OKX Web3最新发布:链上防钓鱼安全交易指南
引言
探索链上世界,安全第一,用户需谨记这3条安全规则:不要在任何网页填写助记词/私钥、谨慎点击钱包交易界面 确认按钮、以及推特/Discord/搜索引擎获得的链接可能是钓鱼链接。
进入新周期,链上交互风险随着用户活跃度的增加而日益暴露。钓鱼者通常会采用假冒钱包网站、窃取社交媒体账号、创建恶意浏览器插件、发送钓鱼邮件和信息以及发布虚假应用程序等方式,诱使用户泄露敏感信息,导致资产损失,钓鱼形式和场景呈现多样性、复杂性和隐匿性等特征。
比如,钓鱼者一般通过创建与正规钱包网站外观相似的假冒网站,诱使用户输入其私钥或助记词,这些假冒网站通常会使用社交媒体、电子邮件或广告进行推广,误导用户认为他们正在访问正规的钱包服务,从而盗取用户的资产。此外,还有钓鱼者可能会利用社交媒体平台、论坛或即时通讯应用程序,伪装成钱包客服或社区管理员,向用户发送虚假消息,要求他们提供钱包信息或私钥,这种方式利用了用户对官方的信任,诱使他们泄露私人信息等等。
总之,这些案例突出了钓鱼行为对Web3钱包用户的威胁。为帮助用户提高Web3钱包使用安全意识,并保护资产安全免受损失,OKX Web3深入社区调研并收集了众多Web3钱包用户遭遇过的钓鱼事件,从而提炼出用户最常遇到的4大典型钓鱼场景,并通过不同场景下的细分案例,采用图文案例结合的方式,撰写了Web3用户该如何进行安全交易的最新指南,供大家学习参考。
恶意信息来源
1、热门项目推特回复
通过热门项目推特回复是恶意信息的主要方式之一,钓鱼推特账号可以从Logo、名字、认证标识等都做到和官方号一模一样,甚至连Follower数量也可以是几十K,而唯一能区别两者的就是——推特handle(注意相似字符),请用户务必擦亮眼睛。
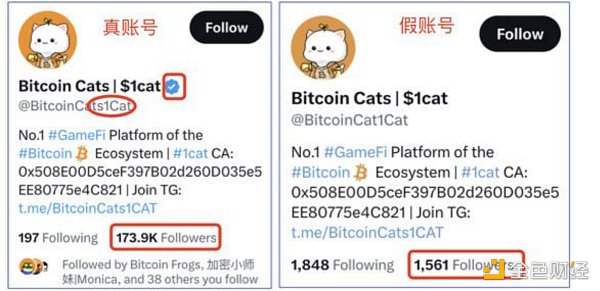
此外,很多时候,假账号会在官推消息下面故意回复,但回复内容中带有钓鱼链接,很容易让用户以为是官方链接,从而上当受骗。目前,有些官方账号目前在推文中,会增加End of Tweet推文,提醒用户防范后续回复中可能包含钓鱼链接的风险。
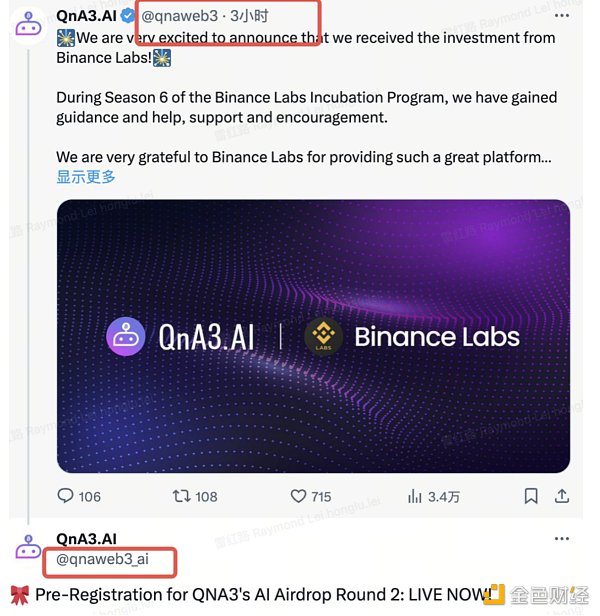
2、盗取官方推特/Discord
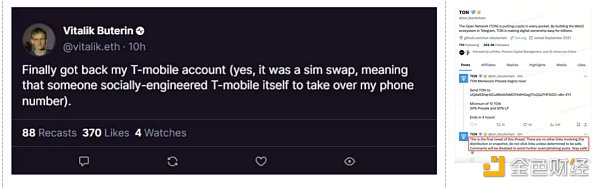
为增加可信性,钓鱼者还会盗取项目方或者KOL的官方推特/Discord,以官方名义发布钓鱼链接,所以很多用户很容易上当。比如,Vitalik的推特账号以及TON项目官方推特就曾被盗取,钓鱼者借机发布了虚假信息或者钓鱼链接。
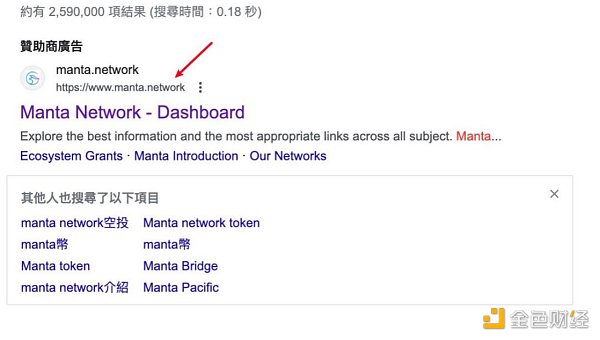
3、谷歌搜索广告
钓鱼者有时会使用谷歌搜索广告发布恶意链接,用户从浏览器显示的名字看为官方域名,但点击后跳转到的链接为钓鱼链接。
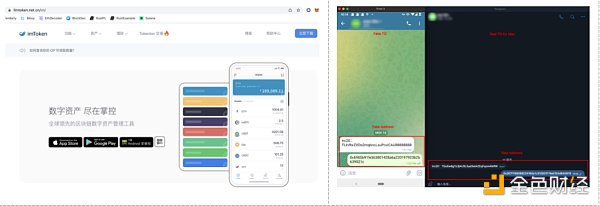
4、虚假应用
钓鱼者还会通过虚假应用从而诱导用户。比如当用户下载安装了钓鱼者发布的假钱包,会导致其私钥泄漏和资产丢失。有钓鱼者曾修改过的Telegram安装包,从而改变了接收和发送代币的链上地址,导致了用户资产的损失。
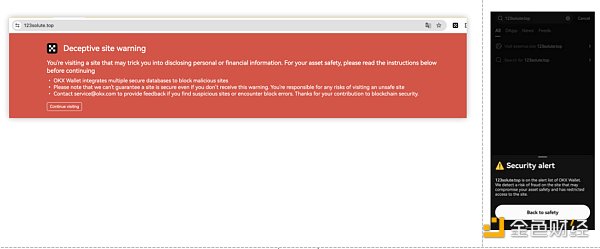
5、应对措施:OKX Web3钱包支持钓鱼链接检测及风险提醒
当前,OKX Web3钱包通过支持钓鱼链接检测及风险提醒,为帮助用户更好地应对上述问题。比如,用户通过OKX Web3插件钱包使用浏览器访问网站时,如果该域名为已知恶意域名,则会第一时间收到告警提醒。此外,如果用户使用OKX Web3 APP在Discover界面访问第三方DAPP时,OKX Web3钱包将会自动针对域名进行风险检测,如果其为恶意域名,则会进行拦截提醒,禁止用户访问。
钱包私钥安全
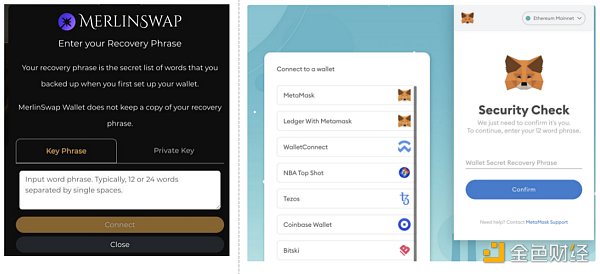
1、进行项目交互或者资格验证
钓鱼者会在用户在进行项目交互或者资格验证时候,伪装成插件钱包弹窗的页面或者其他任何网页,要求用户填写助记词/私钥,这类一般都是都是恶意网站,用户应该提高警惕意识。
2、冒充项目方客服或者管理员
钓鱼者经常会冒充项目方客服或者Discord管理员,并提供网址让用户输入助记词或者私钥,这种情况说明对方是钓鱼者。

3、其他助记词/私钥泄漏可能路径
用户助记词和私钥泄漏可能路径有很多,常见的包括电脑被植入木马病毒软件、电脑使用了撸毛用的指纹浏览器、电脑使用了远程控制或代理工具、助记词/私钥截图保存相册,但被恶意APP上传、备份到云端,但云端平台被入侵、输入助记词/私钥过程被监控、身边人物理获取到助记词私钥文件/纸 、以及开发人员推送包括私钥代码到Github等等。
