丢失了助记词,他们将无法访问其钱包及其中的任何资金。
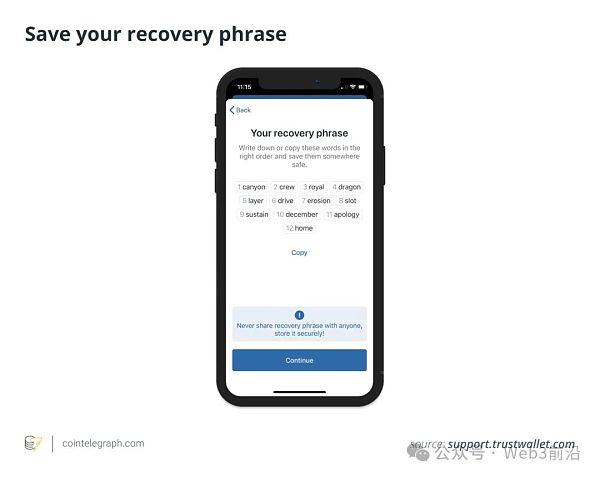
步骤 3:按照屏幕上的说明完成设置。一旦用户完成备份和验证过程,他们就会被引导到主钱包界面,其中可以选择初始的加密货币进行融资。
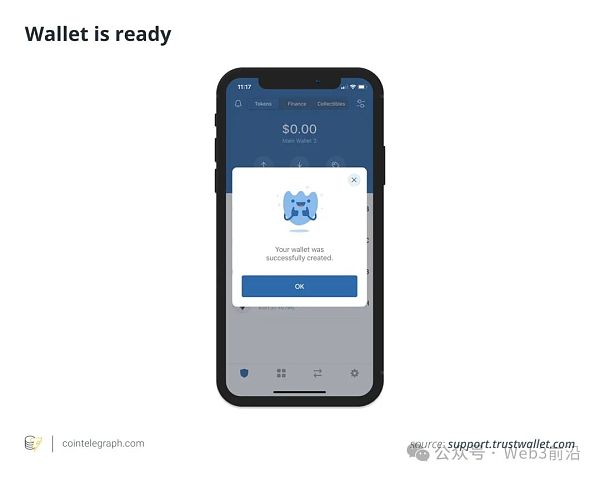
由于整合了多家销售加密货币的提供商,用户可以通过应用程序使用信用卡或借记卡直接为 Trust Wallet 提供资金。如果用户拥有 CEX 账户,他们还可以将加密货币从交易所转移到他们的 Trust 钱包。
使用移动应用程序为加密钱包提供资金的步骤
要使用移动应用程序为加密钱包提供资金,用户必须:
选择他们想要购买的代币并指定数量。
选择提供商的报价。该应用程序通常会突出显示最经济的报价。
用户需要输入他们的付款详细信息(借记卡或信用卡)。请注意,一些银行和卡更加人性化,允许用户执行加密货币交易,而其他银行和卡可能会标记、延迟或阻止此类交易。
在某些情况下,提供商需要用户接受 KYC 检查。
交易完成后,用户将看到加密货币记入他们的钱包。
上述步骤通常构成所谓的“加密货币入口”,用户可以将其法定货币转换为持有的加密货币。Web3精神的关键原则之一是去中心化和自我托管。因此,创建私人自我托管钱包是务实的第一步,为用户在未来提供更广泛的社交和去中心化金融机会。
如何将加密资产转移到 Trust Wallet:分步过程
以下部分将介绍如何将加密资产从 Coinbase 和 MetaMask 钱包转移到 Trust 钱包。
将加密货币从 Coinbase 转移到 Trust Wallet 的步骤
首先,下载并安装 Trust Wallet,然后用户可以按照以下步骤将加密货币从 Coinbase 发送到 Trust Wallet:
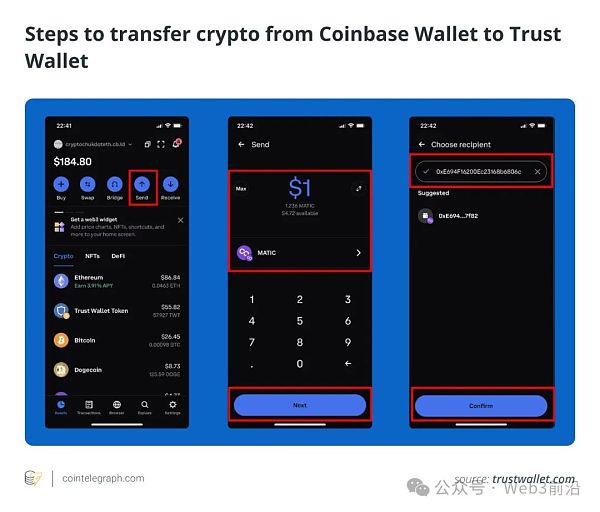
第 1 步:要将加密资产从 Coinbase 转移到 Trust Wallet,请先按 Coinbase 应用程序或网站上的“发送”按钮。
步骤2:选择具体的加密货币和转账金额,然后点击“下一步”。
第 3 步:最后一步是输入 Trust Wallet 的接收地址并按照提供的任何其他提示确认交易。此过程使得数字资产能够在两个钱包之间安全移动。
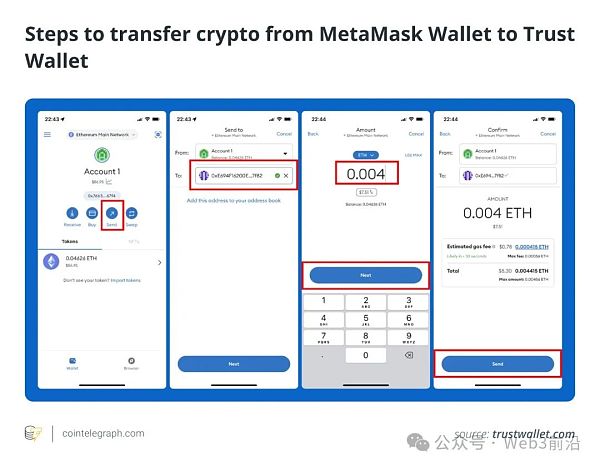
将加密货币从 MetaMask 转移到 Trust Wallet 的步骤
第 1 步:希望将加密货币从 MetaMask 转移到 Trust Wallet 的用户应首先安装 Trust Wallet。
步骤 2:该过程包括点击 MetaMask 钱包中的“发送”按钮,输入 Trust Wallet 地址并选择要转账的金额。
第 3 步:用户应在点击“发送”完成转账之前验证交易详细信息。这有利于两个钱包之间数字资产的安全交换。
自我托管钱包的未来
自我托管钱包与早期相比已经有了显着的发展,当时用户需要技术技能来设置它们,并且必须非常谨慎以避免丢失加密货币。然而,助记词只是更广阔前景的一方面。由于助记词或私钥放错地方而导致钱包丢失的可能性,加上缺乏将钱包所有权转移给家人和朋友的直接方法,仍然是日常用户广泛采用这些钱包的重大障碍。
未来的自我托管钱包理想情况下不会仅仅依靠助记词,而是结合生物识别技术和层层身份验证和批准,以便轻松吸引更多用户,并为他们的数字资产所有权提供安心和安全。
在隐私方面,未来的法规可能会要求个人钱包地址进行 KYC 程序才能进行交易。因此,采用自我托管钱包的主要目的是增强对用户加密资产的控制并获得加密货币生态系统中的机会,而不是保持区块链上的匿名性。
Understand the advantages and disadvantages of the work and gradually set up to control your encrypted assets through self-managed wallets. The cryptocurrency pattern is dynamic and characterized by frequent token issuance. Although some people are familiar with popular cryptocurrencies such as Bitcoin, there are countless tokens emerging in the dollar ecosystem. Those who are interested in holding cryptocurrencies have two main choices: centralized exchange wallets or private self-managed wallets to store them. Both methods have advantages and disadvantages. It will explain the self-managed wallet and share the basic steps of setting up a beginner's wallet to control your encrypted assets. The advantages and disadvantages of holding encrypted currency through a centralized exchange are discussed. The centralized exchange holds encrypted tokens on behalf of its customers. It conforms to the standard arrangement that users create accounts to buy and sell tokens on the exchange and rely on the exchange to carefully handle their accounts and the assets they hold. It is similar to having a bank or stock brokerage account, but some similarities are just that. The exchange has a user's generation. In the event of unfortunate events such as hacking or bankruptcy, users will not be able to recover these funds. Considering that users lack protection and control over deposits and assets, the famous adage is that it is not