進階加密标准(英語:,缩写:),又称Rijndael加密法(荷兰语发音:[?r?inda?l],音似英文的「Rhine doll」),是美国联邦政府采用的一種區塊加密标准。
進階加密标准(英語:,缩写:),又称Rijndael加密法(荷兰语发音:[?r?inda?l],音似英文的「Rhine doll」),是美国联邦政府采用的一種區塊加密标准。这个标准用来替代原先的DES,已經被多方分析且廣為全世界所使用。經過五年的甄選流程,進階加密標準由美國國家標準與技術研究院(NIST)於2001年11月26日發佈於FIPS PUB 197,並在2002年5月26日成為有效的標準。現在,進階加密标准已然成為对称密钥加密中最流行的演算法之一。
Advanced Encryption Standard & #xff08; English & #xff1a; xff0c; xff1a; xff09; ff0c; also known as Rijndael Encryption method
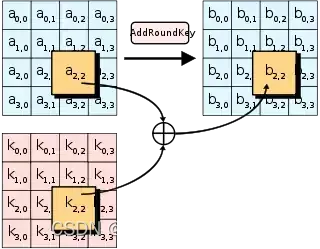
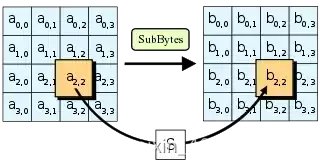
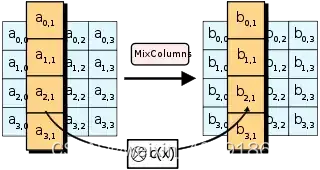
SubBytes是AES演算法四步驟之一。 SubBytes is one of the four steps of the AES algorithm. 该演算法為比利时密码学家Joan Daemen和Vincent Rijmen所設計,結合兩位作者的名字,以Rijndael為名投稿進階加密標準的甄選流程。 The algorithm was designed by Belgian cryptographers Joan Daemen and Vincent Rijmen & #xff0c; the combination of two authors' names & #xff0c; and the selection process using Rijndael as an advanced encryption standard. Rijndael是由Daemen和Rijmen早期所设计的Square改良而來;而Square則是由SHARK发展而来。 Rijndael is an improved Square designed by Daemen and Rijmen earlier & #xff1b; Square is developed by SHARK. 不同於它的前任標準DES,Rijndael使用的是代换-置换网络,而非Feistel架構。 Unlike its predecessor's DES& #xff0c; Rijndael uses a proxy-to-place network & #xff0c; not a Feistel structure. 严格地说,AES和Rijndael加密法並不完全一樣(虽然在实际应用中兩者可以互换),因为Rijndael加密法可以支援更大範圍的區塊和密钥长度:AES的區塊長度固定為128位元,密钥长度則可以是128,192或256位元;而Rijndael使用的密钥和區塊长度均可以是128,192或256位元。加密過程中使用的密钥是由Rijndael密钥生成方案產生。 Strictly xff0c; AES and encryption is not exactly the same xff08; although in practical applications the two are interchangeable xff09; xff0c; because the Rijndael encryption can support larger block and key lengths xff1a; AES block lengths are fixed at 128bit < xfffx0c; the key lengths can be 128#x6x6x3x3x3x3x3x3x4x3x3x3x3x3x3x3x3x3x3x3x3x3x3x3x3x6; the keys.ints. 大多数AES计算是在一个特别的有限域完成的。 Most AES calculations are performed in a special limited area. AES加密過程是在一個4×4的位元組矩陣上運作,這個矩陣又称为「体(state)」,其初值就是一個明文區塊(矩陣中一個元素大小就是明文區塊中的一個Byte)。(Rijndael加密法因支援更大的區塊,其矩陣的「列數(Row number)」可視情況增加)加密时,各轮AES加密迴圈(除最后一轮外)均包含4个步骤: The AES encryption process operates on a 4x4 byte matrix xff0c; this matrix is also known as xff08; state&xff09; xff0c; the initial value is an explicit block xff08; the size of an element in the matrix is a Byte) ff08; xff08; Rijndael encryption for supporting a larger block xff0c; its matrix is called xff08; Row number #xff09; xff09; xff0c; encrypting loops #xff08; #xES encryption loops #xff08; xff09; apart from the last round xff09; all contain four steps xff1a; 在AddRoundKey步驟中,將每個狀態中的位元組與該回合金鑰做异或(⊕)。 In AddRoundKey steps & #xff0c; bytes in each state are different from the key in the round or xff08;xff09; AddRoundKey步驟,回合金鑰將會與原矩陣合併。