使用Azure AD SAML SSO配置ISE 3.0發起人門戶
本文檔介紹如何使用思科身份服務引擎(ISE)3.0配置Azure Active Directory(AD)SAML伺服器,為發起人使用者提供單一登入(SSO)功能。
This document provides an overview of how the Cisco Identity Service Engine (ISE) 3.0 can be used to configure the Azure Active Directory (AD) SAML server to provide a single login (SSO) function for senders.
思科建議您瞭解以下主題:
Cisco suggests that you should be aware of the following themes:
- Cisco ISE 3.0
- 有關SAML SSO部署的基本知識
- Azure AD
- Cisco ISE 3.0
- Azure AD
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
The information in this paper is based on the devices in a given laboratory environment. All devices used in the text are activated from the cleared (predicted) configuration. If you are working on your network, make sure you understand the implications of any instructions.
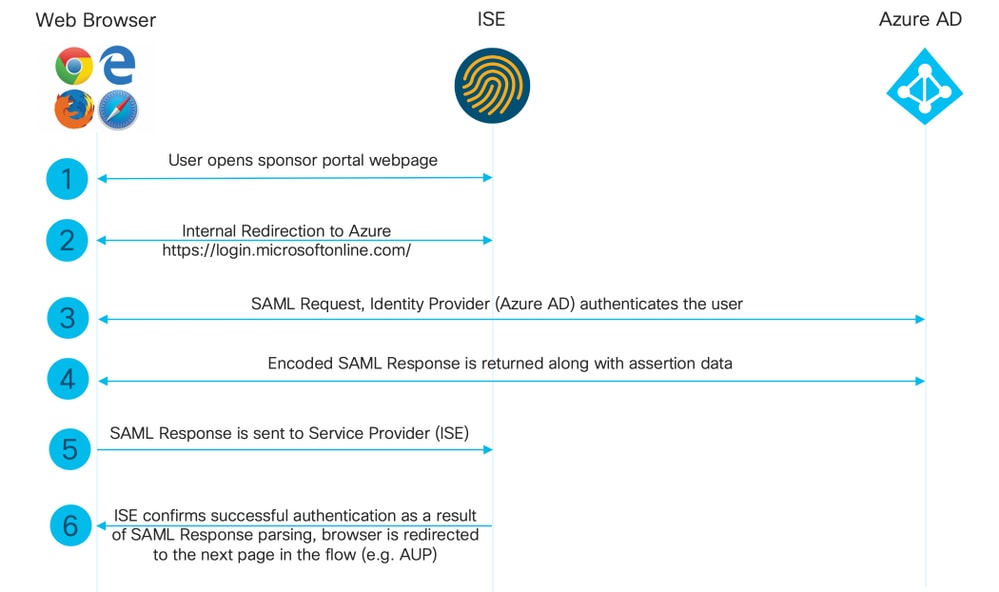
1.將Azure AD配置為外部SAML標識源
在ISE上,導航到Administration > Identity Management > External Identity Sources > SAML Id Providers,然後點選Add按鈕。
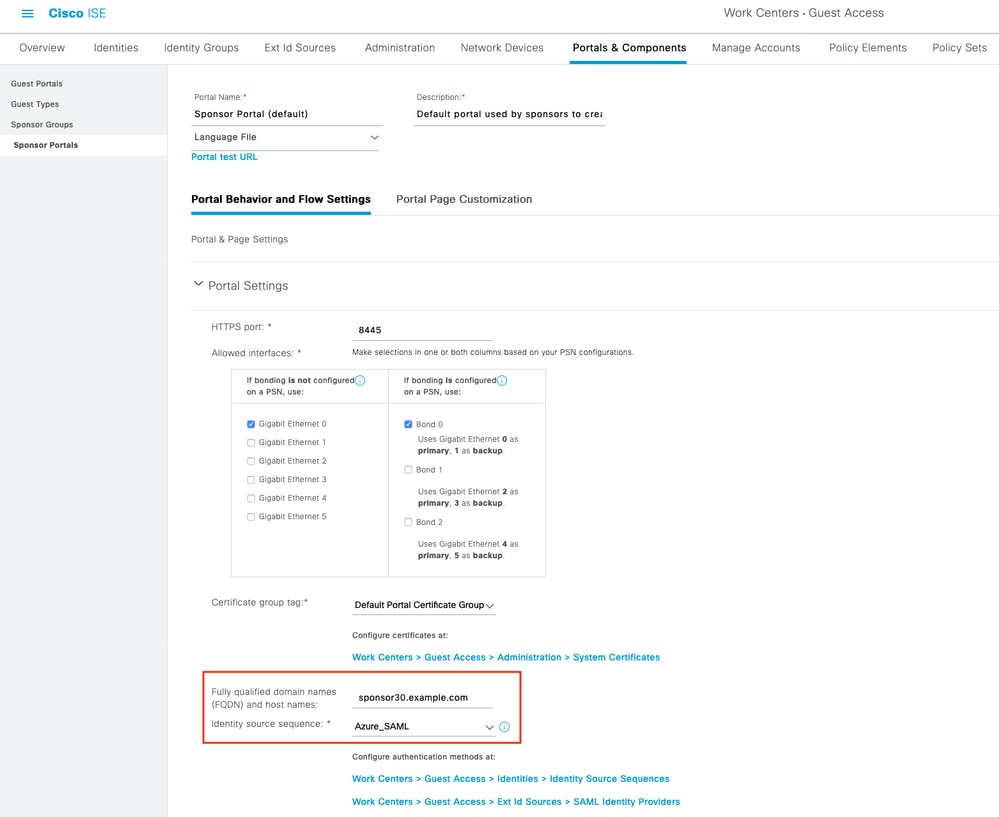
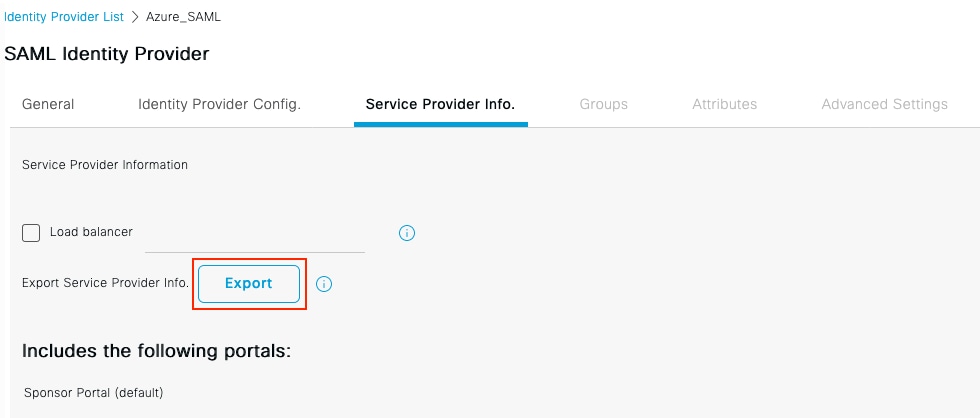
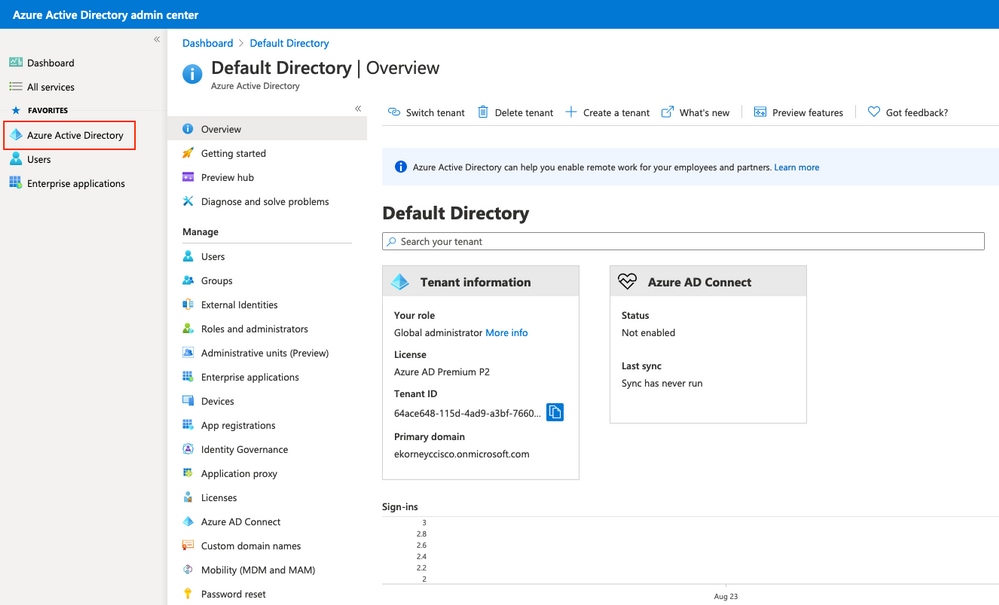
On ISE, the ship is directed to Administration & gt; Identity Management & gt; Extranality Resources & gt; SAML Id Providers and then click on 輸入Id Provider Name,然後按一下Submit儲存它。Id Provider Name僅對ISE有效,如下圖所示。 Enter Id Provider Name, and press Submit to store it. Id Provider Name only works for ISE, as shown below. 導航至工作中心>訪客接入>門戶和元件>發起人門戶,然後選擇發起人門戶。在此示例中使用發起人門戶(預設)。 Guides to work center > visitor access > door and component & gt; sender , and then choose to send. In this example, uses sender . 展開Portal Settings面板,然後在Identity source序列中選擇您的新SAML IdP。為發起人門戶配置完全限定域名(FQDN)。在本例中,它是sponsor30.example.com。按一下「Save」,如下圖所示。 Expand the Portal Settings panel and select your new SAML IdP in the series Identitysource. The full domain name (FQDN) is configured for the sender . In this case, it is sponsor30.example.com. Click on Save, as shown in the figure below. 導航到管理>身份管理>外部身份源> SAML Id提供程式> [您的SAML提供程式]。 Lead to administration> identity management> external identity source> SAML Id supply program> [Your SAML supply program]. 切換到Service Provider Info頁籤。然後按一下Export按鈕,如下圖所示。 Switch to ServiceProviderInfo. Then press the button of Export, as shown in the figure below. 下載並儲存該zip檔案。您可以在其中找到2個檔案。您需要稱為發起人門戶的XML檔案。 Downloads and saves the zip file. You can find two files in it. You need an XML file that you call the sender. 請記下來自SingleLogoutService Bindings的ResponseLocation、entityID值以及AssertionConsumerServiceBinding的Location值。 