your key, not your coin, but the failure of direct ownership exchange is not uncommon. Therefore, the prudent choice is to consider this reality and avoid a large number of exposures. However, it provides an easy-to-access entry point for those who have just come into contact with cryptocurrency and can be used to buy tokens for transfer to other wallet users. You can create an account in one of the reputable exchanges in the industry. Most of them need to know your customers. Check that users need to provide identification. After approval, they can set up their accounts to buy and sell cryptocurrencies. Users must ensure that additional security functions such as two-factor authentication are enabled to ensure account security. What is a private self-managed wallet blockchain? It is essentially public, making the tokens owned by any specific wallet address visible to everyone. However, self-managed wallets are private because. The uniqueness of a self-managed wallet is that users have mnemonics or private keys needed to perform any transaction with this address. As long as users guarantee the security of private keys, they are the only people who can control the funds in the wallet, that is, no third party can control or access these funds. How does a self-managed private wallet work? A self-managed wallet usually generates a unique seed phrase for the user's wallet first, and then the user must store it safely. This can be on a piece of paper or any other medium, but users should avoid keeping them as pure scripts on computers or mobile devices, because anyone who has access to the seed phrases will have complete control over the wallet. Self-managed wallets can take many forms, including browser extensions, wallet desktop applications, mobile applications or hardware wallets. These wallets are usually divided into hot wallets or cold wallets according to their intended use and security level. Users usually browse wallets on their desktops or mobile phones. They are considered as hot wallets because they are more vulnerable to potential malicious hacker attacks and security threats because they remain connected to the Internet, while cold wallets are usually offline. Users who are highly concerned about security often use cold wallets in a one-way interactive way, in which coins are transferred to wallets for storage, but strictly speaking, wallets will never be connected to any Internet-based applications to encrypt the evolution of wallets. Packages are going beyond the usual seed phrase mechanism to bring security and simplicity, thus helping to expand the scope of adoption. Some mobile wallets provide the function of allowing trusted contacts to recover, focusing on biometric security to protect assets. In addition, some hardware wallets are paired with mobile applications and use chip cards for asset protection, emphasizing the need to protect chip cards like security keys. In addition, multi-signature wallets need to approve transactions many times, thus adding a layer