钓鱼揭秘之谷歌虚假广告钓鱼
事件背景
近日,慢雾安全团队和 Rabby Wallet 团队发现一种利用 Google 广告进行钓鱼的攻击手法。随后,慢雾安全团队联合 Rabby Wallet 团队对该攻击手法展开深入分析。
根据 Rabby Wallet 团队的描述,团队并未购买任何 Google 广告,然而这个假广告却跳转到了真正官网,莫非钓鱼团伙花钱推广真钱包?
从 Google 搜索关键字情况来看,排在前两位的搜索结果都为钓鱼广告,然而第一条广告的链接却很反常,它显示的明明是 Rabby Wallet 的官方网站地址 https://rabby.io,钓鱼团伙为什么要这么做呢?
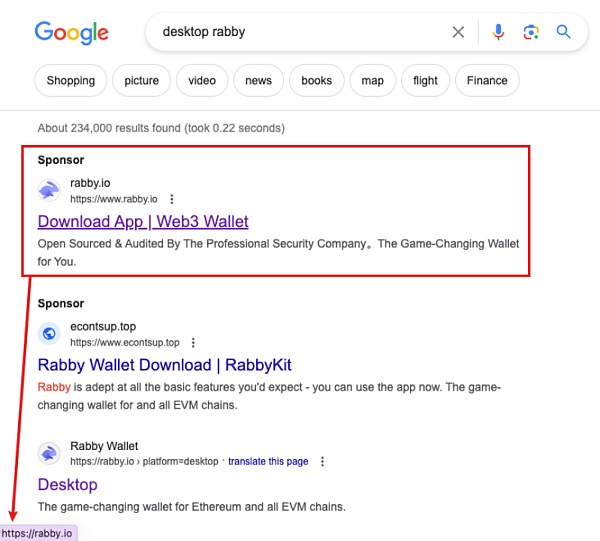
通过跟踪发现,钓鱼广告有时会跳转到真正官方地址 https://rabby.io,而在多次更换代理到不同地区后,则会跳转到钓鱼地址 http://rebby.io,并且该钓鱼地址会更新改变。在编写本文时,该链接跳转到钓鱼地址 https://robby.page[.]link/Zi7X/?url=https://rabby.io?gad_source=1。
技术分析
我们先说下什么是 302,302 是一种 HTTP 状态代码,代表临时重定向(Found)。当服务器收到客户端的请求后,如果需要临时将请求的资源转移到另一个位置,就会返回 302 状态码,同时在响应头中包含一个 Location 字段,指示客户端应该重定向到的新位置。这种重定向是临时性的。
经过分析发现,该钓鱼广告的链接会经过多次的 302 跳转,如下图所示,使用 curl 命令请求该链接,第一次会 302 跳转到钓鱼地址 https://rabby.iopost.ivsquarestudio.com,然而在第二次 302 跳转时却出现了两种情况:
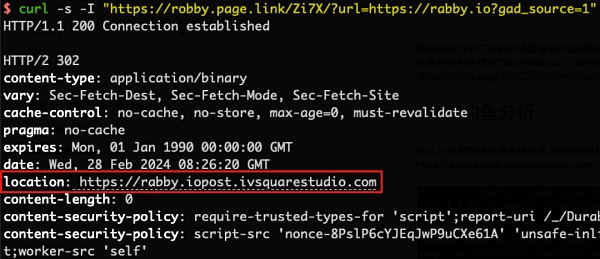
1. 当我们使用 curl 命令请求上述 Location 地址 https://rabby.iopost.ivsquarestudio.com,会 302 跳转到真正官方地址 https://rabby.io。
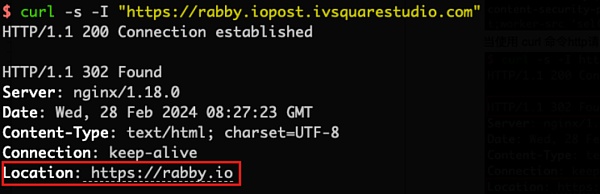
2. 但是,在我们使用 curl 命令模拟正常浏览器请求上述 Location 地址 https://rabby.iopost.ivsquarestudio.com 的情况下(携带请求头包括 User-Agent、Accept、Referer、Accept-Encoding 等字段),则会 302 跳转到一个新的 Location 地址 https://dnovomedia.com?uid=087aa42d-724b-4a1e-bae7-f1f700ce71e6。
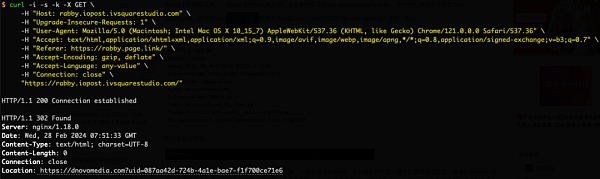
由此可见,钓鱼链接在第二次 302 跳转时会进行一次判断,当检测到非正常浏览器的请求时,会重定向到官方地址;而检测到正常浏览器的请求行为并且地区合理,则重定向到钓鱼地址。
我们跟踪发现最后一次跳转的钓鱼地址为 https://rabbyo.com/index.php?uid=087aa42d-724b-4a1e-bae7-f1f700ce71e6。
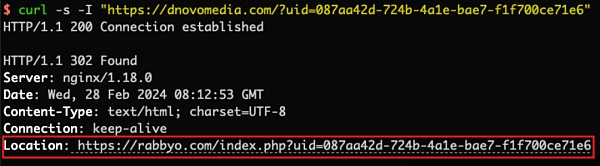
打开该钓鱼链接,发现这个钓鱼页面几乎克隆了真官网网页的大部分内容:
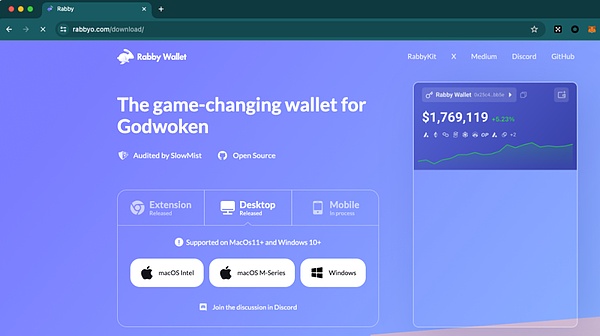
通过跟踪 302 跳转,我们发现以下钓鱼链接地址:
https://robby.page.link/Zi7X
https://rabby.iopost.ivsquarestudio.com
https://dnovomedia.com?uid=087aa42d-724b-4a1e-bae7-f1f700ce71e6
https://rabbyo.com
https://rebby.io
通过威胁情报平台查询 rebby.io 和 rabbyo.com 这两个钓鱼域名,发现它们的注册时间均在 2024 年 1 月份。


木马分析
查看代码,发现攻击者使用的是俄语:

钓鱼部署后台程序使用 Fastpanel(Fastpanel 是俄语地区主机商开发的虚拟主机管理面板):

接着对钓鱼网页的源代码进行审查发现,点击下载桌面版本会进行一次客户端校验:
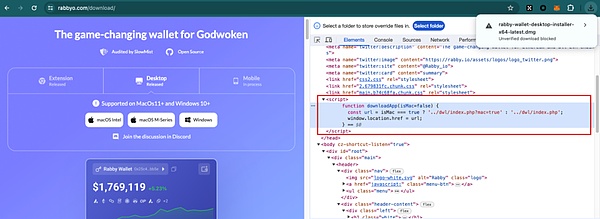