Please note the value of ResponseLocation, entityID from SingLogoutServicebinding, and the value of 根據XML檔案: According to XML file: SingleLogoutService ResponseLocation="https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action" entityID="http://CiscoISE/100d02da-9457-41e8-87d7-0965b0714db2" AssertionConsumerService Location="https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action" AssertionConsumerService Location="https://10.48.23.86:8445/sponsorportal/SSOLoginResponse.action" AssertionConsumerService Location="https://10.48.23.63:8445/sponsorportal/SSOLoginResponse.action" AssertionConsumerService Location="https://10.48.26.60:8445/sponsorportal/SSOLoginResponse.action" AssertionConsumerService Location="https://ise30-1ek.example.com:8445/sponsorportal/SSOLoginResponse.action" AssertionConsumerService Location="https://ise30-2ek.example.com:8445/sponsorportal/SSOLoginResponse.action" AssertionConsumerService Location="https://ise30-3ek.example.com:8445/sponsorportal/SSOLoginResponse.action" 登入到Azure Active Directory管理中心儀表板並選擇你的AD,如下圖所示。 Log in to the Azure Active Management Center dashboard and select your AD, as shown in the figure below. 選擇Users,按一下New User,配置User name、Name和Initial Password。按一下「Create」,如下圖所示。 Select 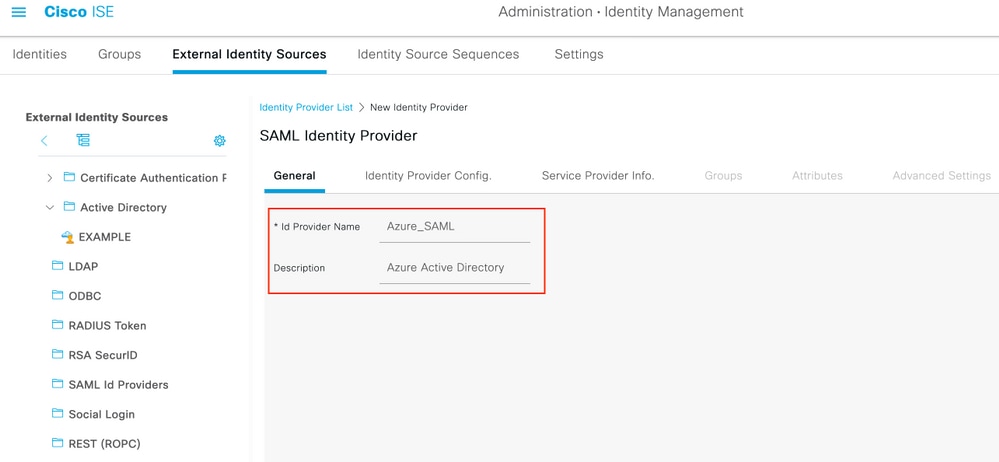
2.配置發起人門戶以使用Azure AD
3.匯出服務提供商資訊
<?xml version="1.0" encoding="UTF-8"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429">
<md:SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>
MIIFZjCCA06gAwIBAgIQX1oAvwAAAAChgVd9cEEWOzANBgkqhkiG9w0BAQwFADAlMSMwIQYDVQQD
ExpTQU1MX0lTRTMwLTFlay5leGFtcGxlLmNvbTAeFw0yMDA5MTAxMDMyMzFaFw0yNTA5MDkxMDMy
MzFaMCUxIzAhBgNVBAMTGlNBTUxfSVNFMzAtMWVrLmV4YW1wbGUuY29tMIICIjANBgkqhkiG9w0B
AQEFAAOCAg8AMIICCgKCAgEAt+MixKfuZvg/oAWGEs6zrUYL3H2JwvZw9yJs6sJ8/BpP6Sw027wh
FXnESXpqmmoSVrVEcQIrDdk3l8UYNn/+98PPkIi/4ftyFjZK9YdeverD6nrA2MeoLCzGlkWq/y4i
vvVcYuW344pySm65awVvro3q84x9esHqyLahExs9guiLJryD497XmNP4Z8eTHCctu777PuI1wLO4
QOYUs2sozXvR98D9Jok/+PjH3bjmVKapqAcNEFvk8Ez9x1sMBUgFwP4YdZzQB9IRVkQdIJGvqMyf
a6gn+KaddJnmIbXKFbrTaFii2IvRs3qHJ0mMVfYRnYeMql9/PhzvSFtjRe32x/aQh23j9dCsVXmQ
ZmXpZyxxJ8p4RqyM0YgkfxnQXXtV9K0sRZPFn6O+iszUw2hARRG/tE0hTuVXpbonG2dT109JeeEe
S1E5uxenJvYkU7mMamvBjYQN6qVyyogf8FOlHTSfd6TDsK3QhmzOjg50PrBvvg5qE6OrxxNvqSVZ
1dhx/iHZAZ1yYSVdwizsZMCw0PjSwrRPx/h8l03djeW0aL5R1AF1qTFHVHSNvigzh6FyjdkUJH66
JAygPe0PKJFRgYzh5vWoJ41qvdQjlGk3c/zYi57MR1Bs0mkSvkOGbmjSsb+EehnYyLLB8FG3De2V
ZaXaHZ37gmoCNNmZHrn+GB0CAwEAAaOBkTCBjjAgBgNVHREEGTAXghVJU0UzMC0xZWsuZXhhbXBs
ZS5jb20wDAYDVR0TBAUwAwEB/zALBgNVHQ8EBAMCAuwwHQYDVR0OBBYEFPT/6jpfyugxRolbjzWJ
858WfTP1MB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjARBglghkgBhvhCAQEEBAMCBkAw
DQYJKoZIhvcNAQEMBQADggIBABGyWZbLajM2LyLASg//4N6mL+xu/9IMdVvNWBQodF+j0WusW15a
VPSQU2t3Ckd/I1anvpK+cp77NMjo9V9oWI3/ZnjZHGoFAIcHnlGCoEjmC1TvLau7ZzhCCII37DFA
yMKDrXLi3pR+ONlXlTIvjpHTTzrKm1NHhkxkx/Js5Iuz+MyRKP8FNmWT0q4XGejyKzJWrqEu+bc1