总之,用户需要安全地存储和使用助记词/私钥,从而更好的保证钱包资产安全。比如,当前作为去中心化的自托管钱包,OKX Web3钱包上线iCloud/Google Drive云端、手动、硬件等多种助记词/私钥备份方式,已成长为市面上支持私钥备份方式较为全面的钱包,为用户提供较为安全的私钥存储方式。在用户私钥被盗问题上,OKX Web3钱包已支持Ledger、 Keystone、Onekey 等较为全面的主流硬件钱包功能,硬件钱包的私钥存储在硬件钱包设备里,由用户自己掌握,从而保障资产安全。也就是OKX Web3钱包让用户通过硬件钱包安全管理资产的同时,又可以自由参与链上代币交易、NFT市场和各类dApp项目交互等。此外,OKX Web3 钱包现已上线 MPC无私钥钱包、以及AA智能合约钱包,帮助用户进一步简化私钥问题。
4大经典钓鱼场景
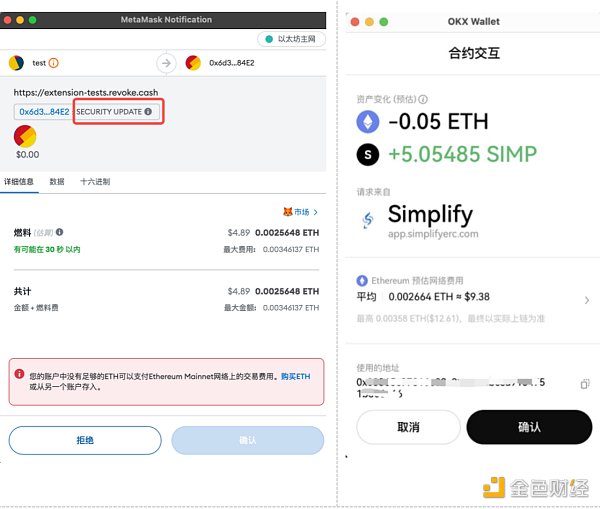
场景1、窃取主链代币
钓鱼者往往会给恶意合约函数起名为Claim,SeurityUpdate等具有诱导性名字,而实际函数逻辑为空,从而只转移用户主链代币。当前OKX Web3钱包已上线交易预执行功能,显示该交易上链后资产及授权变化,从而进一步提醒用户注意安全。另外,如果其交互合约或授权地址为已知恶意地址,则会进行红色安全提醒。
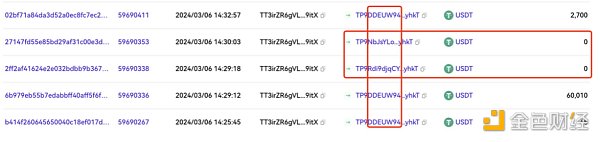
场景2、相似地址转账
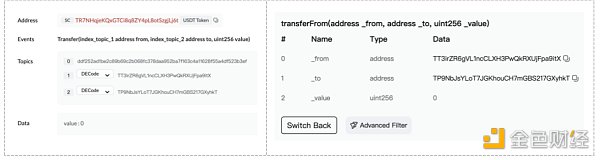
当监测到有大额转账时,钓鱼者会通过地址碰撞生成和接收地址首位若干位相同的地址,利用transferFrom进行0金额转账,或利用假USDT进行一定金额转账,污染用户交易历史,期望用户后续转账从交易历史拷贝错误地址,完成诈骗。
https://www.oklink.com/cn/trx/address/TT3irZR6gVL1ncCLXH3PwQkRXUjFpa9itX/token-transfer
https://tronscan.org/#/transaction/27147fd55e85bd29af31c00e3d878bc727194a377bec98313a79c8ef42462e5f
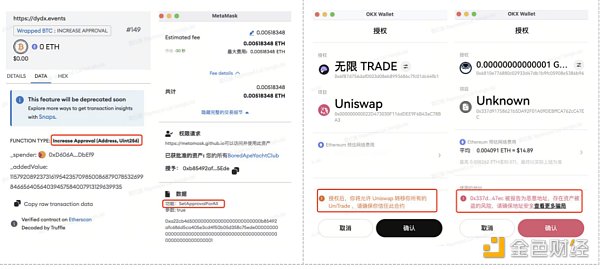
场景3、链上授权
钓鱼者通常会诱导用户签署 approve / increaseAllowance / decreaseAllowance / setApprovalForAll 交易,以及升级使用Create2生成预先计算好的新地址,绕过安全检测,从而骗取用户授权相关。OKX Web3钱包会针对授权交易进行安全提醒,请用户注意该交易为授权相关交易,注意风险。另外,如果交易授权地址为已知恶意地址时,会进行红色信息提醒,避免用户上当受骗。
场景4、链下签名
除了链上授权外,钓鱼者还会通过诱导用户进行链下签名的方式进行钓鱼。比如,ERC20代币授权允许用户授权给另外一个地址或合约一定额度,被授权地址可以通过transferFrom转移用户资产,钓鱼者就是利用这种特点进行诈骗。当前OKX Web3钱包正在针对此类场景开发风险提示功能,当用户签署离线签名时,通过解析签名授权地址,如果命中已知恶意地址,会对用户进行风险提示。
其他钓鱼场景
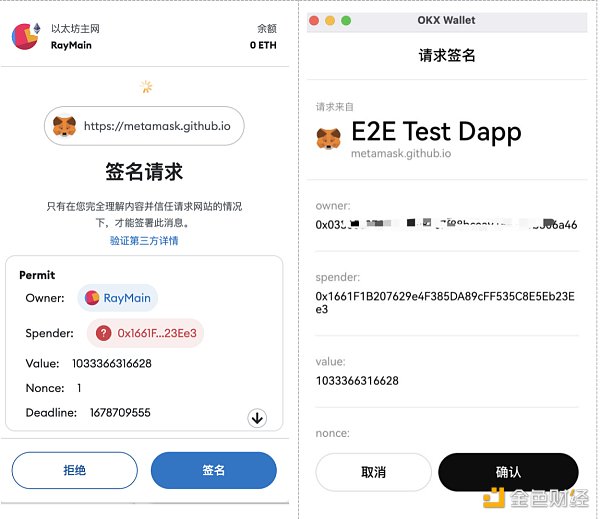
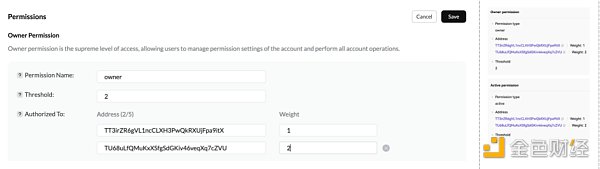
场景5、TRON账号权限
这类场景比较抽象,一般是钓鱼者通过获取用户TRON账号权限来控制其资产。TRON账号权限设置和EOS类似,分为Owner和Active权限,并可以设置类似多签形式进行权限控制,如下权限设置Owner门限为2,两个地址权重分别为1和2,第一个地址为用户地址,权重为1无法单独操作账号。
https://tronscan.org/#/wallet/permissions
https://www.oklink.com/trx/tx/1fe56345873425cf93e6d9a1f0bf2b91846d30ca7a93080a2ad69de77de5e45f
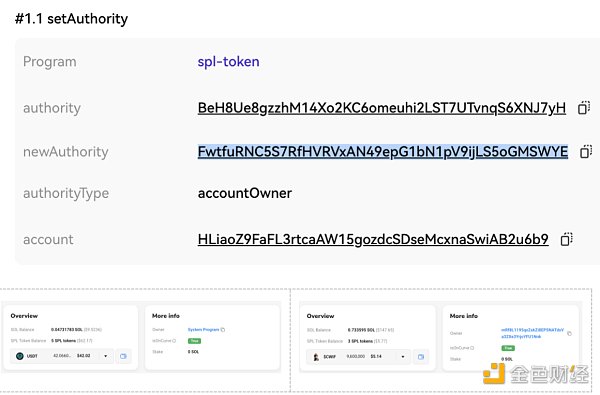
场景6、Solana代币及账号权限
钓鱼者通过SetAuthroity修改代币ATA账户Ownership,相当于代币转给了新的Owner地址。用户被该方法钓鱼后,资产转移给钓鱼方等等。此外,如果用户签署了Assign交易,其正常账号的Owner将从System Program被修改为恶意合约。
场景7、EigenLayer调用 queueWithdrawal
由于协议本身的设计机制等问题,也很容易被钓鱼者利用。基于以太坊的中间件协议EigenLayer的queueWithdrawal调用,允许指定其他地址作为withdrawer,用户被钓鱼签署了该交易。七天后,指定地址通过completeQueuedWithdrawal获得用户的质押资产。