如果检查发现当前环境为 Mac 电脑,则会跳转到下载地址 https://brandsrocket.com/data/rabby-wallet-desktop-installer-x64-latest.dmg。
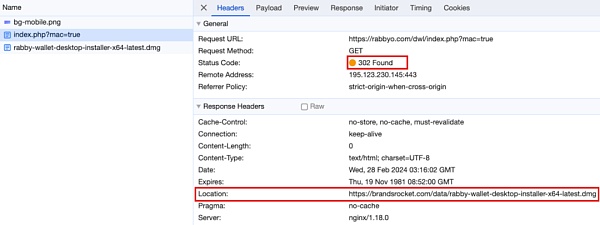
可以发现该木马程序占用的存储空间非常小,只有 1.1 MB:

将木马程序上传到在线威胁分析网站上进行分析,发现该木马样本在编写本文 19 天前已经被分析过,并被多个杀毒引擎识别为木马后门程序。
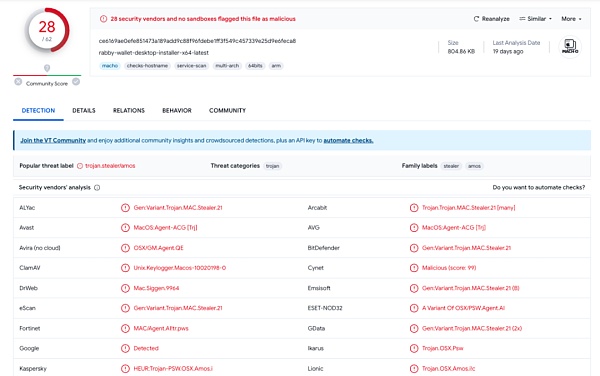
(https://www.virustotal.com/gui/file/ce6169ae0efe851473a189add9c88f96fdebe1ff3f549c457339e25d9e6feca8/detection)
钓鱼背后的技术
可以看到,从广告投放到钓鱼网站制作,再到木马制作,钓鱼团伙一套操作下来行云流水。让人看不懂的是,为何谷歌搜索的广告信息显示的是官方地址?又为何后续经过了多次的 302 跳转?分析发现,关键操作在于钓鱼团伙利用了 Google 自家的 Firebase 短链接服务的 302 跳转来欺骗谷歌的展示。
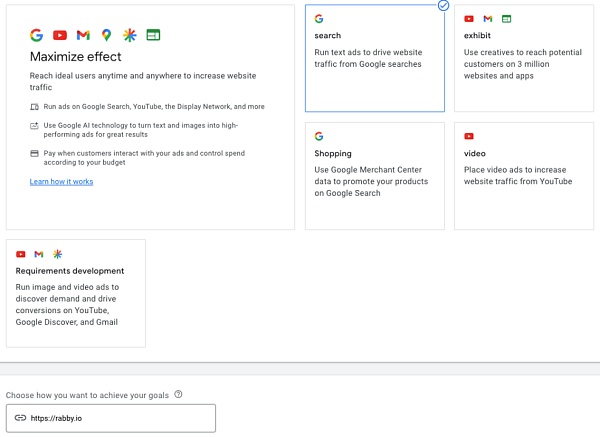
为了使这个过程更清楚,我们还需要先了解 Google 广告的投放机制(只要拥有谷歌账号,就可以登录谷歌的广告管理站点 https://ads.google.com 进行推广设置):
1. 首先,需要在广告管理站点新建一个目标为网站流量,类型为搜索的广告系列。
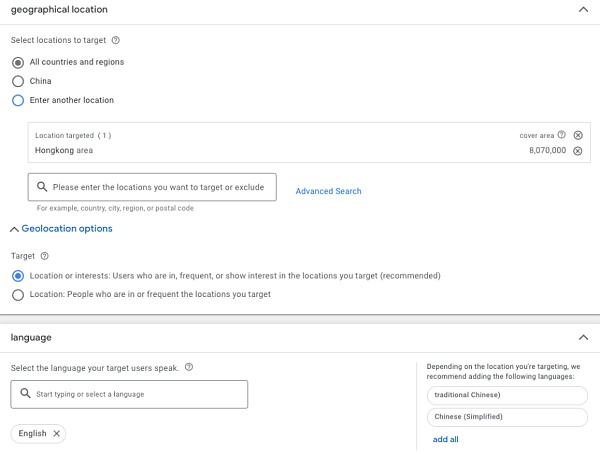
2. 设置广告投放的价格和投放次数信息后,选择广告投放的地区和语言。这里也解释了为什么在不同地区或者不同语言环境下搜索关键字不一定会出现广告。
3. 到了关键一步,设置跟踪模版。跟踪模板是 Google Ads 的一项高级功能,允许第三方跟踪广告链接。
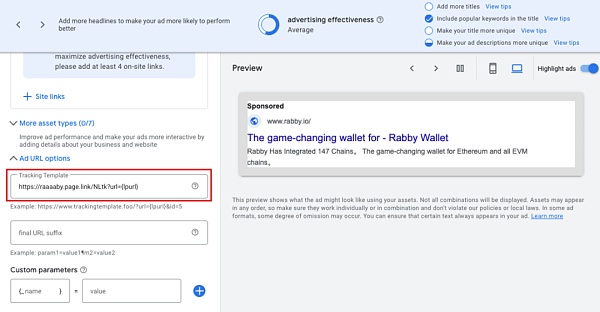
我们注意到钓鱼页面用的第一个跳转链接域名为 page.link,这个其实是谷歌的 Firebase 的一个短地址服务,该服务允许绑定任意的重定向地址到 page.link 的一个子域名中。
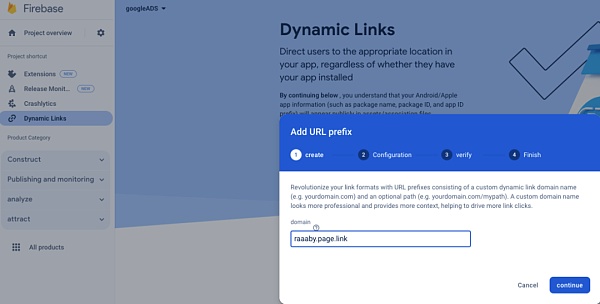
由于第三方跟踪链接需要是经过谷歌认证过的地址,而 page.link 刚好是谷歌自家的域名,于是钓鱼团伙绕过了这个限制。
4. 广告投放出去后,由于谷歌并不会实时检查 302 跳转的链接是否发生了改变,也不会实时修改广告信息,因此钓鱼团伙会在广告投放一段时间后,修改重定向到钓鱼网址。
类似的钓鱼套路还出现在各种聊天软件上。以 Telegram 这款聊天软件为例,当聊天时发送一个 URL 链接,Telegram 后台会抓取 URL 链接域名、标题和图标进行预览展示。
(此图仅供演示)
然而,在抓取预览信息时,Telegram 并没有阻止 302 跳转。因此,如果用户只根据页面的信息判断,然后点击链接,则可能跳转到预设的钓鱼地址中。
总结
请广大用户认准 Rabby 钱包官方地址 https://rabby.io,不可相信任何搜索结果显示出来的广告投放地址;如果不幸中招,请第一时间转移钱包资金,并对个人电脑进行全面的杀毒排查;平常在点击网站链接前要保留一份怀疑;更多的安全知识建议阅读慢雾安全团队出品的《区块链黑暗森林自救手册》:https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README_CN.md。
Event background Recently, the slow fog security team and the team found an attack method of fishing by advertising, and then the slow fog security team and the team conducted an in-depth analysis of the attack method. According to the team's description, the team did not buy any advertisements, but this fake advertisement jumped to the real official website Murphy fishing gang to spend money to promote the real wallet. From the