idCl/gBNuCHgqmFeM82IGQ7jVOm1kBjLb4pTDbYk4fMIbJVh4V2Pgi++6MIfXAYEwL+LHjSGHCQT
PSM3+kpv1wHHpGWzQSmcJ4tXVXV95W0NC+LxQZLBPNMUZorhuYCILXZxvXH1HGJJ0YKx9lk9Ubd2
s5JaD+GN8jqm5XXAau7S4BawfvCo3boOiXnSvgcIuH9YFiR2lp2n/2X0VVbdPHYZtqGieqBWebHr
4I1z18FXblYyMzpIkhtOOvkP5mAlR92VXBkvx2WPjtzQrvOtSXgvTCOKErYCBM/jnuwsztV7FVTV
JNdFwOsnXC70YngZeujZyjPoUbfRKZI34VKZp4iO5bZsGlbWE9Skdquv0PaQ8ecXTv8OCVBYUegl
vt0pdel8h/9jImdLG8dF0rbADGHiieTcntSDdw3E7JFmS/oHw7FsA5GI8IxXfcOWUx/L0Dx3jTNd
ZlAXp4juySODIx9yDyM4yV0f
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sponsor30.example.com:8445/sponsorportal/SSOLogoutRequest.action?portal=bd48c1a1-9477-4746-8e40-e43d20c9f429" ResponseLocation="https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:WindowsDomainQualifiedName</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:kerberos</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action" index="0"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://10.48.23.86:8445/sponsorportal/SSOLoginResponse.action" index="1"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://10.48.26.63:8445/sponsorportal/SSOLoginResponse.action" index="2"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://10.48.26.60:8445/sponsorportal/SSOLoginResponse.action" index="3"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ise30-1ek.example.com:8445/sponsorportal/SSOLoginResponse.action" index="4"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ise30-2ek.example.com:8445/sponsorportal/SSOLoginResponse.action" index="5"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ise30-3ek.example.com:8445/sponsorportal/SSOLoginResponse.action" index="6"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>1.建立Azure AD使用者
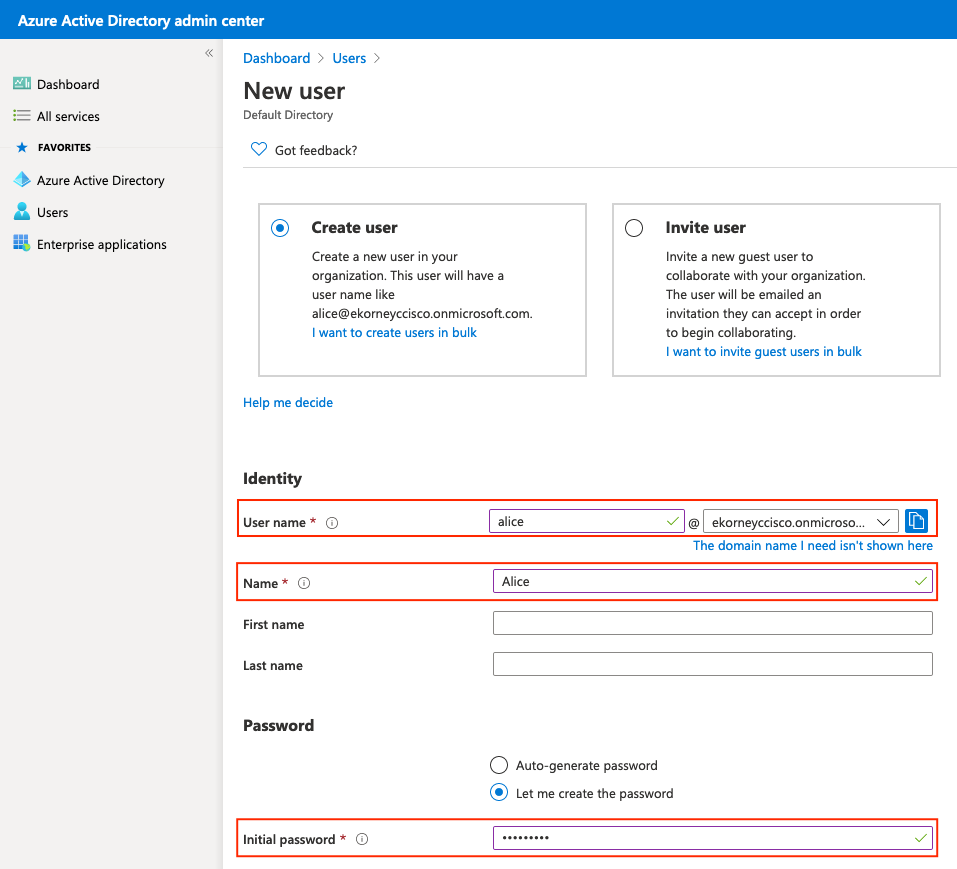
2.建立Azure AD組
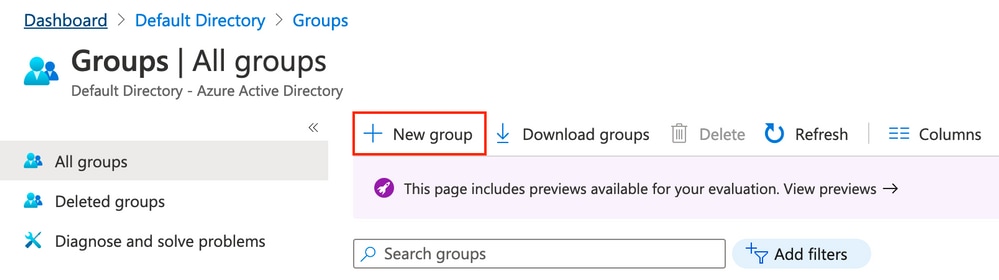
選擇組。按一下「New Group」,如下圖所示。
Select the
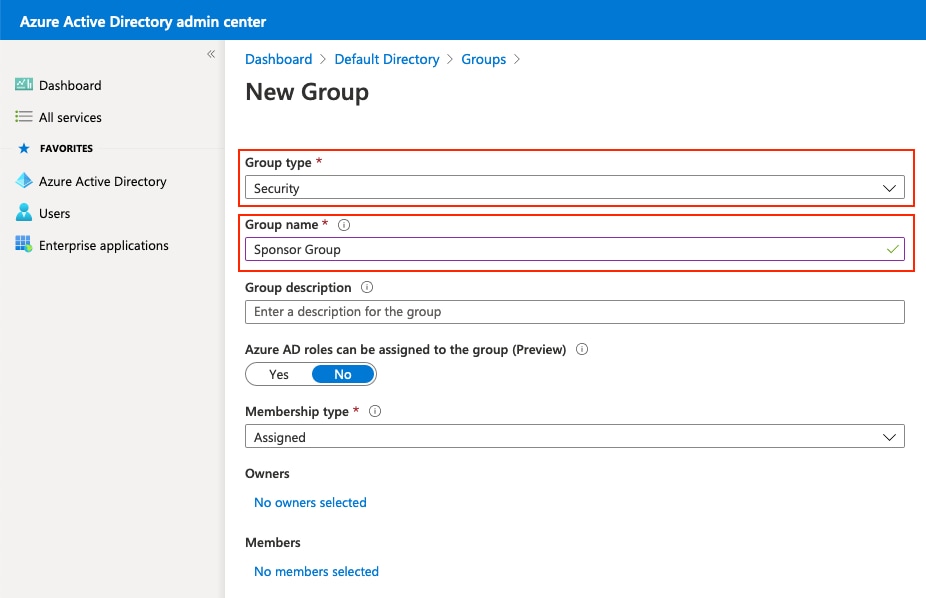
將組型別保留為安全。設定群組名稱,如下圖所示。
Keep the grouping safe for . sets the group name for , as shown in the figure below.
3.將Azure AD使用者分配給組
按一下No members selected。選擇使用者並按一下Select。按一下Create以建立已為其分配「使用者」的組。
Click on
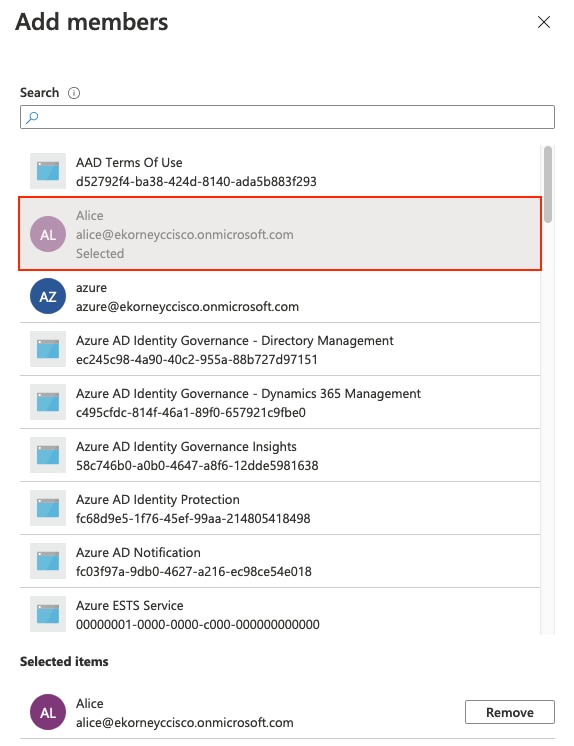
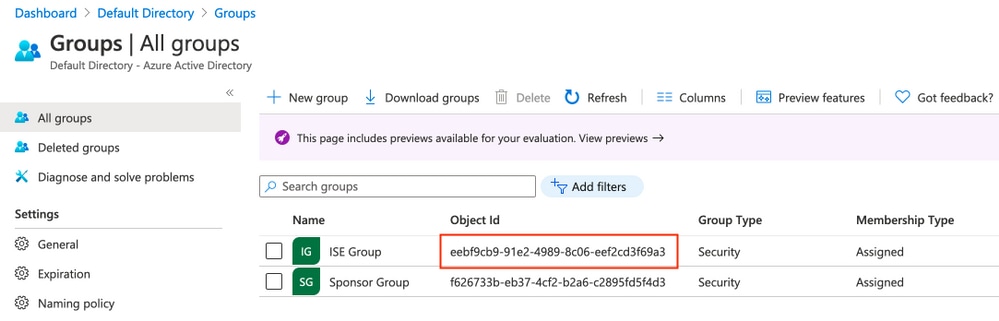
記下Group Object id,在此螢幕中,發起人組為f626733b-eb37-4cf2-b2a6-c2895fd5f4d3。
Take note of
4.建立Azure AD Enterprise應用程式
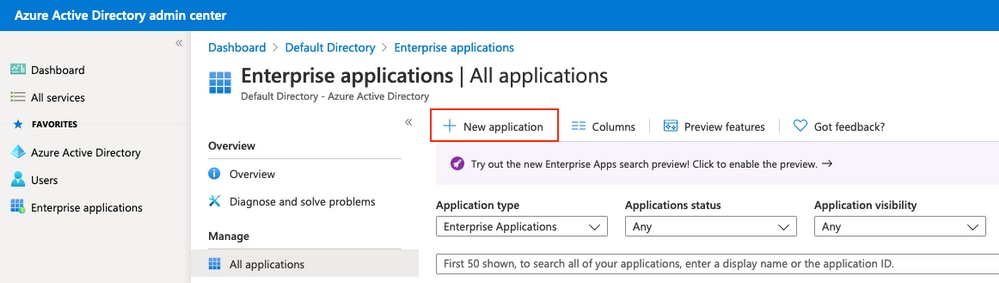
在AD下,選擇Enterprise Applications,然後按一下New application,如下圖所示。
Under AD, select Enterprise Applications, and then press New application, as shown in the figure below.
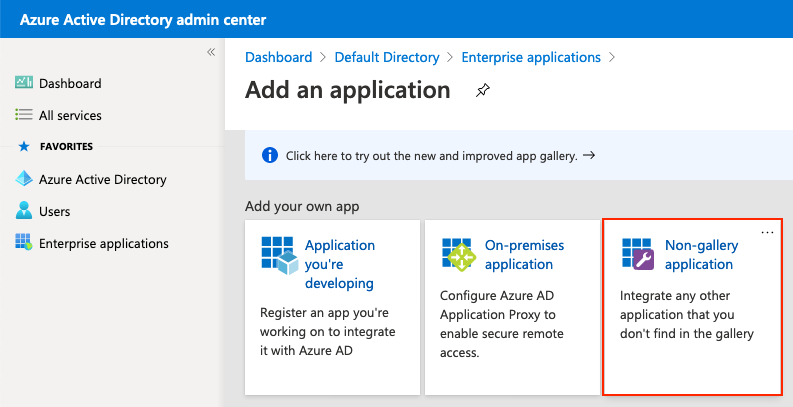
選擇Non-gallery應用程式,如下圖所示。
Select the non-gallery application, as shown in the figure below.
輸入應用程式的名稱,然後按一下Add。
Enter the name of the application and press Add.