探索链上世界,安全第一
安全使用Web3钱包是保护资产的关键措施,用户应切实采取预防措施以防范潜在的风险和威胁。可以选择行业知名的、经过安全审计的OKX Web3钱包、更安全便捷地探索链上世界。
作为行业最先进以及功能最全面的钱包,OKX Web3钱包完全去中心化、且自托管,支持用户一站式玩转链上应用,现已支持 85+ 公链,App、插件、网页三端统一,涵盖钱包、DEX、DeFi、NFT 市场、DApp 探索 5 大板块、并支持 Ordinals 市场、MPC 和 AA 智能合约钱包、兑换 Gas、连接硬件钱包等。此外,用户还可以通过安全地保护私钥和助记词、定期更新钱包应用和操作系统、谨慎处理链接和信息以及启用多重身份验证功能,从而增加钱包的安全性。
总之,在链上世界,资产安全大于一切。
用户需要谨记这3条Web3安全规则:不要在任何网页填写助记词/私钥、谨慎点击钱包交易界面 确认按钮、以及推特/Discord/搜索引擎获得的链接可能是钓鱼链接。
Introduction The first user in the exploration chain should keep in mind this safety rule. Don't fill in the mnemonic private key on any webpage. Carefully click the confirm button on the wallet transaction interface and the link obtained by the Twitter search engine may be a phishing link entering a new cycle chain. With the increase of user activity, the risk of interaction is increasingly exposed. Fishermen usually use fake wallet websites to steal social media accounts, create malicious browser plug-ins to send phishing emails and information, and publish fake applications. Causes users to disclose sensitive information, resulting in asset losses. The forms and scenes of phishing are characterized by diversity, complexity and concealment. For example, anglers generally induce users to enter their private keys or mnemonics by creating fake websites with similar appearance to regular wallet websites. These fake websites usually use social media e-mails or advertisements to promote and mislead users into thinking that they are accessing regular wallet services, thus stealing users' assets. In addition, anglers may use social media platforms and forums. Or instant messaging applications disguised as wallet customer service or community administrators sent false messages to users asking them to provide wallet information or private keys, which used users' trust in the government to induce them to disclose private information, etc. In short, these cases highlighted the threat of phishing to wallet users. In order to help users improve their awareness of wallet use safety and protect assets from losses, they conducted in-depth