在每次的加密迴圈中,都會由主密鑰產生一把回合金鑰(透過Rijndael密鑰生成方案產生),這把金鑰大小會跟原矩陣一樣,以與原矩陣中每個對應的位元組作异或(⊕)加法。 AddRoundKey & #xff0c; the turn key will be merged with the original matrix. In each encryption loop & #xff0c; a turn key & #xff08 will be generated by the main key; & #xff09; & #xff0c will be generated through the Rijndael key generation program; the key size will be the same as the original matrix & #xff0c; it will be different from each corresponding byte in the original matrix or #xff08; #xff09; plus. 在SubBytes步骤中,矩陣中各字节被固定的8位查找表中对应的特定字节所替换,S;?bij?=?S(aij). In the SubBytes step & #xff0c; the bytes in the matrix were replaced by specific bytes corresponding to the fixed eight-bit search table S; bij?#61; S( aijxff09; . 在SubBytes步骤中,矩陣中的各字節透過一個8位元的S-box進行轉換。這個步驟提供了加密法非線性的變換能力。S-box與��(28)��(28)GF(28)上的乘法反元素有關,已知具有良好的非線性特性。為了避免簡單代數性質的攻擊,S-box結合了乘法反元素及一個可逆的仿射變換矩陣建構而成。此外在建構S-box時,刻意避開了不動點與反不動點,即以S-box替換字節的結果會相當於錯排的結果。Rijndael S-box條目有針對S-box的詳細描述。 In the SubBytes step & #xff0c; the bytes in the matrix are converted through an eight-bit S-box. This step provides the non-linear transformation of encryption. S-box and & #xfffffd; & & #xfffd; & #ffffd; 28) Multiplications on GF(28) are related to #xff0c; known to be good non-linear. In order to avoid a simple algebra attack xff0c; S-box combines the Multiplication Reverse element with a reversible analogue Reprogram. In addition, S-box S-box has a detailed description of S-box. 在ShiftRows步驟中,矩陣中每一列的各個位元組循環向左方位移。位移量則隨著列數遞增而遞增。 & #xff0c in the ShiftRows step; the loops of each bytes in each column in the matrix shift to the left. The number of columns increases with the number of columns. ShiftRows描述矩陣的行操作。在此步驟中,每一行都向左循環位移某個偏移量。在AES中(區塊大小128位元),第一行維持不變,第二行裡的每個位元組都向左循環移動一格。同理,第三行及第四行向左循環位移的偏移量就分別是2和3。128位元和192位元的區塊在此步驟的循環位移的模式相同。經過ShiftRows之後,矩陣中每一竖列,都是由輸入矩陣中的每個不同列中的元素組成。Rijndael演算法的版本中,偏移量和AES有少許不同;對於長度256位元的區塊,第一行仍然維持不變,第二行、第三行、第四行的偏移量分別是1位元組、2位元組、3位元組。除此之外,ShiftRows操作步驟在Rijndael和AES中完全相同。 ShiftRows describes the line of the matrix. In this step xff0c; each line moves a deviation to the left loop. In AES & #xff08; block size 128 bits & #xff09; & #xff0c; first row maintains xff0c; second rows each move a grid to the left cycle. The third and fourth row moves a deviation to the left loop are divided by 2 and 3. The 128-bit and 192-digit blocks move the same pattern. After ShiftRows & #xff0c; each column in the matrix #xff0c; each of the different columns in the matrix is divided into two and three. In the Rijndael and fourth rows, the deviations are different. 在MixColumns步驟中,每個直列都在modulo?�4+1�4+1x4+1之下,和一個固定多項式c(x)作乘法。 xff0c in the MixColumns step; each column is in Modulo? & #xfffd; 443; 1xfffd; 443; 1x4#43; xff0c under 1; and a fixed multi-line c(x) multiplication. 在MixColumns步骤,每一列的四個位元組透過线性变换互相結合。