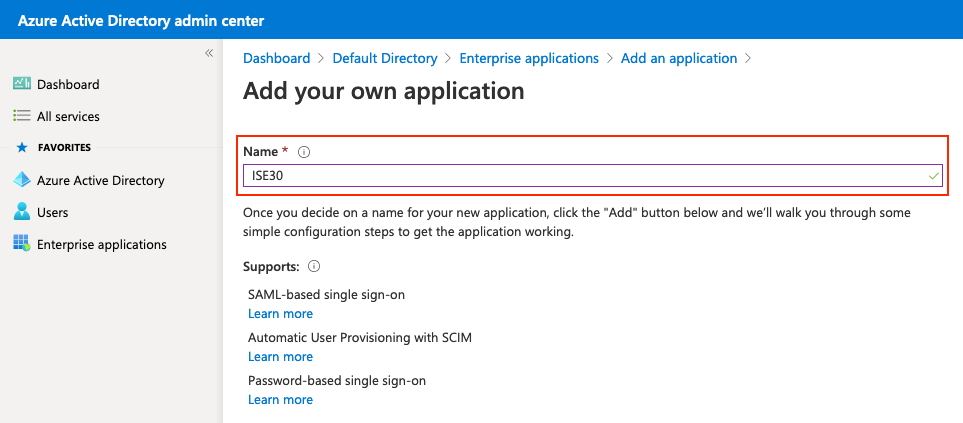
5.將組新增到應用程式
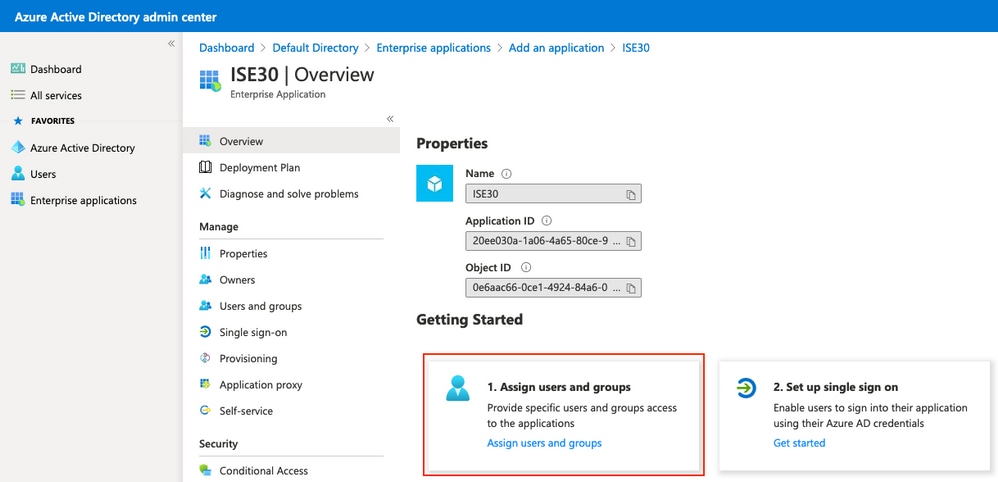
選擇分配使用者和組。
Select the user and group of
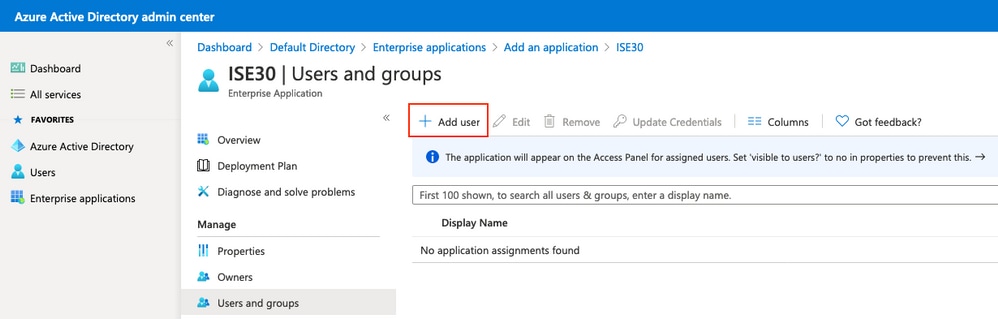
按一下Add user。
Press
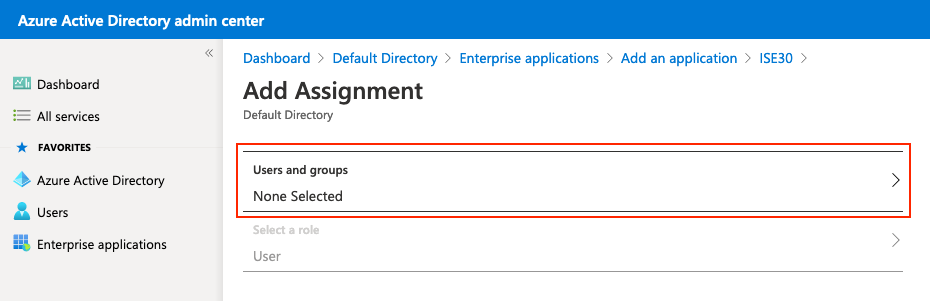
按一下Users and groups。
Press
選擇先前配置的組,然後按一下選擇。
Select the previously configured group and press .
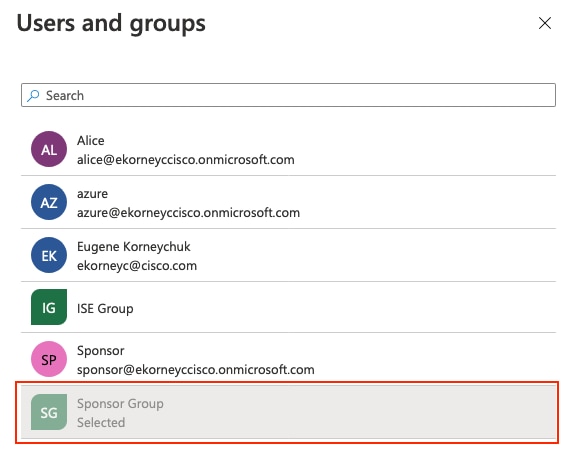
選擇組後,按一下Assign,如下圖所示。
After selecting the group, press Assign, as shown in the figure below.
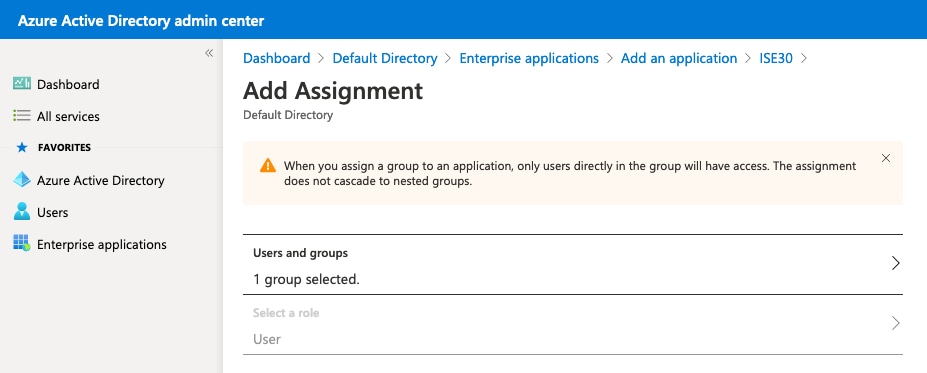
因此,應用程序的「用戶和組」選單應使用所選組進行填充。
Therefore, the application program

6.配置Azure AD Enterprise應用程式
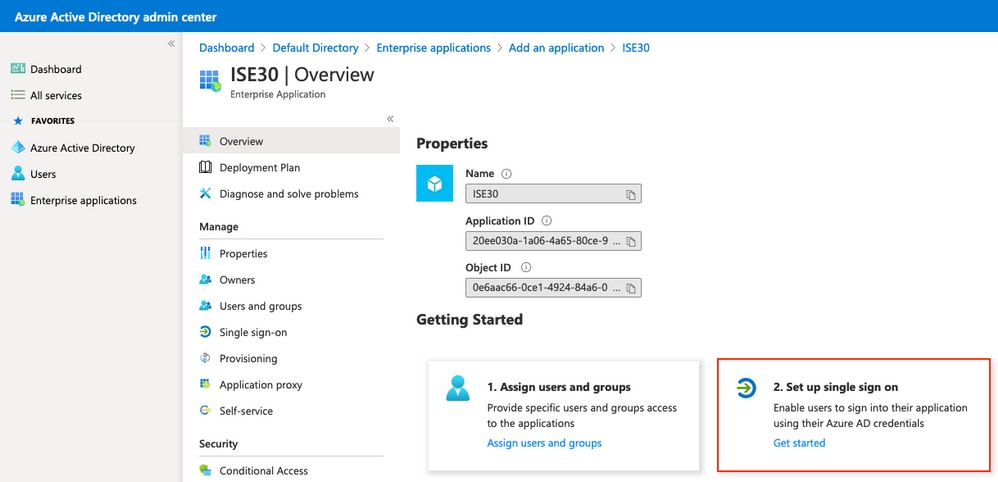
導覽回您的應用程式,然後按一下Set up single sign-on,如下圖所示。
Navigates your application and then press Set up single sign-on, as shown in the figure below.
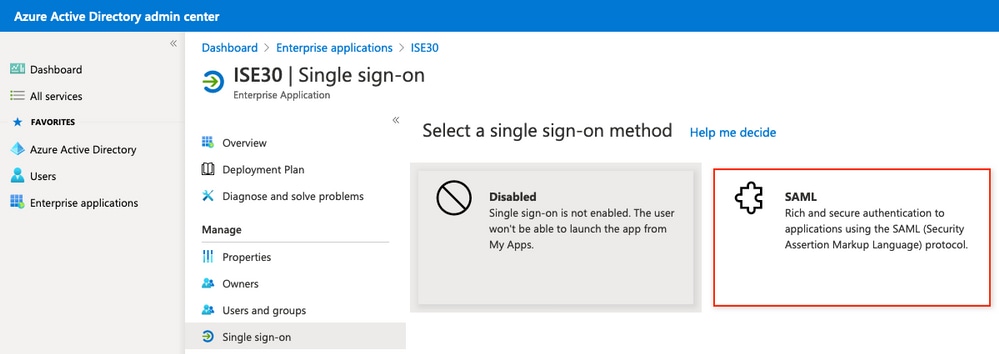
在下一個螢幕上選擇SAML。
On the next screen, select SAML.
按一下Basic SAML Configuration旁邊的Edit。
Press the strongEdit next to Basic SAML Consultation.
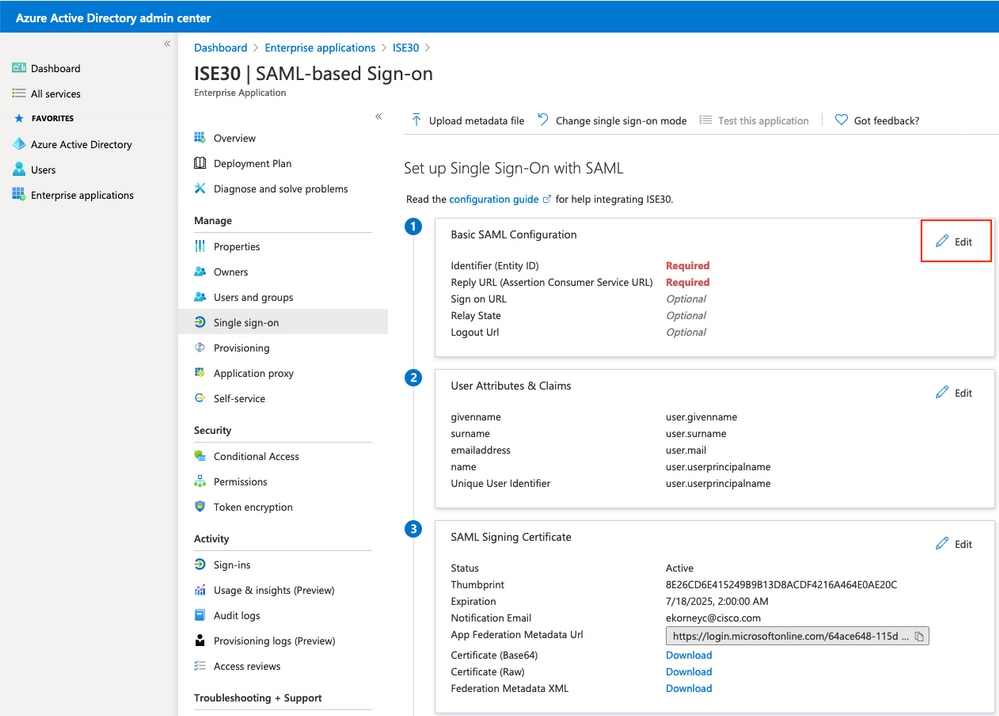
在步驟匯出服務提供商資訊中,使用XML檔案中的entityID值填充識別符號(實體ID)。使用AssertionConsumerService中的Locations值填充Reply URL(Assertion Consumer Service URL)。使用ResponseLocation 填充註銷Url值(來自SingleLogoutService)。按一下Save。
In a step
7.配置Active Directory組屬性
要返回先前配置的組屬性值,請按一下使用者屬性和宣告旁邊的編輯。
To return the previously configured group attribute value, press User Properties and Declare Editor .