community research and collected many phishing incidents encountered by wallet users, thus extracting the most common ones for users. Typical fishing scenes encountered, and the latest guide on how users can conduct safe transactions by combining graphic cases in different scenarios is written for your reference. The source of malicious information: Twitter reply through popular projects is one of the main ways of malicious information. The phishing Twitter account can be exactly the same as the official number in terms of name authentication and logo, and even the number can be dozens. The only thing that can distinguish the two is that Twitter pays attention to similarity. Please keep your eyes open. In addition, in many cases, fake accounts will deliberately reply under official tweets, but the reply content contains phishing links, which can easily make users think it is an official link and thus be deceived. At present, some official accounts will add tweets in tweets to remind users to guard against the risk of phishing links in subsequent replies. In order to increase credibility, phishers will also steal the project party or official tweets to post phishing links in the official name, so many users are very worried. Easy to be fooled, such as Twitter account and official Twitter of the project, have been stolen, and anglers have taken the opportunity to post false information or phishing links. Google search advertisements are sometimes used by anglers to post malicious links. Users look at the name displayed in the browser as official domain names, but the links they jump to after clicking are phishing links. False applications will also induce users to use false applications. For example, when users download and install fake wallets published by anglers, their private keys will be leaked and assets will be caused. The loss of the installation package modified by the fisherman has changed the chain address for receiving and sending tokens, resulting in the loss of user assets. Countermeasures: The wallet supports phishing link detection and risk warning. The