每一列的四個元素分別當作1,�,�2,�31,�,�2,�31,x,x2,x3的係數,合併即為��(28)��(28)GF(28)中的一個多項式,接著將此多項式和一個固定的多項式�(�)=3�3+�2+�+2�(�)=3�3+�2+�+2c(x)=3x3+x2+x+2在模�4+1�4+1x4+1下相乘。此步驟亦可視為Rijndael有限域之下的矩陣乘法。MixColumns函数接受4個位元組的輸入,輸出4個位元組,每一個輸入的位元組都會對輸出的四個位元組造成影響。因此ShiftRows和MixColumns兩步驟為這個密碼系統提供了擴散性。 In MixColumns Step xff0c; in each column the four bits of xff0c; in each row, the four bits of xfffffd; xffffffd; xffd; xffd; xffd; xffd; xffffd; xffffd; xffffd; xfffd; fffffd; xfffd; xffd; xffd; xffd; xffd; ffd; xffd; f; r; f; f; f; f; f; #f; #4; f; #4; f; #4; f; #4; #jff; #jff; #fff; #jfff; ###4; ##fff; #f/d; #f/d; d; #f/d; #4; #f/d; #d; #f/d; #f/d; #f/r; #4; #f/r; #4; #f/r; #f/r. # #4; #4; #r; #f/r; #f/r; #r; #r; #r; #r; # # # # # # # # #4; #4; #r. # # # # # # #r; #r; # #r. # # # # #r; # # # # # # # # # # # # # # # # # 以下條目有對MixColumns更加詳細的描述:Rijndael mix columns The following entries provide a more detailed description of MixColumns & #xff1a; Rijndael mix columns 使用32或更多位元定址的系統,可以事先對所有可能的輸入建立對應表,利用查表來實作SubBytes,ShiftRows和MixColumns步驟以達到加速的效果。這麼作需要產生4個表,每個表都有256個格子,一個格子記載32位元的輸出;約佔去4KB(4096位元組)記憶體空間,即每個表佔去1KB的記憶體空間。如此一來,在每個加密迴圈中,只需要查16次表,作12次32位元的XOR運算,以及AddRoundKey步驟中4次32位元XOR運算。若使用的平台記憶體空間不足4KB,也可以利用循環交換的方式一次查一個256格32位元的表。 The system using 32 or more bits of location & #xff0c; the ability to pre-empt the creation of , for all possible input; the use of checklists to implement SubBytes, SchiftRows and MixColumns steps to achieve acceleration effects. This requires four tables & #xff0c; each has 256 cells & #xff0c; one cell to record the output of 32 pieces & xff1b; approximately 4KB( 4096 units #xff09; memory space #xff0c; each table to take the memory space of 1KB. 然而,實際實作中應避免使用這樣的對應表,否則可能因為產生快取命中與否的差別而使旁道攻擊成為可能。 However, xff0c; in practice, this countermeasure xff0c should be avoided; otherwise it may be possible to make an off-the-road attack possible because of the difference between fast hits and no. 截至2006年,针对AES唯一的成功攻击是旁道攻击或社會工程學攻擊。美国国家安全局审核了所有的參與競選AES的最終入圍者(包括Rijndael),认为他們均能夠满足美国政府傳遞非機密文件的安全需要。2003年6月,美国政府宣布AES可以用于加密机密文件: As of 2006 xff0c; the only successful attack against AES was or socio-engineering attacks. The US National Security Agency reviewed all final entrants to the AES campaign xff08; including Rijndael) xff0c; thought that they were able to meet the security needs of the U.S. Government for the delivery of unofficially classified documents. June 2003 xff0c; the U.S. Government announced that AES could be used to encrypt classified documents xff1a; The design and strength of all key lengths of the AES algorithm(i.e., 128, 192 and 256)are sufficient to protect classified information up to the SECRET level. TOP SECRET information will require use of either the 192 or 256 key lengths. The implementation of AES in products intended to protect national security systems and/or information must be reviewed and certified by NSA prior to their acquisition and use. (譯:AES加密演算法(使用128,192,和256位元密鑰的版本)的安全性,在設計結構及密鑰的長度上俱已到達保護機密資訊的標準。