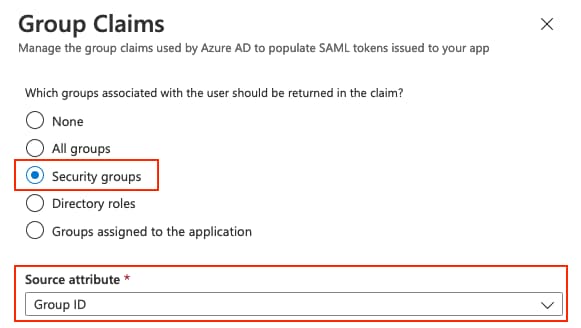
按一下Add a group claim。
Press
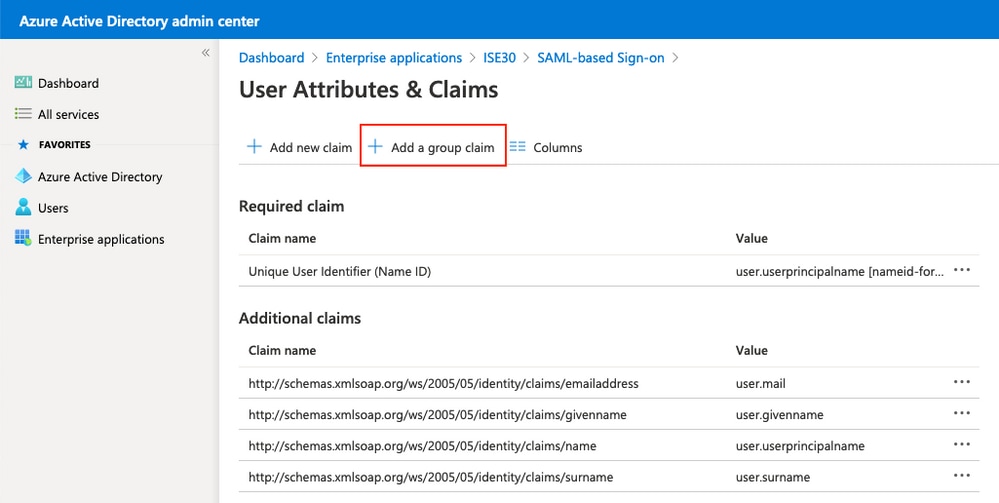
選擇Security groups,然後按一下Save。斷言中返回的Source屬性是組ID,它是之前獲取的組對象ID。
Select
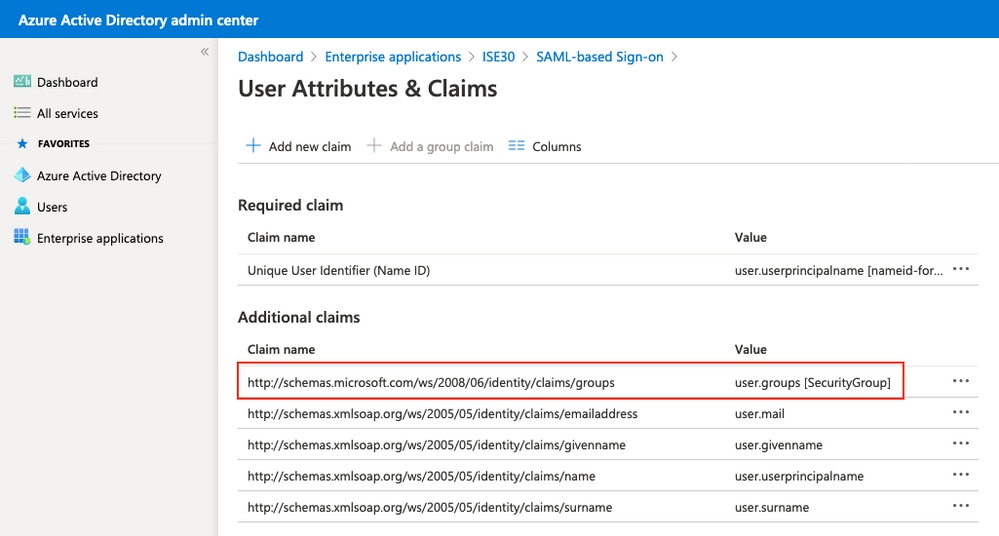
記下組的申請名稱。在本例中,它是http://schemas.microsoft.com/ws/2008/06/identity/claims/groups。
Take note of the name of http://schemas.microsft.com/ws/2008/06/identity/claims/groups.
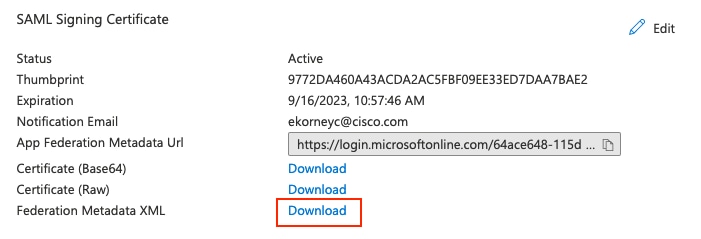
8.下載Azure聯合後設資料XML檔案
在SAML簽名證書中按一下Download on Federation Metadata XML。
Press Download on Document Metadata XML in the signing certificate .
導航到管理>身份管理>外部身份源> SAML Id提供程式> [您的SAML提供程式]。
Lead to administration> identity management> external identity source> SAML Id supply program> [Your SAML supply program].
切換到Identity Provider Config頁籤,然後按一下Browse按鈕。從下載Azure聯合後設資料XML步驟中選擇「聯合後設資料XML檔案」,然後按一下「儲存」。
Switch to IdentityProviderConfig, then press the Browse button. Select "Standup XML" from the downloading Azure postdata XML step, and click to save
切換到頁籤Groups,並將Claim name的值從Configure Active Directory Group attribute 貼上到Group Membership Attribute中。 Switch to page 按一下「Add」。使用將Azure Active Directory使用者分配給組時捕獲的發起人組的組對象ID值填充Assertion中的Name。在ISE中配置具有有意義值的名稱,在這種情況下為Azure發起人組。按一下「OK」(確定)。按一下 儲存。 Click on Add. Use to assign the user of Azure Active Directory to the team to capture the launcher group to fill the Assertion's Name in ID 這會在Azure中的組與可在ISE上使用的組名稱之間建立對映。 This will create a dichotomy between the group in Azure and the name that can be used on ISE. . 導航到工作中心>訪客訪問>門戶和元件>發起人組,然後選擇要對映到Azure AD組的發起人組。在此示例中,使用了ALL_ACCOUNTS(預設值)。 Leads to the 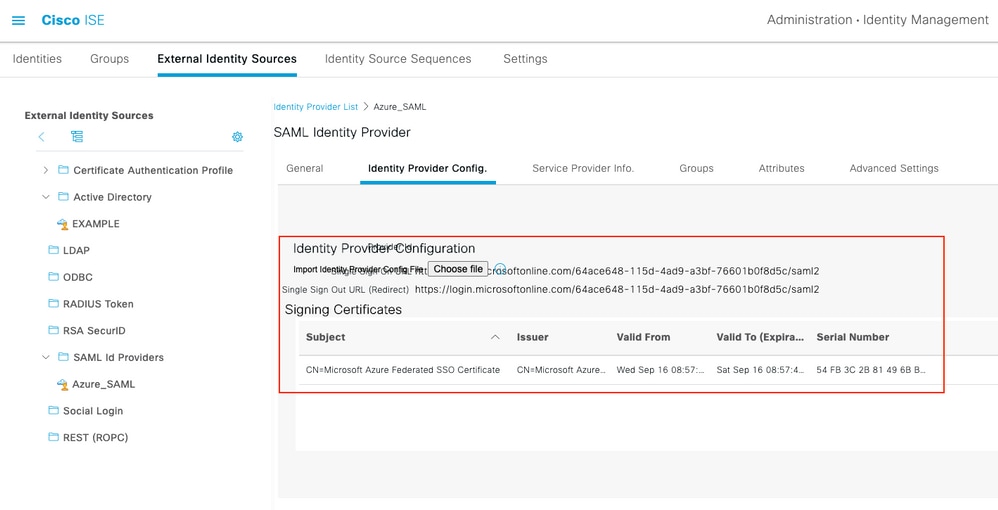
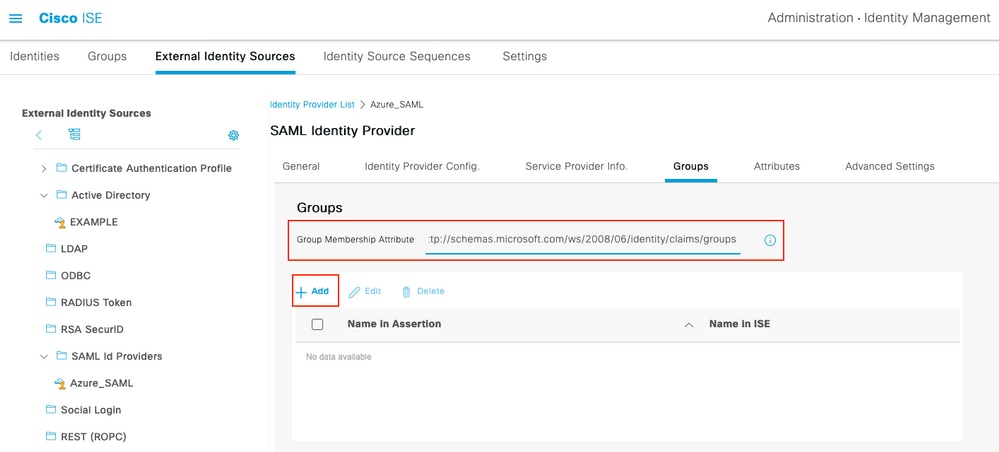
/strang >.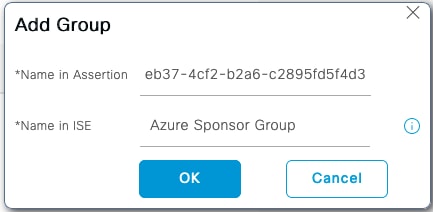
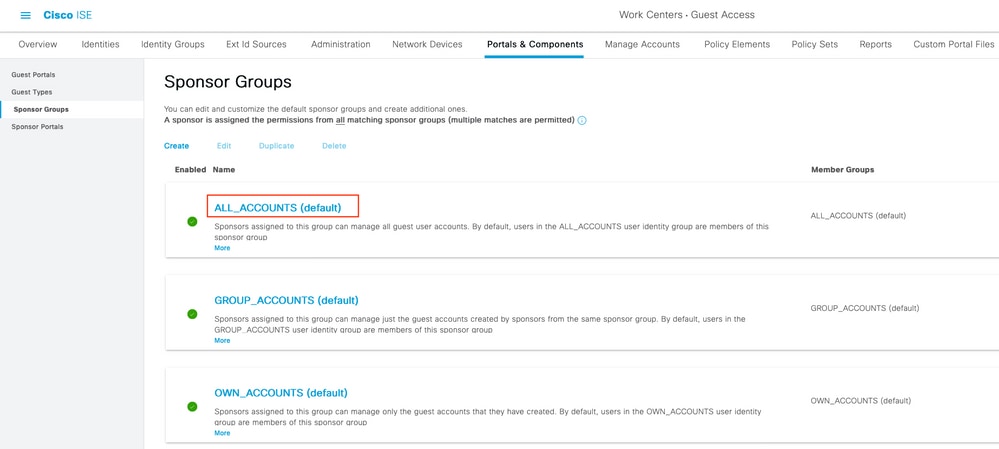
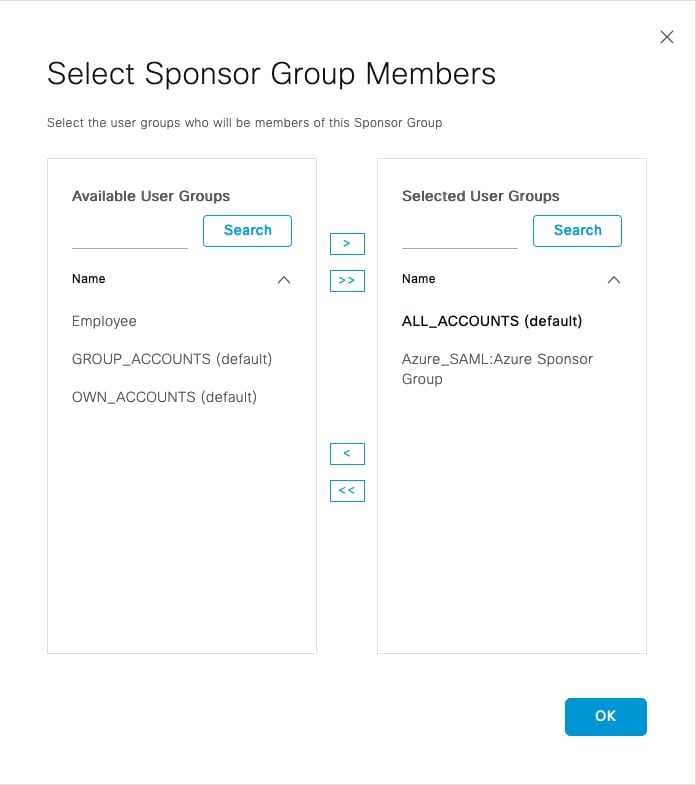
按一下成員…… 並將Azure_SAML:Azure發起人組新增到所選使用者組。這會將Azure中的發起人組對映到ALL_ACCOUNTS發起人組。按一下OK。按一下Save。
Press strong member
使用本節內容,確認您的組態是否正常運作。
Use the contents of this section to verify that your configuration is working properly.
現在,如果您開啟發起人門戶(例如,從測試URL),您將重定向到Azure進行登入,然後返回到發起人門戶。