search keywords, the top two search results are all fishing advertisements, but the link of the first advertisement is abnormal, and it shows that it is obviously an official. Why do phishing gangs do this? Through tracking, it is found that phishing advertisements sometimes jump to the real official address, but after changing agents to different regions for many times, they will jump to the phishing address, and the phishing address will be updated and changed. At the time of writing this article, the link jumps to the phishing address. Technical analysis, let's first talk about what a status code represents temporary redirection. When the server receives the request from the client, it will temporarily transfer the requested resources to another location if necessary. At the same time, the return status code contains a field in the response header to indicate the new location to which the client should redirect. This redirection is temporary. After analysis, it is found that the link of the phishing advertisement will go through many jumps, as shown in the figure below. When using the command to request the link, it will jump to the phishing address for the first time. However, there are two situations when we use the command to request the above address, it will jump to the real official address, but when we use the command to simulate a normal browser to request the above address. In the case of address, it will jump to a new address with the request header and other fields, so it can be seen that the phishing link will make a judgment when it jumps for the second time. When it detects the request of an abnormal browser, it will be redirected to the official address, and when it detects the request behavior of a normal browser and the area is reasonable, it will be redirected to the phishing address. We tracked and found the phishing address that jumped for the last time. In order to open the phishing link, we found that this phishing page almost cloned most of the