最高機密資訊的傳遞,則至少需要192或256位元的密鑰長度。用以傳遞國家安全資訊的AES實作產品,必須先由國家安全局審核認證,方能被發放使用。) & #xff08; & & #xfff1a; AES encryption algorithm & #xff08; using 128, 192, and 256-bit versions of ) security & #xff0c; standards for protecting machine secret information have been reached in the length of the design structure and the key; transmission of top secret information & #xff0c; required at least 192 or 256-digit key lengths. AES-based products for transmitting state security information & #xff0c; must first be reviewed by the State Security Service for authentication #xff0c; should be released. #xff09; #xff09; 这标志着,由美国国家安全局NSA批准在最高机密資訊上使用的加密系統首次可以被公開使用。许多大众化产品只使用128位元密鑰當作預設值;由於最高機密文件的加密系統必須保證數十年以上的安全性,故推測NSA可能認為128位元太短,才以更長的密鑰長度為最高機密的加密保留了安全空間。 This marks xff0c; for the first time, the encryption system approved by the National Security Service (NSA) for top secret information is publicly available. Many popular products use 128-bit keys as default value xff1b; since encryption systems for top secret files must guarantee security xff0c for more than a decade; so it is assumed that the NSA may think 128-bits are too short xff0c; and it retains security space with longer secret key lengths as top secret encryption. 通常破解一個區塊加密系統最常見的方式,是先對其較弱版本(加密迴圈次數較少)嘗試各種攻擊。AES中128位元密鑰版本有10個加密迴圈,192位元密鑰版本有12個加密迴圈,256位元密鑰版本則有14個加密迴圈。至2006年為止,最著名的攻擊是針對AES 7次加密迴圈的128位元密鑰版本,8次加密迴圈的192位元密鑰版本,和9次加密迴圈的256位元密鑰版本所作的攻擊。 The most common way to decipher a block encryption system is xff0c; the weaker version xff08; the smaller number of encrypt loops xff09; trying attacks. The 128-bit version of AES has 10 encryption loops xff0c; the 192-bit version has 12 encryption loops xff0c; the 256-digit version has 14 encryption loops. Until 2006 xff0c; the most famous attack was the 128-bit key version xff0c; the 192-digit key version #xff0c of 8 encryption loops; and the 256-digit key version of 9 encryption loops. 由於已遭破解的弱版的AES,其加密迴圈數和原本的加密迴圈數相差無幾,有些密碼學家開始擔心AES的安全性:要是有人能將該著名的攻擊加以改進,這個區塊加密系統就會被破解。在密碼學的意義上,只要存在一個方法,比窮舉法還要更有效率,就能被視為一種「破解」。故一個針對AES 128位元密鑰的攻擊若「只」需要2120計算複雜度(少於窮舉法2128),128位元密鑰的AES就算被破解了;即便該方法在目前還不實用。從應用的角度來看,這種程度的破解依然太不切實際。最著名的暴力攻擊法是distributed.net針對64位元密鑰RC5所作的攻擊。 AES,, a weak version of which has been broken; its cryptographic loops are very different from the original encryption loops; some cryptographers are beginning to worry about AES' safety & #xff1a; if someone can change the famous attack into xff0c; the cryptographic system is broken. In the meaning of cryptology xff0c; as long as a method xff0c exists, it is more efficient than > 其他的爭議則著重於AES的數學結構。