Now, if you open the sender's home (for example, from the test URL), you will be redirected to Azure for login and then return to the sender's home.
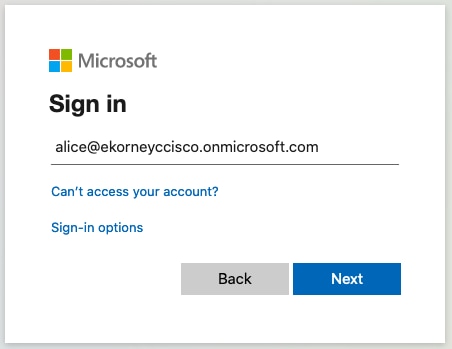
1.啟動發起人門戶,在門戶測試URL連結上使用其FQDN。ISE應將您重定向到Azure登入頁面。輸入username create earlier並按一下Next。
ISE shall direct you back to Azure to enter the page. Enter username recorder and press
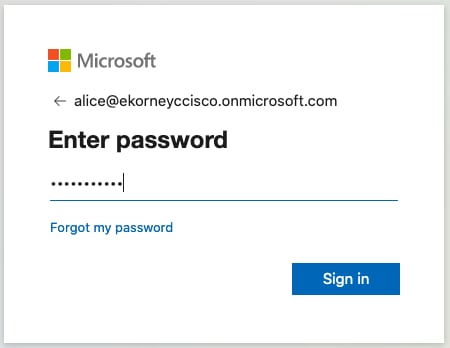
2.輸入密碼,然後按一下Sign In。IdP登入螢幕會將使用者重定向到初始ISE的發起人門戶。
Enter the password and press SignIn.
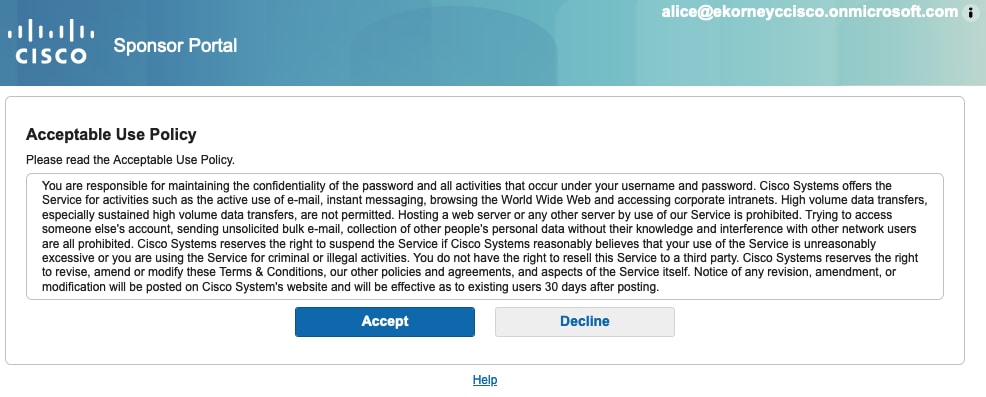
3.接受AUP。
3. Accept AUP.
4.此時,發起人使用者應具有對ALL_ACCOUNTS發起人組許可權的門戶的完全訪問許可權。
At this time, senders should have full access to to the user of ALL_ACCOUNTS.

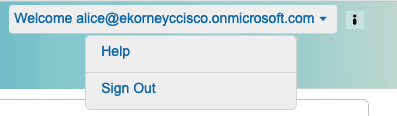
5.按一下「歡迎」下拉選單下的註銷。
Press to delete under "Welcome".
6.使用者應成功註銷,然後再次重定向到登入螢幕。
6. Users should be successful and then reoriented to the screen.
本節提供的資訊可用於對組態進行疑難排解。
The information provided in this section can be used to make the composition difficult.
瞭解在瀏覽器和Azure Active Directory之間處理SAML身份驗證至關重要。因此,您可以直接從身份提供程式(Azure)獲取與身份驗證相關的錯誤,其中ISE參與尚未啟動。
Understanding the importance of handling SAML identification between the browser and Azure Active Directory is important. Therefore, you can retrieve the error associated with the authentication directly from the Azure provider, in which ISE involvement has not yet started.
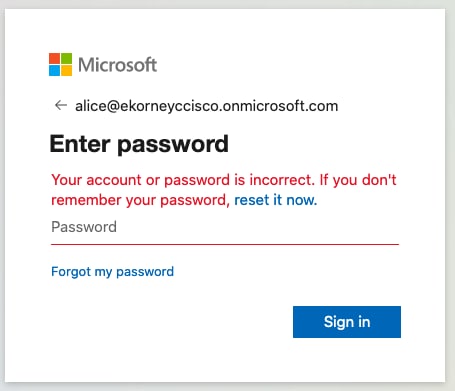
問題1.使用者輸入錯誤的密碼,未在ISE上處理使用者資料,該問題直接來自IdP(Azure)。 若要修正:重置密碼或提供正確的密碼資料。
Question 1. The user entered the wrong password and did not process the user data on ISE, which came directly from IdP (Azure). To amend: Reset the password or provide the correct password data.
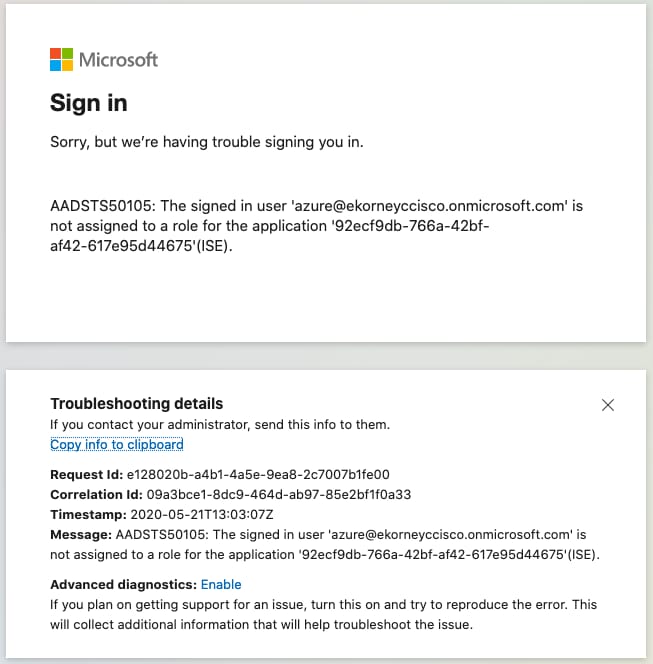
問題2.使用者不屬於應該允許訪問SAML SSO的組,同樣在本例中,未在ISE上處理使用者資料,問題直接來自IdP(Azure)。 若要修正:驗證Add group to the Application configuration步驟是否正確執行。
Question 2. The user does not belong to the group that should be allowed to visit SAML SSO. In the same case, the user data is not processed on ISE and the question is directly from IdP (Azure). To amend: whether the Add group to the Application control step is correctly carried out.