of security to prevent unauthorized access. And the key steps of starting and setting up potential fraud support multiple blockchains. Anyone can install them on their mobile devices and use them as browser extensions on laptops. First, users can access or download mobile applications. Users can follow the following simple steps to create new accounts. The first step is to install applications on mobile devices. It is very important to write mnemonics safely and ensure their safety in the account setting stage. If users lose mnemonics, they will not be able to access them. The wallet and any fund steps in it are set up according to the instructions on the screen. Once users complete the backup and verification process, they will be guided to the main wallet interface, where they can choose the initial cryptocurrency for financing. Because of the integration of many providers selling cryptocurrency, users can use credit cards or debit cards to provide funds directly through the application. If users have accounts, they can also transfer cryptocurrency from the exchange to their wallets by using mobile applications. Steps to fund a secret wallet To use a mobile application to fund an encrypted wallet, users must choose the tokens they want to buy and specify the quantity to choose the provider's quotation. The application usually highlights the most economical quotation, and users need to enter their payment details. Debit or credit cards, please note that some banks and cards are more user-friendly and allow users to perform encrypted currency transactions, while others may mark delays or prevent such transactions from being provided in some cases. Merchants need users to be checked. After the transaction is completed, users will see the encrypted currency recorded in their wallets. The above steps usually constitute the so-called encrypted currency entrance. One of the key principles of the spirit is decentralization and self-custody. Therefore, it is a pragmatic first step to create a private self-custody wallet, which will provide users with a wider range of social and decentralized financial opportunities in the future. How to transfer encrypted assets to a step-by-step process will be introduced in the following part. The step of transferring encrypted assets from wallet to wallet is to download and install encrypted money from to first, and then users can follow the following steps to transfer encrypted money from to first. To transfer encrypted assets from to first, please press the send button on the application or website to select specific encrypted money and transfer amount, and then click next. The last step is to enter the receiving address and confirm the transaction according to any other prompts provided. This process enables digital assets to move safely between two wallets. The first step is to transfer encrypted money from to. Users who want to transfer encrypted money from should first. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。

