不像其他區塊加密系統,AES具有相當井然有序的代數結構。雖然相關的代數攻擊尚未出現,但有許多學者認為,把安全性建立於未經透徹研究過的結構上是有風險的。Ferguson,Schroeppel和Whiting因此寫道:「...我們很擔心Rijndael演算法應用在機密系統上的安全性。」 Other disputes focus on AES’s mathematical structure. Unlike other block encryption systems & #xff0c; AES has a rather orderly algebraic structure. Although the associated algebra attacks have not yet appeared & #xff0c; many scholars believe that , creating security in unresearched structures is risky. Ferguson, Schroepel and Whiping write #xff1a; “... we are very concerned about the security that Rijndael algorithms should use in the system.” 2002年,Nicolas Courtois和Josef Pieprzyk發表名為XSL攻擊的理論性攻擊,試圖展示AES一個潛在的弱點。但該攻擊的數學分析有點問題,推測應是作者的計算有誤。因此,這種攻擊法是否對AES奏效,仍是未解之謎。就現階段而言,XSL攻擊AES的效果不十分顯著,故將之應用於實際情況的可能性並不高。 xff0c; Nicolas Courtois and Josef Pieprzyk published the theoretical attack xff0c; tried to show AES a potential weakness. But the mathematical analysis of the attack was problematic xff0c; the assumption was that the author had miscalculated. xff0c; therefore, whether the attack had worked for AES xff0c; it was still a mystery. In the present context xff0c; the effect of the XSL attack on AES was not very obvious xff0c; so the likelihood of applying it to the actual situation was not high. 旁道攻击,又称旁路攻击、侧信道攻击,是一种基于从密码系统的物理实现中获取的信息的攻击方式。它不攻击加密算法本身,而是攻击那些基於不安全系統(會在不經意間洩漏資訊)上的加密系統。 2005年4月,D.J. Bernstein公佈了一种缓存时序攻击法,他以此破解了一个装载OpenSSL?AES加密系統的客戶伺服器。為了設計使該伺服器公佈所有的時序資訊,攻击算法使用了2亿多条筛选过的明码。对于需要多个跳跃的国际互联网而言,这样的攻击方法并不实用。Bruce Schneier稱此攻擊為「好的時序攻擊法」。 xff0c; April 2005 xff0c; D.J. Bernstein published a cache time-series attack method xff0c; he deciphered OpenSSL? AES encryption system client server designed to make the server publicly available all time-series information xff0c; attack algorithms used more than 200 million filtered codes. For multiple jumps over the international Internet xff0c; such attacks are not practical. 2005年10月,Eran Tromer?(页面存档备份,存于)和另外兩個研究員發表了一篇論文,展示了數種針對AES的緩存時序攻擊法。 October 2005 xff0c; Eran Tromer?(
This article is issued from?Wikipedia. The text is licensed under?Creative Commons - Attribution - Sharealike. Additional terms may apply for the media files.
注册有任何问题请添加
微信:MVIP619
拉你进入群
打开微信扫一扫 添加客服 进入交流群 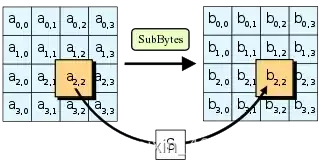
概述 设计者 Vincent Rijmen、Joan Daemen 首次发布 1998年 衍生自 Square 继承算法 Anubis、Grand Cru、Kalyna 密码细节 密钥长度 128、192或者256位元 分组长度 128位元 结构 置換排列網絡 重复回数 10, 12或14(視密鑰長度而定) 最佳公开破解 關聯密碼攻擊可以破解9個加密迴圈/256位元(密鑰)的AES。另外選擇明文攻擊可以破解8個加密迴圈,192或256位元(密鑰)的AES,或7個加密迴圈、128位元(密鑰)的AES。(Ferguson?et al., 2000) AddRoundKey步骤
SubBytes步骤
ShiftRows步骤

MixColumns步骤
加密演算法优化
旁道攻击
引用
书目
实现

1.本站遵循行业规范,任何转载的稿件都会明确标注作者和来源;2.本站的原创文章,请转载时务必注明文章作者和来源,不尊重原创的行为我们将追究责任;3.作者投稿可能会经我们编辑修改或补充。