contents of the real official website webpage. Following the jump, we found that the following phishing link addresses were queried by the threat intelligence platform and these two phishing domain names, and their registration time was found in the year and month. Trojan horse analysis and code inspection found that the attacker used Russian phishing deployment background program and used the virtual host management panel developed by the host vendor in Russian-speaking areas. Then, the source code of the phishing webpage was reviewed and it was found that clicking to download the desktop version would conduct a client check, and if the current environment was found to be a computer, it would jump to download. The address can be found that the storage space occupied by the Trojan is very small. Only by uploading the Trojan to the online threat analysis website for analysis, it is found that the Trojan sample has been analyzed and recognized as a Trojan backdoor program by several anti-virus engines days before the writing of this article. The technology behind fishing can be seen from advertising to phishing website production to Trojan fishing gang production. What people can't understand is why the advertising information searched by Google shows the official address. Why did the following jump analysis find that the key operation is that the phishing gang used its own short link service to cheat Google's display? In order to make this process more clear, we need to understand the advertising delivery mechanism first. As long as we have a Google account, we can log in to Google's advertising management site for promotion settings. First, we need to create a new target on the advertising management site, and set the advertising price and delivery times information for the advertising series with the website traffic type as search. Choosing the region and language of advertising also explains why searching for keywords in different regions or different language environments does