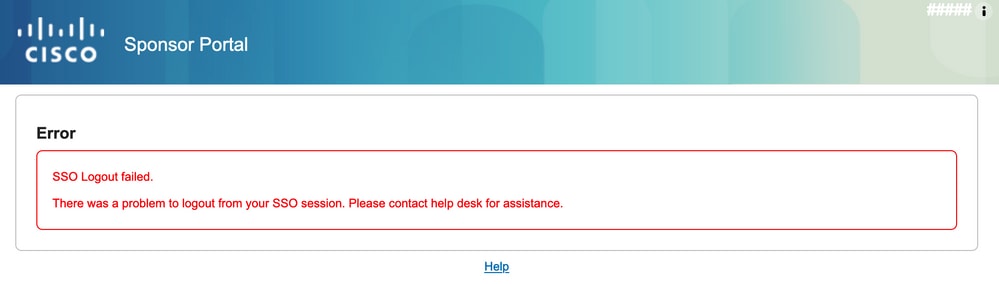
3. Sing Out未按預期工作,出現此錯誤 — 「SSO註銷失敗」。從您的SSO會話註銷時出現問題。請聯絡幫助台以獲得幫助。」 當在SAML IdP上未正確配置註銷URL時,即可看到這種情況。在這種情況下,此URL使用的是「https://sponsor30.example.com:8445/sponsorportal/SSOLogoutRequest.action?portal=100d02da-9457-41e8-87d7-0965b0714db2」,而應該是「https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action」才能修正:在Azure IdP的註銷URL中輸入正確的URL。
3. Sing Out did not work as expected, and this error occurred - "SSO failed". Problems arose when your SSO session was cancelled. Contact help desk for help." This is what happens when the URL is not properly configured on SAML IdP. In this case, the URL is used as "
若要驗證是否收到SAML負載,可以使用Web Developer Tools。如果使用Firefox,請導航到Tools > Web Developer > Network,然後使用Azure憑據登入到門戶。在Params頁籤中,可以看到加密的SAML響應:
If you want to verify that a SAML load has been received, you can use Web Development Tools. If you use Firefox, you can use navigation to
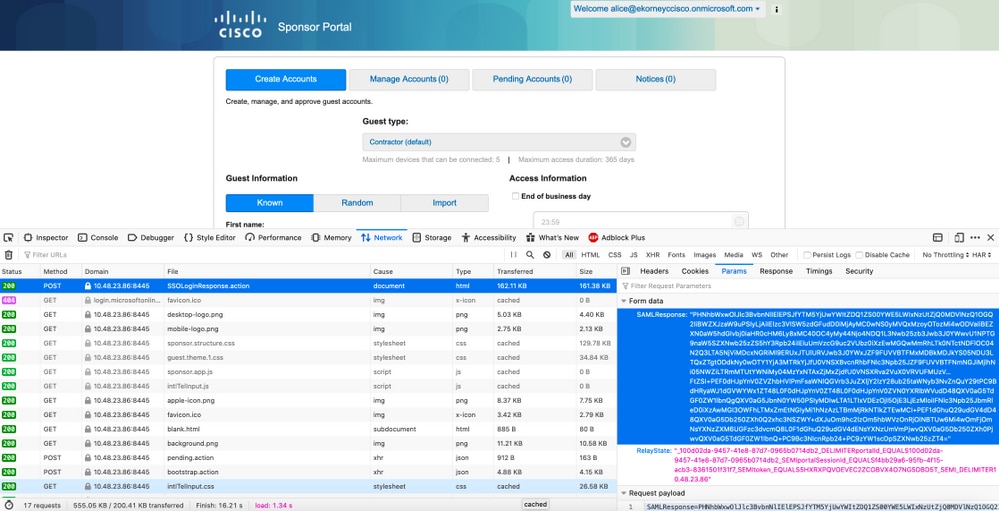
此處的元件的日誌級別應在ISE上更改。導航到操作>故障排除>調試嚮導>調試日誌配置。
The size of the widget here should be changed on ISE . the navigation to operation > troubleshoot > test guide > test journal configuration.
| 元件名稱 | 日誌級別 | 日誌檔名 |
| 訪客接入 | 調試 | guest.log |
| portal-web-action | 調試 | guest.log |
| opensaml | 調試 | ise-psc.log |
| saml | 調試 | ise-psc.log |
正確流執行時調試的工作集(ise-psc.log):
Workset (ose-psc.log):
1.使用者從發起人門戶重定向到IdP URL。
1. The user redirects from the sender to the IdP URL.
2020-09-16 10:43:59,207 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Azure_SAML
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM. IDP URL:
https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SPProviderId for Azure_SAML is: http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Azure_SAML
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML request - providerId (as should be found in IdP configuration):
http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML request - returnToId (relay state):
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId_EQUALSbd48c1a1-9477-4746-8e40-e43d20c9f429_SEMIportalSessionId_EQUALS8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_SEMItoken_EQUALSOA6CZJQD7X67TLYHE4Y3EM3EY097E2J_SEMI_DELIMITERsponsor30.example.com
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML request - spUrlToReturnTo:
https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action
2.從瀏覽器接收SAML響應。
2. Receive the SAML response from the browser.
2020-09-16 10:44:11,122 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,126 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:
portalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;
2020-09-16 10:44:11,126 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State
:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,126 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:
portalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;
2020-09-16 10:44:11,129 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,129 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:
portalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;
2020-09-16 10:44:11,133 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,134 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:
portalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;
2020-09-16 10:44:11,134 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,134 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML flow initiator PSN's Host name is:sponsor30.example.com
2020-09-16 10:44:11,134 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Is redirect requiered: InitiatorPSN:sponsor30.example.com
This node's host name:ISE30-1ek LB:null request Server Name:sponsor30.example.com
2020-09-16 10:44:11,182 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- This node is the initiator (sponsor30.example.com) this node host name is:sponsor30.example.com
2020-09-16 10:44:11,184 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.parse.BasicParserPool -::::- Setting DocumentBuilderFactory attribute 'http://javax.xml.XMLConstants/feature/secure-processing'
2020-09-16 10:44:11,187 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.parse.BasicParserPool -::::- Setting DocumentBuilderFactory attribute 'http://apache.org/xml/features/disallow-doctype-decl'
2020-09-16 10:44:11,190 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Beginning to decode message from inbound transport of type: org.opensaml.ws.transport.http.HttpServletRequestAdapter
2020-09-16 10:44:11,190 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.saml2.binding.decoding.HTTPPostDecoder -::::- Decoded SAML relay state of:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId_EQUALSbd48c1a1-9477-4746-8e40-e43d20c9f429_SEMIportalSessionId_EQUALS8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_SEMItoken_EQUALSOA6CZJQD7X67TLYHE4Y3EM3EY097E2J_SEMI_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,190 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.saml2.binding.decoding.HTTPPostDecoder -::::- Getting Base64 encoded message from request
2020-09-16 10:44:11,191 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Parsing message stream into DOM document
2020-09-16 10:44:11,193 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Unmarshalling message DOM
2020-09-16 10:44:11,195 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Starting to unmarshall Apache XML-Security-based SignatureImpl element
2020-09-16 10:44:11,195 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Constructing Apache XMLSignature object
2020-09-16 10:44:11,195 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Adding canonicalization and signing algorithms, and HMAC output length to Signature
2020-09-16 10:44:11,195 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Adding KeyInfo to Signature
2020-09-16 10:44:11,197 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Message succesfully unmarshalled
2020-09-16 10:44:11,197 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.saml2.binding.decoding.HTTPPostDecoder -::::- Decoded SAML message
2020-09-16 10:44:11,197 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.saml2.binding.decoding.BaseSAML2MessageDecoder -::::- Extracting ID, issuer and issue instant from status response
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- No security policy resolver attached to this message context, no security policy evaluation attempted
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Successfully decoded message.
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Checking SAML message intended destination endpoint against receiver endpoint
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Intended message destination endpoint:
https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Actual message receiver endpoint:
https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::-
SAML decoder's URIComparator - [https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action] vs. [https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action]
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::-
SAML message intended destination endpoint matched recipient endpoint
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: statusCode:urn:oasis:names:tc:SAML:2.0:status:Success
3.屬性(斷言)分析已啟動。
3. Properties (verbal) analysis initiated.
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/identity/claims/tenantid
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/identity/claims/tenantid> add value=<64ace648-115d-4ad9-a3bf-76601b0f8d5c>
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object -
attribute<http://schemas.microsoft.com/identity/claims/tenantid> value=<64ace648-115d-4ad9-a3bf-76601b0f8d5c>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/identity/claims/objectidentifier
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/identity/claims/objectidentifier> add value=<50ba7e39-e7fb-4cb1-8256-0537e8a09146>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object -
attribute<http://schemas.microsoft.com/identity/claims/objectidentifier> value=<50ba7e39-e7fb-4cb1-8256-0537e8a09146>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/identity/claims/displayname
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/identity/claims/displayname> add value=<Alice>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object -
attribute<http://schemas.microsoft.com/identity/claims/displayname> value=<Alice>
4.接收組屬性,值為f626733b-eb37-4cf2-b2a6-c2895fd5f4d3,簽名驗證。
4. Receiver group properties with f626733b-eb37-4cf2-b2a6-c2895fd5f4d3, signed .
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/ws/2008/06/identity/claims/groups
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/ws/2008/06/identity/claims/groups> add value=<f626733b-eb37-4cf2-b2a6-c2895fd5f4d3>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute
<http://schemas.microsoft.com/ws/2008/06/identity/claims/groups> value=<f626733b-eb37-4cf2-b2a6-c2895fd5f4d3>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/identity/claims/identityprovider
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/identity/claims/identityprovider> add value=<https://sts.windows.net/64ace648-115d-4ad9-a3bf-76601b0f8d5c/>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute
<http://schemas.microsoft.com/identity/claims/identityprovider> value=<https://sts.windows.net/64ace648-115d-4ad9-a3bf-76601b0f8d5c/>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/claims/authnmethodsreferences
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/claims/authnmethodsreferences> add value=<http://schemas.microsoft.com/ws/2008/06/identity/authenticationmethod/password>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute
<http://schemas.microsoft.com/claims/authnmethodsreferences> value=<http://schemas.microsoft.com/ws/2008/06/identity/authenticationmethod/password>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name> add value=<alice@ekorneyccisco.onmicrosoft.com>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute
<http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name> value=<alice@ekorneyccisco.onmicrosoft.com>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::getUserNameFromAssertion: IdentityAttribute is set to Subject Name
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::getUserNameFromAssertion: username value from Subject is=[alice@ekorneyccisco.onmicrosoft.com]
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::getUserNameFromAssertion: username set to=[alice@ekorneyccisco.onmicrosoft.com]
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: Found value for 'username' attribute assertion: alice@ekorneyccisco.onmicrosoft.com
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [SAMLAttributesParser:readDict]
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.cfg.IdentityProviderMgr -::::- getDict: Azure_SAML
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [SAMLAttributesParser:readDict]: read Dict attribute=<ExternalGroups>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.microsoft.com/identity/claims/displayname> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [cacheGroupAttr] Adding to cache ExternalGroup values=<f626733b-eb37-4cf2-b2a6-c2895fd5f4d3>
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.microsoft.com/identity/claims/tenantid> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.microsoft.com/identity/claims/identityprovider> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.microsoft.com/identity/claims/objectidentifier> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.microsoft.com/claims/authnmethodsreferences> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cisco.cpm.saml.framework.SAMLSessionDataCache -::::- [storeAttributesSessionData] idStore=<Azure_SAML> userName=alice@ekorneyccisco.onmicrosoft.com>
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [SAMLAttributesParser:getEmail] The email attribute not configured on IdP
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: email attribute value:
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal ID:bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:
portalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML flow initiator PSN's Host name is:sponsor30.example.com
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Azure_SAML
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM.