current wallet supports phishing link detection and risk warning to help users better cope with the above problems. For example, if the domain name is a known malicious domain name when users use the browser through the plug-in wallet, they will receive an alarm warning at the first time. In addition, if users use the interface to access the first. The wallet will automatically carry out risk detection for the domain name. If it is a malicious domain name, it will intercept and remind users not to access the private key of the wallet for safe project interaction or qualification verification. The fisherman will pretend to be a plug-in wallet pop-up page or any other web page when the user is engaged in project interaction or qualification verification, and ask the user to fill in the mnemonic private key. These are generally malicious websites. Users should be vigilant and pretend to be customer service or administrators of the project. Fishermen often. Will pretend to be the customer service or administrator of the project party and provide the website for the user to enter the mnemonic or private key, which means that the other party is a fisherman. Other mnemonic private keys may leak. There are many common paths for the user's mnemonic and private key to leak, including the computer being implanted with Trojan virus software, the computer using a fingerprint browser, the computer using a remote control or proxy tool, the private key screenshot of the mnemonic saved the photo album, but it was maliciously uploaded and backed up to the cloud, but the cloud platform was invaded to enter the mnemonic. The private key process is monitored, people around us physically get the mnemonic private key file paper, and developers push the private key code to it, etc. In short, users need to safely store and use the mnemonic private key to better ensure the security of wallet assets. For example, at present, as a decentralized self-managed wallet, the wallet is online and cloud-based manual hardware and other mnemonic private key backup methods have grown into wallets that