not necessarily lead to advertisements. The key step is to set up a tracking template, which is an advanced function to allow third parties to track advertising links. We noticed that the first jump link domain name used in phishing pages is actually a short url service of Google, which allows binding any redirection address to a subdomain, because third parties track links. What is needed is an address that has been authenticated by Google, but it happens to be Google's own domain name, so the phishing gang bypasses this restriction. After the advertisement is put out, Google will not check whether the jumped link has changed in real time, nor will it modify the advertisement information in real time. Therefore, the phishing gang will modify and redirect to the phishing website after the advertisement is put in for a period of time. Similar phishing routines also appear on various chat software. Take this chat software as an example. When chatting, a link is sent and the background will grab the linked domain name. The title and icon are previewed. This picture is only for demonstration. However, when grabbing the preview information, it does not prevent jumping. Therefore, if the user only judges according to the information on the page and then clicks on the link, he may jump to the preset fishing address to summarize. Please identify the official address of the wallet and do not trust the advertising address displayed in any search results. If you are unfortunately recruited, please transfer the wallet funds at the first time and conduct a comprehensive anti-virus investigation on the personal computer. Usually, you should keep a copy of the safety knowledge that is suspicious before clicking on the website link. It is recommended to read the blockchain dark forest self-help manual produced by the slow fog security team 比特币今日价格行情网_okx交易所app_永续合约_比特币怎么买卖交易_虚拟币交易所平台
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群
1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。