IDP URL: https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SPProviderId for Azure_SAML is:
http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- ResponseValidationContext:
IdP URI: https://sts.windows.net/64ace648-115d-4ad9-a3bf-76601b0f8d5c/
SP URI: http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
Assertion Consumer URL: https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action
Request Id: _bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId_EQUALSbd48c1a1-9477-4746-8e40-e43d20c9f429_SEMIportalSessionId_EQUALS8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_SEMItoken_EQUALSOA6CZJQD7X67TLYHE4Y3EM3EY097E2J_SEMI_DELIMITERsponsor30.example.com
Client Address: 10.61.170.160
Load Balancer: null
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.SAMLSignatureValidator -::::- no signature in response
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.SAMLSignatureValidator -::::- Validating signature of assertion
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.BaseSignatureValidator -::::- Determine the signing certificate
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.BaseSignatureValidator -::::- Validate signature to SAML standard with cert:CN=Microsoft Azure Federated SSO Certificate serial:112959638548824708724869525057157788132
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.security.SAMLSignatureProfileValidator -::::- Saw Enveloped signature transform
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.security.SAMLSignatureProfileValidator -::::- Saw Exclusive C14N signature transform
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.BaseSignatureValidator -::::- Validate signature againsta signing certificate
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.signature.SignatureValidator -::::- Attempting to validate signature using key from supplied credential
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.signature.SignatureValidator -::::- Creating XMLSignature object
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.signature.SignatureValidator -::::- Validating signature with signature algorithm URI: http://www.w3.org/2001/04/xmldsig-more#rsa-sha256
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.signature.SignatureValidator -::::- Validation credential key algorithm 'RSA', key instance class 'sun.security.rsa.RSAPublicKeyImpl'
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.signature.SignatureValidator -::::- Signature validated with key from supplied credential
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.SAMLSignatureValidator -::::- Assertion signature validated succesfully
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.WebSSOResponseValidator -::::- Validating response
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.WebSSOResponseValidator -::::- Validating assertion
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.AssertionValidator -::::- Assertion issuer succesfully validated
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.AssertionValidator -::::- Authentication statements succesfully validated
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.AssertionValidator -::::- Subject succesfully validated
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.AssertionValidator -::::- Conditions succesfully validated
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: validation succeeded for alice@ekorneyccisco.onmicrosoft.com
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: found signature on the assertion
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Retrieve [CN=Microsoft Azure Federated SSO Certificate] as signing certificates
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: loginInfo:SAMLLoginInfo: name=alice@ekorneyccisco.onmicrosoft.com,
format=urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, sessionIndex=_4b798ec4-9aeb-40dc-8bed-6dd2fdd46800, time diff=26329
2020-09-16 10:44:11,292 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- AuthenticatePortalUser - Session:null IDPResponse:
IdP ID: Azure_SAML
Subject: alice@ekorneyccisco.onmicrosoft.com
SAML Status Code:urn:oasis:names:tc:SAML:2.0:status:Success
SAML Success:true
SAML Status Message:null
SAML email:
SAML Exception:nullUserRole : SPONSOR
2020-09-16 10:44:11,292 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- AuthenticatePortalUser - about to call authenticateSAMLUser messageCode:null subject:alice@ekorneyccisco.onmicrosoft.com
2020-09-16 10:44:11,306 INFO [RMI TCP Connection(346358)-127.0.0.1][] api.services.server.role.RoleImpl -::::- Fetched Role Information based on RoleID: 6dd3b090-8bff-11e6-996c-525400b48521
2020-09-16 10:44:11,320 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cisco.cpm.saml.framework.SAMLSessionDataCache -::::- [SAMLSessionDataCache:getGroupsOnSession] idStore=<Azure_SAML> userName=<alice@ekorneyccisco.onmicrosoft.com>
2020-09-16 10:44:11,320 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cisco.cpm.saml.framework.SAMLSessionDataCache -::::- [getAttributeOnSession] idStore=<Azure_SAML> userName=<alice@ekorneyccisco.onmicrosoft.com> attributeName=<Azure_SAML.ExternalGroups>
5.將使用者組新增到身份驗證結果中,以便門戶可以使用它,通過SAML身份驗證。
Add user groups to the identification results so that users can use them and pass the SAML identification.
2020-09-16 10:44:11,320 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- AuthenticatePortalUser - added user groups from SAML response to AuthenticationResult, all retrieved groups:[f626733b-eb37-4cf2-b2a6-c2895fd5f4d3]
2020-09-16 10:44:11,320 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Authenticate SAML User - result:PASSED
6.註銷已觸發。SAML響應中接收到註銷URL;https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action。
6. The release has been triggered. .
2020-09-16 10:44:51,462 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM. IDP URL: https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:44:51,462 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- getLogoutMethod - method:REDIRECT_METHOD_LOGOUT
2020-09-16 10:44:51,462 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- getSignLogoutRequest - null
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.MessageComposer -:::alice@ekorneyccisco.onmicrosoft.com:- buildLgoutRequest - loginInfo:SAMLLoginInfo: name=alice@ekorneyccisco.onmicrosoft.com, format=urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, sessionIndex=_4b798ec4-9aeb-40dc-8bed-6dd2fdd46800, time diff=26329
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Azure_SAML
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM. IDP URL: https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- SPProviderId for Azure_SAML is: http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.MessageComposer -:::alice@ekorneyccisco.onmicrosoft.com:- buildLgoutRequest - spProviderId:http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.MessageComposer -:::alice@ekorneyccisco.onmicrosoft.com:- buildLgoutRequest - logoutURL:https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:44:53,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal ID:bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:53,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML flow initiator PSN's Host name is:sponsor30.example.com
2020-09-16 10:44:53,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Is redirect requiered: InitiatorPSN:sponsor30.example.com This node's host name:ISE30-1ek LB:null request Server Name:sponsor30.example.com
2020-09-16 10:44:53,248 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- This node is the initiator (sponsor30.example.com) this node host name is:sponsor30.example.com
2020-09-16 10:44:53,249 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,249 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:8fa19bf2-9fa6-4892-b082-5cdabfb5daa1
2020-09-16 10:44:53,250 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] org.opensaml.xml.parse.BasicParserPool -::::- Setting DocumentBuilderFactory attribute 'http://javax.xml.XMLConstants/feature/secure-processing'
2020-09-16 10:44:53,251 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] org.opensaml.xml.parse.BasicParserPool -::::- Setting DocumentBuilderFactory attribute 'http://apache.org/xml/features/disallow-doctype-decl'
2020-09-16 10:44:53,253 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Beginning to decode message from inbound transport of type: org.opensaml.ws.transport.http.HttpServletRequestAdapter
2020-09-16 10:44:53,253 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.saml2.binding.decoding.HTTPRedirectDeflateDecoder -::::- Decoded RelayState: _bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,253 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.saml2.binding.decoding.HTTPRedirectDeflateDecoder -::::- Base64 decoding and inflating SAML message
2020-09-16 10:44:53,253 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Parsing message stream into DOM document
2020-09-16 10:44:53,256 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Unmarshalling message DOM
2020-09-16 10:44:53,256 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Message succesfully unmarshalled
2020-09-16 10:44:53,256 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.saml2.binding.decoding.HTTPRedirectDeflateDecoder -::::- Decoded SAML message
2020-09-16 10:44:53,256 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.saml2.binding.decoding.BaseSAML2MessageDecoder -::::- Extracting ID, issuer and issue instant from status response
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- No security policy resolver attached to this message context, no security policy evaluation attempted
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Successfully decoded message.
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Checking SAML message intended destination endpoint against receiver endpoint
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Intended message destination endpoint: https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Actual message receiver endpoint: https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML decoder's URIComparator - [https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action] vs. [https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action]
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- SAML message intended destination endpoint matched recipient endpoint
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: statusCode:urn:oasis:names:tc:SAML:2.0:status:Success
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal ID:bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:8fa19bf2-9fa6-4892-b082-5cdabfb5daa1
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML flow initiator PSN's Host name is:sponsor30.example.com
2020-09-16 10:44:53,258 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Azure_SAML
2020-09-16 10:44:53,258 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM. IDP URL: https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:44:53,258 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SPProviderId for Azure_SAML is: http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:53,258 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- ResponseValidationContext:
IdP URI: https://sts.windows.net/64ace648-115d-4ad9-a3bf-76601b0f8d5c/
SP URI: http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
Assertion Consumer URL: https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action
Request Id: _bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
Client Address: 10.61.170.160
Load Balancer: null
2020-09-16 10:44:53,259 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.validators.SAMLSignatureValidator -::::- LogoutResponse signature validated succesfully
2020-09-16 10:44:53,259 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.validators.SAMLSignatureValidator -::::- This is LogoutResponse (only REDIRECT is supported) no signature is on assertion, continue
2020-09-16 10:44:53,259 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.validators.WebSSOResponseValidator -::::- Validating response
2020-09-16 10:44:53,259 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.validators.WebSSOResponseValidator -::::- Validating assertion
2020-09-16 10:44:53,259 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: validation succeeded for null
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。