support private key backup methods in the market and provide users with safer private key storage methods. On the issue of stolen private key, the wallet has supported the mainstream hardware wallet functions. The private key of the hardware wallet is stored in the hardware wallet device and mastered by the user, thus ensuring the security of the assets. That is, the wallet allows the user to safely manage the assets through the hardware wallet while freely participating in the online token trading market and various item interactions. In addition, the wallet is now online, and the wallet without private key and the smart contract wallet help the user to further simplify the private key problem. Token anglers often give the malicious contract function an induced name, but the actual function logic is empty, thus only transferring the user's main chain token. The pre-execution function shows the changes of assets and authorization after the transaction is wound up, thus further reminding the user to pay attention to safety. In addition, if the interactive contract or authorization address is a known malicious address, a red security reminder scenario will be carried out. When a large amount of transfer is detected, the angler will generate and receive it through address collision. The same address in the first few digits of the receiving address pollutes the user's transaction history by transferring money or transferring a certain amount of money by fraud. It is expected that the user will copy the wrong address from the transaction history to complete the fraud scene chain. The authorized angler will usually induce the user to sign the transaction and upgrade the use to generate a pre-calculated new address to bypass the security detection, thus defrauding the user to authorize the relevant wallet. Please pay attention to the risks of the authorized transaction. In addition, if the authorized address of the transaction is a known malicious address, a red message will be reminded to avoid the user being deceived. 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。